In cybersecurity, anticipating an adversary’s moves before they strike is a master strategy. Red teaming is such a proactive security approach where experts simulate real-world attacks. This is done to test and exploit any possible loopholes in your organization’s defences and assess the response capabilities.
Red teamers, as they are often called, need the right tools to execute. There are open-source and commercial red team tools that are shaping modern red teaming operations. These red team security tools help organizations find blind spots before cyber attackers do.
Understanding Red Teaming
Red teaming involves a highly efficient team of security experts, authorized by an organization, to conduct a simulated attack on a specific system. They emulate an attacker’s exploitation capabilities against your IT security posture. This may sound like penetration testing, but it is not.
Red teaming has a wider scope. It mimics real threat actors, combining digital, physical and social engineering tactics. This realistic threat simulation identifies how deep attackers can go undetected. Plus, it unveils existing vulnerabilities and exposures. Red teamers use these outcomes to demonstrate how effective the defence and response capabilities of the organization is.
Explore our comprehensive blog – Red Teaming Guide – to learn more about this security approach.
What are Red Team Tools?
Red team tools are software used to emulate the tactics, techniques and procedures (TTPs) of real-world adversaries. Now the use of red team security tools varies depending on the specific organization’s attack surface and industry-focused threats. Based on the needs, a customized red teaming attack model is devised. For example, red team security tools and models used for a BFSI company may not be applicable for a healthcare setup.
These tools help red teamers to plan, launch and manage complex attack scenarios. Plus, they are used across the red teaming stages such as reconnaissance, exploitation, lateral movement, privilege escalation and exfiltration.
There are many open-source tools available on the web, and they are effective. At the same time, there are commercial ones with better capabilities and features. What your business needs will depend on the SOC team’s strength, budget, as well as C-suite decisions.
Open-Source Red Team Tools
Here are some of the widely adopted open-source red team tools in 2026:
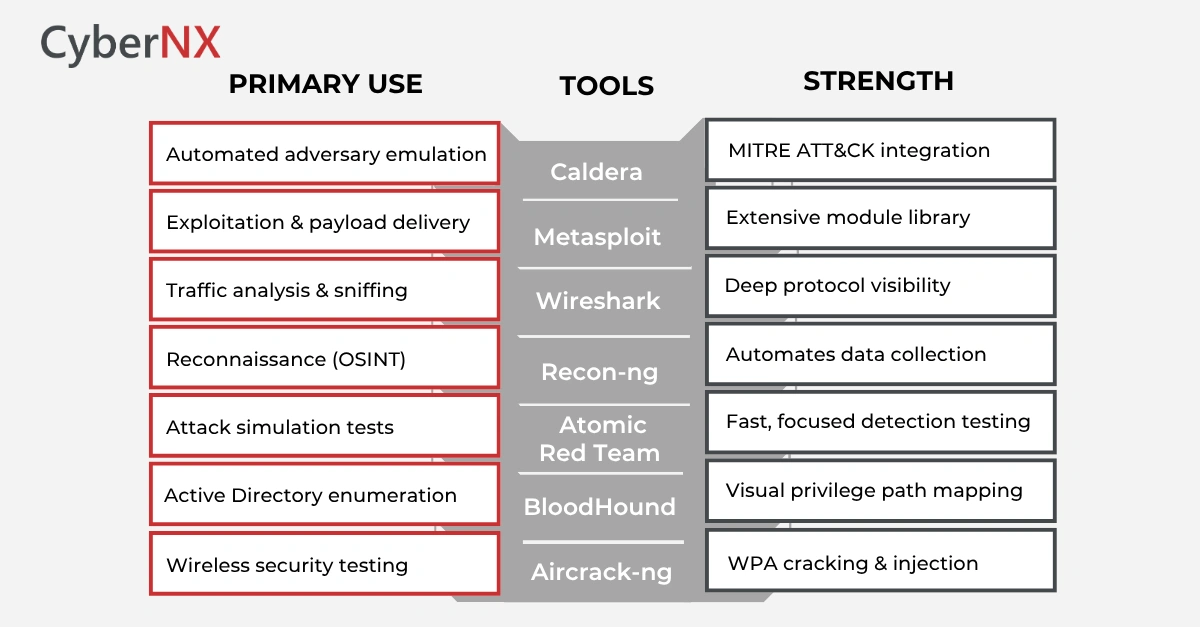
1. Caldera
Caldera is developed by MITRE, and it is known for automating adversary emulation by using real-world TTPs from the highly effective MITRE ATT&CK framework. It is a powerful platform in the hands of a red team, helping them to simulate full-scale attacks while also tracking defence capabilities.
2. Metasploit Framework
A trusted, must-have in the red team toolkit for a long time, Metasploit is mainly an exploitation framework. It is used to probe and validate discovered vulnerabilities.
The vast library of payloads and modules it possesses makes it suitable for testing enterprise systems.
3. Wireshark
Another traditionally used red teaming tool, Wireshark is used as a packet analyser. It is critical during red team operations for sniffing traffic, analysing communications and identifying network weaknesses during or post-exploitation stages.
4. Recon-ng
This web reconnaissance red teaming tool simplifies open-source intelligence (OSINT) gathering. Additionally, it automates data collection across platforms like LinkedIn, GitHub and search engines.
5. Atomic Red Team
This one also developed by MITRE, provides small, focused tests mapped to ATT&CK techniques. It is used for validating the detection coverage and testing specific security controls.
6. BloodHound
BloodHound is a graph-based analysis tool. It essentially identifies privilege escalation paths in Active Directory environments and helps red teams understand how attackers traverse a network in a specific environment.
7. Aircrack-ng
Essential for wireless network testing, Aircrack-ng helps assess WPA/WPA2-PSK networks through packet capture, cracking and injection techniques.
Open-Source Red Team Tools Comparison Chart
This chart gives you a quick look at the top free red team security tools.
Commercial Red Team Tools
Usually, those organizations with mature security and a mature SOC team invest in commercial red team security tools to extend capabilities, support and integrations.
1. Cobalt Strike
Everyone has a favourite, right? Cobalt Strike is the most sought-after tool among red teamers. It offers post-exploitation capabilities such as beaconing, command and control and pivoting through compromised systems.
2. CrowdStrike Falcon
Let’s be very clear: CrowdStrike Falcon is primarily an endpoint detection and response (EDR) tool. But its adversary emulation features allow red teams to simulate advanced attacks and test how well the EDR responds.
3. Verodin (now Mandiant Security Validation)
Verodin is another commercial red team tool that validates the effectiveness of security controls. It is achieved by simulating known attacks and measuring actual outcomes, thus providing quantifiable metrics related to defensive stack used in the organization.
4. AttackIQ
This platform with scenarios mapped to MITRE ATT&CK helps red teams operationalize threat-informed defence. It is helpful in validating detections, improving response and providing board-level insights.
Commercial Red Team Tools Comparison Chart
This chart gives you a quick look at the top commercial red team tools.
| TOOL | FOCUS AREA | UNIQUE EDGE |
| Cobalt Strike | Post-exploitation framework | Covert command & control features |
| CrowdStrike Falcon | Adversary simulation in EDR | Real-time endpoint testing |
| Verodin (Mandiant SV) | Control validation | Security efficacy measurements |
| AttackIQ | Threat emulation platform | MITRE ATT&CK-aligned scenarios |
Conclusion
The red team tool you choose should align with your organization’s goals. Open-source tools offer flexibility and community support whereas commercial platforms offer scale, automation and reporting capabilities. The right tool will make your testing smarter, faster and impactful.
Our red teaming services help businesses build resilient cybersecurity programs through advanced threat simulation and continuous testing. Contact us today.
Red Team Tool FAQs
How do I choose between open source and commercial red team tools for my organization?
Choosing between open source and commercial tools depends on your team’s maturity, budget, and operational goals. Open-source tools offer flexibility and community support, making them ideal for skilled in-house teams. Commercial tools come with support, integrations, and dashboards – better suited for enterprises needing scalability, compliance reporting, and faster deployment.
Can red team tools be used by internal security teams, or are they only for external consultants?
Absolutely, internal security teams can and should use red team security tools. Internal red teams, also known as purple teams when working closely with blue teams, use these tools to simulate realistic threats, improve detection, and continuously assess the effectiveness of their defences – without relying solely on third-party engagements.
Are red team tools legal to use in any environment?
Red team security tools are legal only when used in authorized environments with explicit consent. Using these tools without permission – even for “testing” a public-facing app – can be considered illegal hacking. Always operate within a defined scope and under proper legal frameworks, such as rules of engagement and non-disclosure agreements.
How often should red team security tools be used in a cybersecurity program?
Red team security tools aren’t just for annual security assessments anymore. With the rise of continuous security validation, many organizations use them monthly or even weekly to test controls, validate detection, and adapt defences in real time. The frequency depends on your threat landscape, regulatory needs, and risk tolerance.