A 2024 report revealed something on the expected lines: 60% of organizations have faced physical security breaches in the past five years.
When most people think of cybersecurity, they picture firewalls, antivirus software, and maybe a shady figure in a hoodie tapping away at a keyboard. What often gets overlooked? The physical facilities which could be breached, leading to theft and property destruction.
Welcome to Physical Red Teaming – a lesser-known but increasingly critical part of modern security. It’s where the digital world meets the real one, and where organizations find out if they’re physically as secure as they think they are.
What is Physical Red Teaming?
Physical red teaming involves attempting to enter offices, sensitive spaces and no-entry areas in an organization. When you opt for physical red teams, you are literally hiring ethical intruders and authorizing them to break into your building.
Red teamers often try to bypass security guards, sneak past badge readers and get to your sensitive areas. That’s physical red teaming in a nutshell.
It’s a controlled simulation designed to test how well your physical security holds up against real-world threats.
Why Physical Red Teams Matter More than Ever?
With all the buzz around cybersecurity, it’s easy to forget that attackers don’t only go through computers. They go through doors, windows, loading docks, and-yes-even fake uniforms.
Here’s why physical red teaming should be on every organization’s radar:
1. It Tests the Human Element
No matter how many systems you lock down, there’s always a person in the loop. People can be tricked-into holding a door open, ignoring a bypassed badge reader, or mistaking a stranger for an employee.
2. It Identifies Real-World Weaknesses
Cameras not monitored. Doors propped open. Server rooms unlocked. These issues don’t show up in a network scan, but they’re glaring vulnerabilities in the real world.
3. It Trains Your Team, Not Just Your Tech
Once a red team completes its mission, the real value comes in the debrief. It’s a wake-up call for everyone-security, facilities, even HR. You can’t improve what you don’t know is broken.
Benefits of Physical Red Teaming
Putting your organization through a simulated physical breach can unlock value:
- Proactive defence expose vulnerabilities before real attackers do.
- Staff training under realistic pressure not theoretical classroom lessons.
- Regulatory and compliance support, especially in sectors that require physical security audits.
- Risk prioritization so that you know what to fix first.
- Stronger brand reputation can be achieved as customers and stakeholders see you take security seriously.
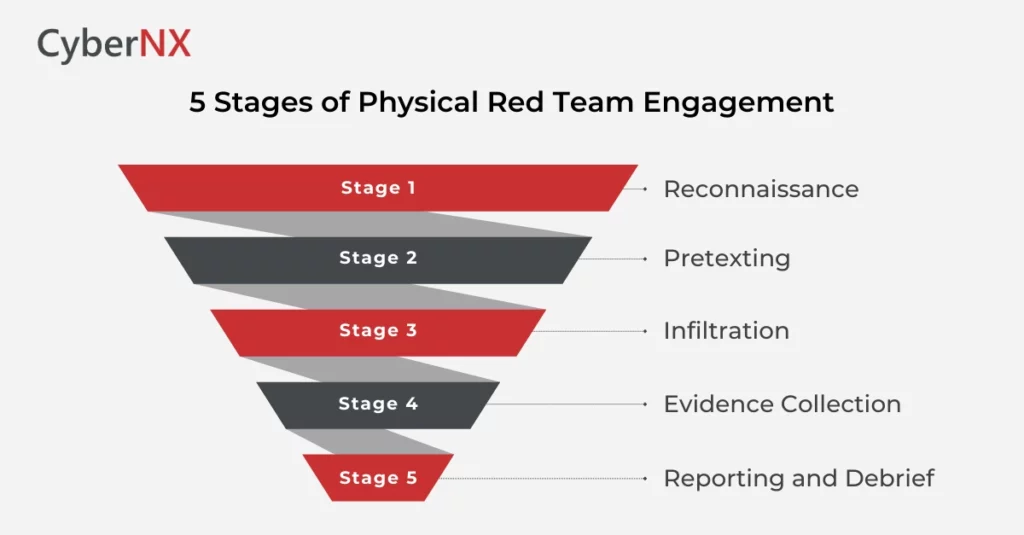
What Happens During a Physical Red Team Engagement?
Every operation is customized, but here’s a peek behind the curtain:
1. Reconnaissance
Before even stepping on-site, red teamers gather information-shift timings, dress codes, access points, social media clues. You’d be surprised what they can learn just by watching from a coffee shop nearby.
2. Pretexting
This is where creativity shines. Red teamers may pose as delivery personnel, maintenance staff, or even job candidates. The goal is to blend in and gain access.
3. Infiltration
Using social engineering, stealth, and sometimes lockpicking (yes, really), they attempt to reach target zones-like data centres, executive offices, or employee workstations.
4. Evidence Collection
Instead of stealing data, they collect proof of access-photos, timestamps, or mock “payloads”—to show what could have been compromised in a real attack.
5. Reporting and Debrief
Finally, the red team lays it all out: what worked, what didn’t, and what the organization needs to fix. No judgment-just facts and fixes.
Common Weaknesses Found (and How to Fix Them)
Some of the most successful intrusions happen due to surprisingly simple oversights:
| Weaknesses | Specific Failures | Suggested Fixes |
| Access Control Gaps | Unlocked sensitive doors, badge systems without fallback, single-factor entry | Enforce multi-factor physical access, mantraps, access lockdown schedules |
| Human Error / Social Engineering | Staff hold doors, fail to verify identity, assume people belong | Security awareness programs, regular drills, verification policies |
| Visitor / Vendor Management Flaws | Loose guest check-in, unverified contractors, weak escort rules | Centralized visitor systems, IDs for contractors, escort procedures |
| Over-reliance on CCTV | Cameras installed but not actively monitored or responded to | Real-time monitoring, alarm integration, regular reviews |
| Tailgating / Piggybacking | Unauthorized persons following authorized staff through doors | Turnstiles, anti-tailgate sensors, employee awareness |
Who Needs Physical Red Teaming?
If you’re in finance, healthcare, energy, IT, or any sector handling critical infrastructure or personal data-you need physical red teaming. Regulatory compliance is one reason. Protecting reputation, assets, and people is another.
Even tech-savvy firms often discover during a red team exercise that their most secure systems could be compromised by someone walking in through an unattended back door.
Physical Security is Cybersecurity
We have spent years separating “cyber” from “physical.” But attackers don’t care about categories, they care about access.
Physical red teaming bridges the gap, revealing how an intruder might pivot from your lobby to your servers, or from a breakroom to your boardroom. It shows that real-world intrusions aren’t just possible, they are sometimes easier than remote ones.
Need Expert Eyes? CyberNX can Help
If you’re ready to find out where your blind spots are – before someone else does – CyberNX can help. Our experienced red team professionals simulate real-world attacks with precision, ethics, and discretion. We test, report, and guide you through securing the physical side of your cybersecurity posture.
Want to know how our red team engagement would work for your organization? Reach out to CyberNX.
Physical Red Teaming FAQs
How is physical red teaming different from a regular security audit?
A security audit typically reviews policies, procedures, and documentation to ensure compliance, while physical red teaming is an active, hands-on simulation of real-world intrusion attempts. Instead of checking if rules exist, it tests whether they work under pressure.
Can physical red teaming be combined with cyber red teaming?
Yes. Many organizations run hybrid engagements where physical and digital attacks happen in parallel. For example, an intruder might enter the premises physically to plug a rogue device into the network, enabling cyber compromise from inside.
Will my staff know a red team test is happening?
In most cases, only a few key decision-makers are informed in advance. Keeping employees unaware ensures authentic reactions and provides a more accurate picture of real-world readiness.
What happens if red teamers are caught during the exercise?
Professional red teamers always carry authorization letters and follow pre-agreed safety protocols. If caught, they immediately identify themselves and pause the exercise to avoid conflict or misunderstanding.