Penetration testing phases provide a window into how your IT environment can be breached, how quickly attackers can move and how deeply they can penetrate before detection.
Knowledge about these phases thus becomes essential to managing business risk.
Suppose you are testing a new cloud deployment, evaluating compliance posture or assessing overall cyber hygiene. When you know what happens at each stage, you are better equipped to allocate resources, demand clearer outcomes and ensure your organization’s defences are resilient.
In short, knowing the penetration testing phases allows you to validate the effectiveness of your security program, step by step.
What is a Pen Test?
A pen test is a structured, controlled and authorized simulation of real-world attacks to identify vulnerabilities within your IT systems, networks and applications.
Pentesters get into the shoes of a malicious actor to exploit weaknesses and to access sensitive data, disrupt operations or move laterally through your IT environment.
Penetration tests are usually conducted using three approaches.
Black Box, where the tester has no prior knowledge of the system, mimicking an external attacker. Then there is White Box, where full internal access is granted to simulate insider threats or deep code-level vulnerabilities. Finally, Grey Box, a combined approach that reflects partial knowledge, ideal for realistic attack scenarios.
It is important to know that each method serves different business goals. From perimeter assessment to internal trust verification, opting the right one depends on your risk tolerance and compliance requirements.
Penetration Testing Phases: From 3 to 7 Stages
Testing methodologies vary. But most pentesting phases engagements follow a phased structure.
Depending on the depth and scope, there could be three, five, or seven clearly defined penetration testing phases.
1. 3 Phases of Penetration Testing
- Planning & Scoping
- Attack Execution
- Reporting & Debrief
2. 5 Phases of Penetration Testing (Industry Standard)
- Reconnaissance
- Scanning & Enumeration
- Exploitation
- Post-Exploitation
- Reporting
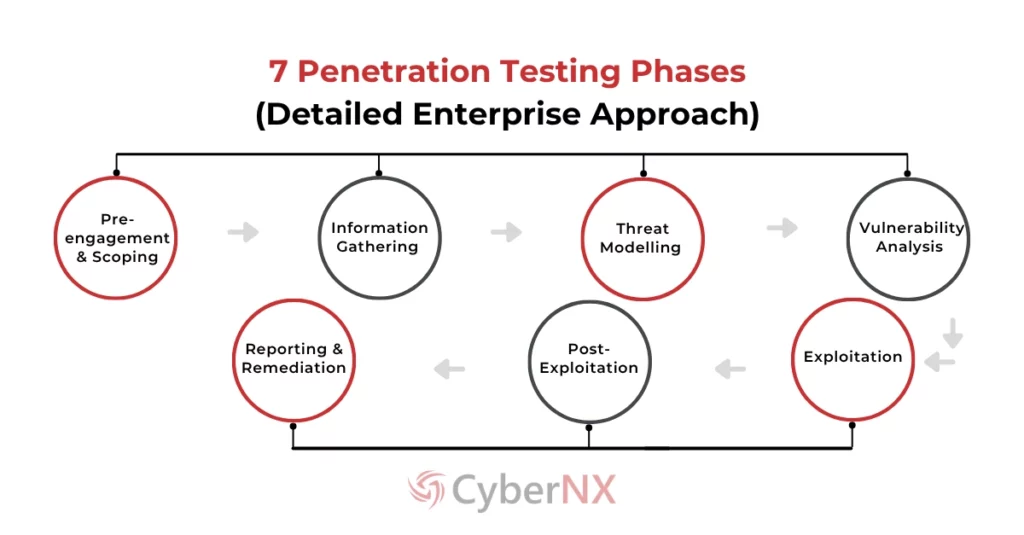
3. 7 Phases of Penetration Testing (Detailed Enterprise Approach)
- Pre-engagement & Scoping
- Information Gathering
- Threat Modelling
- Vulnerability Analysis
- Exploitation
- Post-Exploitation
- Reporting & Remediation
Each pentest phases helps in understanding how an attacker could infiltrate, pivot and impact your organization, providing a crystal-clear security view beyond raw vulnerability data.
Steps Involved & Tools Used in Penetration Testing Phases
A strong pentest process involves meticulous execution across phases. Every step taken simulates attacker behaviour but also provides actionable insights aligned with real-world business risk.
Below, you will find details about each of the pentest phases, enriched with real use cases, advanced techniques and the tools that power them.
1. Pre-engagement & Scoping
This phase involves defining the goal plus establishing technical and legal boundaries. The test objective could be regulatory (PCI DSS, HIPAA), risk validation or post-incident review.
Key Considerations:
- Will the test include social engineering?
- Are production systems in scope?
- Is testing during business hours acceptable?
Tools:
- Project Management: Jira, Trello, Notion
- Legal Forms: Scope matrix, authorization letters
- Collaboration: Secure Slack channels, Signal for urgent alerts
Scoping reduces liability and enables businesses to maximize ROI by aligning priorities with technical depth.
2. Information Gathering (Reconnaissance)
In this step, pentesters begin the real work, mimicking what an attacker would uncover without breaching a system. It’s divided into:
Passive Recon
Collects open-source intelligence (OSINT) without interacting with targets. Includes accessing public information via social media scraping, data leaks and historical DNS records.
Active Recon
Engages with systems directly to identify IPs, domains and attack surfaces.
Tools Used
- Passive: Maltego, TheHarvester, IntelligenceX
- Active: Nmap, Shodan, Amass
This helps discover forgotten assets which are vulnerable like staging servers and legacy systems.
3. Threat Modelling
This is a strategic penetration testing phase because it involves mapping what was found to known attacker techniques. It focuses on what to target based on potential business impact, not just technical severity.
Approach:
- Creating threat attacker personas (e.g., ransomware operator vs insider threat)
- Creating model attack paths using real MITRE ATT&CK TTPs (Tactics, Techniques, and Procedures)
Tools used:
So, what it does? Saves time on low-impact issues and focuses on breach-critical paths.
4. Scanning & Vulnerability Analysis
In this phase, pentesters probe the environment to identify weaknesses using manual and automated methods.
Types of Scans:
- Port & Service Scanning: Identifies open services such as HTTP, SMB, SSH
- Banner Grabbing: Determines software versions for vulnerability matching
- Config Review: Examines default credentials and misconfigurations
Tools:
- Network: Nmap, Masscan
- Vulnerability: Nessus, Qualys
- Web: Burp Suite, OWASP ZAP
This is the stage where technical groundwork for successful exploitation is done and helps validate risk exposure related to real assets.
5. Exploitation
As the name indicates, pentesters exploit the found vulnerabilities to breach the system, but without damaging data or services. The aim is to create proof of concept and not disruption in this pen test phase.
Tactics Used:
- Authentication bypass for default credentials and logic flaws
- Command injection to execute unauthorized commands
- Remote code execution (RCE) for full system compromise
- Social engineering to target employees
Tools:
- Exploitation Frameworks: Metasploit, Cobalt Strike, ExploitDB
- Manual Tools: SQLmap, XSS Hunter
Technical flaws are converted into tangible risks in this phase.
6. Post-Exploitation
Once access is gained, pentesters measure how deep and wide an attacker could go. Also, focus shifts from “getting in” to “what can be done once inside.”
Activities Include:
- Privilege escalation
- Credential dumping
- Lateral movement
- Data exfiltration simulation
Tools:
- Windows Tools: Mimikatz, BloodHound
- Linux Tools: LinPEAS, Linux Exploit Suggester
- Payloads: C2 frameworks like Covenant or Empire
It basically measures how long a breach could go undetected and what data could realistically be stolen.
7. Reporting & Remediation
This is the last penetration testing phase, where findings are converted into actionable intelligence. Comprehensive and easy to understand reporting makes a business case for stronger security posture.
Contents:
- Executive Summary showcasing risk overview and impact assessment
- Technical Detail like exploits used, entry points and affected systems
- Screenshots & Logs for proof of compromise
- Remediation Roadmap which includes steps, prioritisation and effort estimates
Executives should expect a debrief meeting, not just a report handover, where findings are aligned with business impact and mitigation timelines.
We have previously written an in-depth piece on reports. Read now: How to Read and Leverage Penetration Testing Report.
Common Mistakes in Penetration Testing Phases
Many organizations underestimate how these oversights compromise the value of penetration testing. Skipping phases, over-automating, or neglecting remediation guidance results in superficial assessments that fail to reflect real-world threats. Effective testing demands clarity across all phases of a penetration test, completeness and a focus on outcomes that reduce actual business risk.
- Vague scoping: Leads to missed risks or legal issues.
- Insufficient reconnaissance: Misses shadow IT or misconfigured endpoints.
- Relying only on tools: Business logic flaws often require manual testing.
- No post-exploitation simulation: Limits understanding of breach depth.
- Report-only delivery: Lack of remediation follow-through means issues remain unresolved.
Penetration Testing Phases: Timeline
Timelines of penetration testing phases will vary based on project size and complexity. Here’s a generally followed structure for you to have a look:
- Week 1: Scoping & Reconnaissance
- Week 2: Scanning & Analysis
- Week 3: Exploitation & Post-Exploitation
- Week 4: Reporting & Review
In regulated environments, timeline may extend to 6–8-week window.
How Penetration Testing Phases Change with Industries?
Different industry sectors introduce different objectives, changing the penetration testing phases. Here are a few examples:
1. Finance & Fintech
Compliance-driven (PCI DSS, SOX), finance and fintech sector emphasize on post-exploitation, persistence and fraud scenarios.
2. Healthcare
Data privacy and medical device security are the primary goals for healthcare companies. Thus, focus is on passive reconnaissance and exploit impact on patient care.
3. E-commerce
Heavy on API abuse and session hijacking, e-commerce always aims at time-bound testing to avoid downtime.
4. SaaS/Cloud
CI/CD and container security are top priorities for SaaS and Cloud Companies. Greater emphasis is placed on threat modelling and privilege escalation.
Testing phases do not change. However, what happens within each phase does depending on the set objectives.
Conclusion
Penetration testing is about proving how real those flaws are. Understanding the penetration testing phases allows business leaders and executives to connect technical testing with strategic outcomes.
If your goal is compliance, risk reduction or product hardening, visibility into each phase equips you to ask the right questions, hold vendors accountable and turn findings into action.
CyberNX is a CERT-In Empanelled penetration testing service provider with rich experience and expertise. Want to know about our methodology, testing approach and penetration testing phases? Contact us today.
Penetration Testing Phases FAQs
How often should we conduct a full-cycle penetration test across all phases?
Ideally, a full-cycle penetration test should be conducted annually or after any major infrastructure changes such as a cloud migration, new software deployment or a merger. However, for sectors like finance or healthcare, bi-annual or quarterly testing combined with continuous monitoring is suggested. Testing frequency should align with your threat landscape, compliance obligations and digital growth rate.
Can we skip or shorten any penetration testing phases to save time or cost?
Skipping penetration testing phases, especially reconnaissance or threat modelling, significantly reduces test accuracy and business value. Each phase contributes to building a realistic attacker profile and determining exploit paths with real-world consequences. A rushed test might miss critical risks, like misconfigured cloud permissions or orphaned APIs. If constrained by budget, consider narrowing the scope.
How can pentesting phases be integrated into our product development lifecycle?
Penetration testing can be integrated phase by phase into your SDLC. During product design, the threat modelling phase helps identify architectural flaws early. As features are built, teams can run reconnaissance and vulnerability analysis on staging environments. Just before launch, exploitation and post-exploitation testing simulate real attacks on the near-final product. Finally, the reporting and remediation phase aligns with QA and release processes. By distributing pen test phases across development, companies reduce late-stage surprises, accelerate fixes, and bake security into the product from day one.
How can we measure the effectiveness of each of the pentesting phases?
Effectiveness is measured by the depth, accuracy and business relevance of findings at each phase. For example, in reconnaissance, it is about how many unknown assets were uncovered. In exploitation, demonstrating real-world impact. In reporting, effectiveness lies in the clarity of risk communication and the practicality of remediation steps.