Depending on the organizational risks, IT Managers constantly seek innovative strategies to fortify their defences. Red teaming and Blue teaming are traditionally seen as an effective strategy. However, they operated in silos.
The emergence of purple team cybersecurity strategy is revolutionizing how organizations approach security testing and improvement. It strikes the right balance between offensive and defensive security approach. This blog will delve into the intricacies of purple teaming, exploring its definition, benefits and practical applications.
What is Purple Teaming in Cybersecurity?
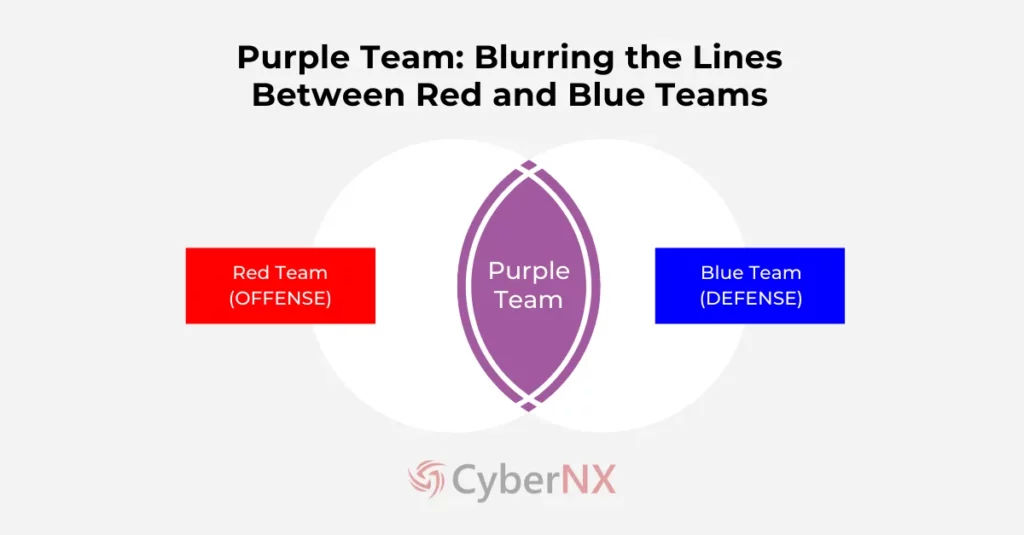
Purple team cybersecurity strategy is a collaborative approach that breaks down the barriers between red and blue teams. It involves real-time interaction and knowledge sharing to enhance an organization’s security posture.
Definition
A purple team is a group of security professionals who facilitate collaboration between red and blue teams during security assessments and exercises.
Role & Responsibility
They act as a bridge, ensuring that the blue team learns from the red team’s attack simulations and vice versa. This collaborative approach leads to a better understanding of how attacks are executed and how to effectively defend against them.
Purple Team Structure
A purple team is not a separate, distinct team, but rather a methodology. It involves members from both the red and blue teams working together, often with a facilitator to guide the process.
Objectives
The primary objective is to improve the organization’s security posture by enhancing threat detection, incident response, and overall security awareness.
Tools
Purple team tools unify offensive and defensive operations by simulating attacks to validate and tune security controls in real-time. Platforms like Atomic Red Team and SCYTHE emulate specific threat tactics, allowing teams to immediately verify if their defences catch the activity.
How Does the Purple Team Work?
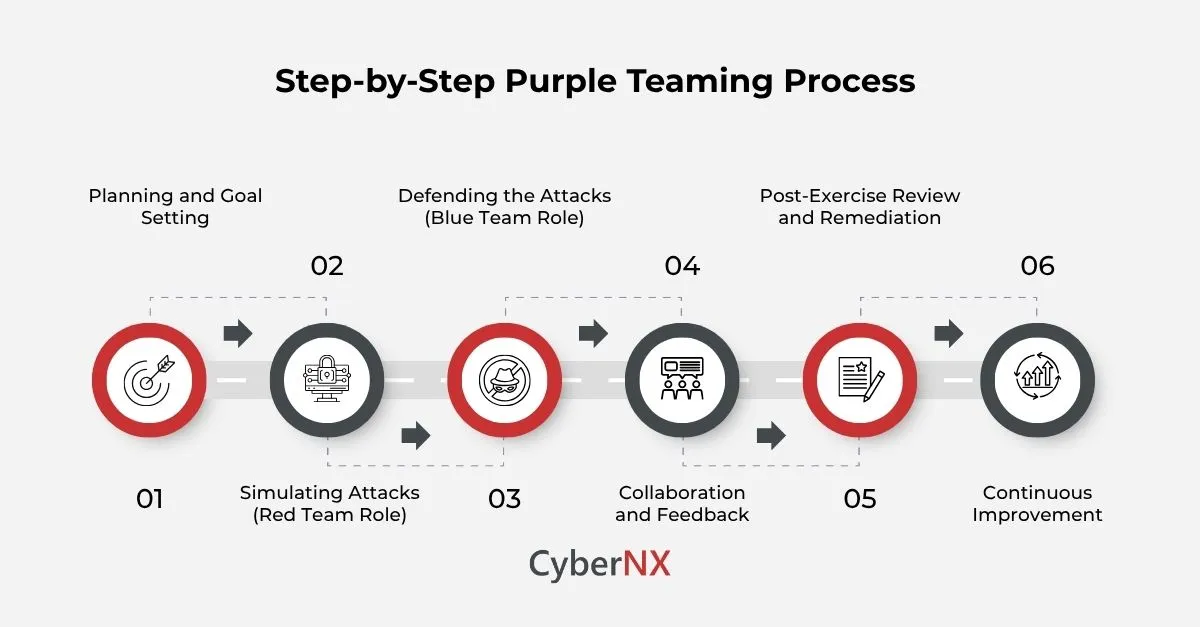
Purple team assessment and purple team exercises follow a structured process to maximize effectiveness.
- Step 1: Planning and Goal Setting: Define the scope and objectives of the exercise.
- Step 2: Simulating Attacks (Red Team Role): The red team performs simulated attacks, emulating real-world threat actors.
- Step 3: Defending the Attacks (Blue Team Role): The blue team monitors and responds to the simulated attacks.
- Step 4: Collaboration and Feedback: Real-time communication and knowledge sharing between the red and blue teams.
- Step 5: Post-Exercise Review and Remediation: Analyze the results and implement necessary security improvements.
- Step 6: Continuous Improvement: Integrate lessons learned into ongoing security practices.
Challenges Faced by the Purple Team
While purple team cybersecurity strategy offers significant advantages, it’s not without its challenges. Overcoming these hurdles is essential for maximizing the effectiveness of your security efforts.
- Real-Time Collaboration: Maintaining consistent, effective communication between red and blue teams.
- Accurate Simulations: Ensuring attack simulations reflect current, real-world threats.
- Knowledge Bridging: Overcoming skill and perspective gaps between red and blue team members.
- Effective Documentation: Properly recording and sharing exercise findings for actionable insights.
- Threat Relevance: Keeping exercises updated with new and emerging cyber threats.
- Executive Buy-In: Securing leadership support and resources for this team activities.
What Skills Are Required for Purple Team Exercises?
Purple Team exercises demand a blend of offensive (Red Team) and defensive (Blue Team) expertise, along with strong communication and analytical skills. Understanding adversary tactics, detection engineering, and real-time collaboration is key to maximizing their effectiveness.
- Technical Expertise: Proficiency in penetration testing, network security, and incident response.
- Collaboration Skills: Ability to work effectively with others and share knowledge.
- Problem-Solving: Analytical skills to identify and resolve security issues.
- Threat Intelligence: Understanding of current and emerging threats.
- Communication: Clear and effective communication skills.
Red Team vs Blue Team vs Purple Team
To truly understand the value of purple teaming, it’s essential to differentiate it from its red and blue team counterparts. In essence:
| Aspects | Red Team | Blue Team | Purple Team |
| Primary Role | Offensive security testing. | Defensive security monitoring. | Facilitate collaboration. |
| Main Objective | Identify vulnerabilities. | Detect and respond to threats. | Enhance overall security posture. |
| Scope of Work | Simulated attacks. | Monitoring and incident response. | Collaborative exercises and assessments. |
| Focus | Exploiting weaknesses. | Defending against attacks. | Real-time collaboration and knowledge sharing. |
| Approach | Proactive, offensive. | Reactive and proactive, defensive. | Collaborative, iterative. |
| Collaboration | Limited, focused on results. | Continuous, internal. | Extensive, real-time. |
| Tools & Techniques | Penetration testing tools, exploits. | SIEM, IDS/IPS, EDR. | Shared platforms, communication tools. |
| Outcome | Vulnerability reports. | Incident response and remediation. | Improved security controls and awareness. |
We have explored in-depth about these practices in our blog Red Team vs Blue Team vs Purple Team. Read now!
Benefits of Purple Team Cybersecurity Strategy
What value does purple team in security add to companies? Purple Teaming enhances security by fostering real-time collaboration between attackers and defenders, turning simulations into shared learning opportunities. It accelerates detection tuning, improves incident response, and builds a more cohesive, threat-aware security culture.
- Strengthened Security: Improved threat detection and incident response capabilities.
- Rapid Incident Response: Faster mitigation through real-time team collaboration.
- Enhanced Preparedness: Realistic attack simulations for better defense readiness.
- Risk Mitigation & Compliance: Demonstrates proactive security for regulatory needs.
- Continuous Security Evolution: Ongoing improvements through consistent feedback.
Conclusion
Purple teaming cybersecurity strategy stands as a pivotal advancement, fostering collaboration and continuous improvement. By dismantling the traditional silos between red and blue teams, organizations can build dynamically resilient security posture.
Real-time knowledge sharing allows for immediate refinement of defenses, ensuring you stay ahead of evolving threats. This collaborative approach, however, relies on the foundational expertise of both red and blue teams.
If you want to improve how your teams work together to detect and respond to real threats, purple teaming is a strong next step. It brings offensive and defensive experts into one focused exercise. This helps you uncover gaps, tune detections and strengthen your overall security posture.
Ready to build better collaboration between your red and blue teams? Explore our purple teaming services to see how we help organisations test attacks, validate defences and drive continuous improvement.
Purple Team FAQs
How does purple teaming differ from traditional penetration testing?
Traditional penetration testing, often conducted by a red team, focuses on finding vulnerabilities. Purple teaming goes further by facilitating real-time interaction between the red and blue teams. This allows for immediate knowledge transfer, improved defense strategies, and continuous security enhancement, far beyond a report.
How often should we conduct purple team exercises?
The frequency depends on your organization’s risk profile and the complexity of your environment. However, regular exercises, such as quarterly or semi-annually, are recommended to keep your security defenses sharp and up-to-date with emerging threats.
What tools are essential for a successful purple team exercise?
Essential tools include those for penetration testing (e.g., Metasploit, Nmap), SIEM systems (e.g., Splunk, ELK Stack), and collaborative communication platforms (e.g., Slack, Microsoft Teams). Also, tools that allow for attack simulation and attack emulations are very helpful.
How does purple teaming help with compliance?
Purple teaming demonstrates a proactive approach to security, which can be valuable for meeting compliance requirements like PCI DSS, HIPAA, and GDPR. It shows that your organization is actively testing and improving its security controls.
Can purple teaming be automated?
While full automation is challenging due to the need for real-time collaboration, aspects of purple teaming can be automated. For example, attack simulations and log analysis can be automated, allowing teams to focus on strategic collaboration and knowledge sharing.
What are the key metrics to measure the success of a purple team exercise?
Key metrics include the number of vulnerabilities identified and remediated, the time taken to detect and respond to simulated attacks, improvements in threat detection rules, and enhanced incident response playbooks. Also, the level of collaboration and knowledge transfer between teams can be measured.