Those in leadership positions or executives often ask questions like, what does penetration testing cost? and what are we actually paying for? The answer isn’t simple, or just a number. Instead, it’s a story about risk, resilience and business priorities.
Also, penetration testing isn’t a one-size-fits-all service. It’s a tailored exercise shaped by scope, technology, objectives and outcomes. That’s why the cost varies widely.
Instead of publishing a flat figure, our experts believe in giving leaders clarity: what drives costs up or down and what hidden expenses to avoid. In addition, how to align penetration testing with your business objectives for lasting impact.
From scoping and methodology to reporting and retesting, we help organizations understand every factor behind the investment. So, when you do request a proposal, you know exactly what you’re buying.
Learn more about contract checklist while considering a service provider with our blog Penetration Testing Contract.
This guide breaks down the moving parts of pricing and shows how to shape a program that measurably reduces risk.
Penetration Testing and Vulnerability Assessment
There’s a lot of confusion between Penetration Testing (PT) and Vulnerability Assessment. Both are distinct services, but the thing is many offer both services together as VAPT. Others keep them separate. This has implications on the final cost.
As for definition, penetration testing simulates real-world attacks to validate exploit paths, business impact and response.
Know all about pentesting in our blog Penetration Testing Guide.
A vulnerability assessment, on the other hand, identifies weaknesses at scale and prioritizes them for action – often delivered as a vulnerability assessment service.
Find everything to know about this topic in our blog Vulnerability Assessment Guide.
You might need both, but you don’t have to overpay for either.
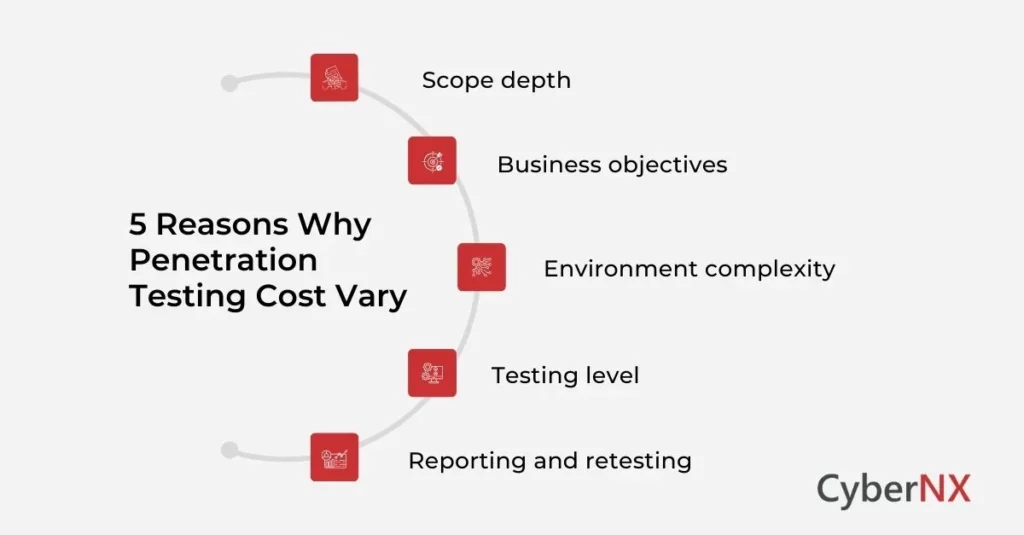
Why Penetration Testing Costs Vary
Pricing reflects five levers you can control:
- Scope depth: Does the scope include external only, or does it include web, mobile, APIs, cloud, and internal networks? A focused test may be 3–5 days. A complex, multi-scope engagement can span weeks.
- Business objectives: Are you validating a critical payment flow, checking zero-trust controls or meeting an audit deadline? Clear goals shorten delivery and sharpen findings.
- Environment complexity: Microservices, third-party integrations, legacy systems and unusual stacks add hours to the pentesting duration.
- Testing level: There are three types of penetration testing: Black-box, Grey-box and White-box. Find the differences in depth with our blog: Black Box vs. Grey Box vs. White Box. More access means more ground covered per day.
- Reporting and retesting: Executive readouts, developer-ready remediation steps and formal retesting windows add value plus line items.
Hidden Costs You Can Actually Avoid
The wrong scope, generic reports and lack of retesting can quietly double your penetration testing cost without improving security.
Clear planning and structured vulnerability assessment practices ensure you invest in meaningful results.
- Ambiguous scope: “Test the app” isn’t enough. Break work into features, roles and threat scenarios, guided by insights from a recent security assessment.
- No developer alignment: Findings that don’t map to stories get parked. Ask for developer-actionable steps, code samples and a guidance/remediation workshop.
- Retesting fatigue: Plan a retest window that matches sprint cycles. Fix fast, validate once and move on.
- Tool sprawl: You don’t need every automated scanner. A sensible risk assessment plus targeted manual testing beats noisy dashboards.
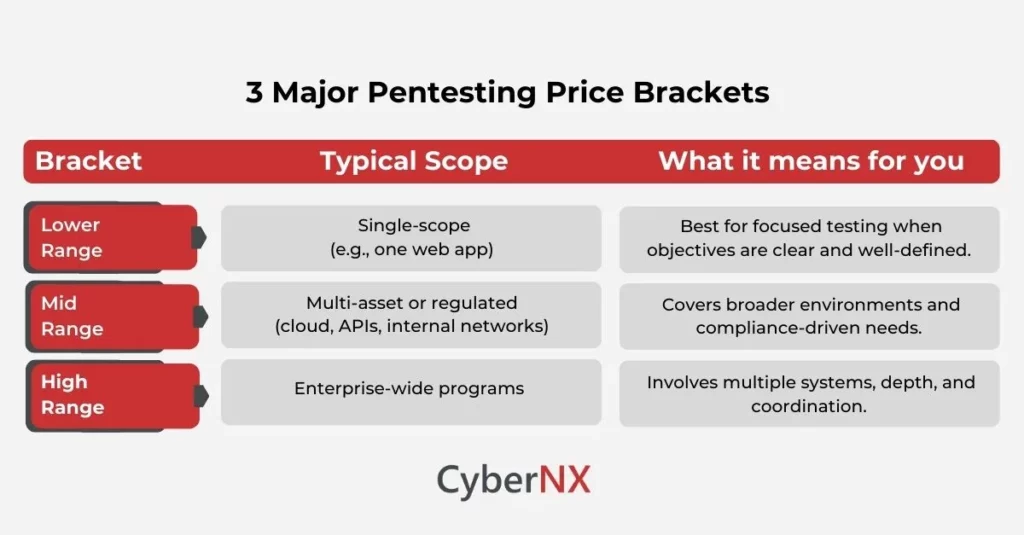
If you are looking for planning ranges, know that markets differ. And most organizations see three broad brackets:
What a Strong Proposal Looks Like
You’ll know you’ve got a solid partner when the proposal reads like a plan:
- Hypotheses tied to business risks: Testing should be mapped to real-world risks like fraud, data exposure or privilege abuse.
- Manual and automated testing: Methodology that blends manual testing with automation and references prior exposure review findings.
- Evidence model: Proof of impact, replay steps, screenshots and sample payloads.
- Clear deliverables: Executive summary, technical write-ups, prioritization and a retest commitment.
- Collaboration: Slack/Teams updates, office hours for engineers and knowledge transfer that elevates your next assessment program.
Budgeting That Survives the CFO Test
Split your annual spend into two streams. First, schedule targeted penetration testing for the systems where failure is not an option. Second, lock in a recurring pentesting service to keep drift in check. Over time, that recurring continuous assessment lowers pen test spend because fewer basic issues make it into the window, letting experts focus on true risks.
ROI in Plain Language
Penetration testing pays for itself when it prevents a breach, yes. But the daily ROI is quieter: fewer critical issues in production, faster audits and tighter change management. Pair that with a disciplined controls review and you reduce incident noise, reclaim engineering time and hit compliance with less drama. Your assurance assessment becomes early-warning radar.
How to Right-size Your Next Engagement
Right-sizing here would mean spending wisely.
Aligning business objectives with assessment and testing insights helps you target high-impact systems while avoiding wasteful testing.
1. Start with objectives
Pick two or three questions you must answer (E.g. Can attackers move from the customer portal to internal data?). Use a fresh surface assessment to prune low-value targets.
2. Choose access level wisely
Grey-box often lands the best signal for cost, especially when guided by assessment program artifacts (SBOMs, diagrams, prior findings).
3. Set reporting expectations
Ask for exploit narratives, asset owner mapping and a remediation roadmap that plugs into your backlog and your technical assessment cadence.
4. Demand retesting included
Real value arrives when fixes are verified and documented.
When Low Price Hides Lower Value
Beware quotes that seem too good. If the work is mostly automated scans, you’re buying a repackaged baseline assessment, not a true adversarial exercise. Automation is vital, but the expertise lies in chaining weaknesses, proving business impact and guiding fixes.
Conclusion
The question should shift from “What does it cost?” to “What does it change?” The smartest buyers insist every finding is fixed, every fix gets verified and every lesson builds the hardens architecture.
If you’re aligning budgets now, shortlist partners who collaborate well, define two make-or-break questions for your next test and refresh your penetration testing so scope and spend stay tight. CyberNX is a CERT-In empanelled cybersecurity company that treats pentesting services as the backbone of continuous security improvement. Our experts can help you pay less for noise and more for proof. Contact us today.
Penetration Testing FAQs
Does penetration testing cost change based on compliance requirements?
Yes, regulatory-driven tests often require stricter methodologies, deeper reporting, and evidence for audits, which can increase the overall penetration testing cost.
How often should businesses budget for penetration testing?
Most organizations plan for annual tests, but high-change environments often benefit from quarterly tests combined with ongoing vulnerability assessment services.
Is retesting usually included in the penetration testing cost?
Not always. Some providers charge extra for retesting, while others include it as part of a complete engagement. Clarify this upfront to avoid surprise costs.
How can vulnerability assessments help reduce penetration testing costs?
By fixing basic issues early, a vulnerability assessment lowers the scope of exploitable risks, ensuring pen testers focus on advanced threats – making your spend more efficient.