In Q1 2025, the average number of weekly cyberattacks per organization surged by 47%, climbing to 1,925 incidents globally. Many of the organizations believed their existing defences were sufficient, which as you can see, wasn’t.
Cybersecurity can no longer be reactive.
In today’s digital world, organizations face a constant barrage of cyber threats. To stay ahead, having a robust cybersecurity posture is essential. Penetration Testing as a Service (PTaaS) offers a complete solution to bolster your defences.
What is Penetration Testing as a Service?
Penetration Testing as a Service (PTaaS) is a subscription model for ongoing security checks. It’s different from traditional tests, which are done once. It keeps checking and fixing issues, keeping systems safe over time.
It’s a new way to check for weaknesses in systems.
At its heart, Pen test as a service mimics real cyber-attacks on systems and finds weaknesses that hackers might use. This way, businesses can fix problems and keep up with threats before they become big issues.
PTaaS: An Evolution from Traditional Penetration Testing
Traditional penetration testing has long been a key part of cybersecurity. But it has limitations. Like it is done only once and might not find all weaknesses.
Penetration Testing as a Service, on the other hand, has transformed the process by:
- Offering constant testing and watching
- Reporting vulnerabilities in real-time
- Scaling to fit growing business needs
- Providing access to top cybersecurity experts
Find out how pentest as a service takes a big leap from traditional pentesting and benefits your business in the next section.
7 Key Benefits of PTaaS Over Traditional Penetration Testing
Penetration Testing as a Service is levelling up cybersecurity for organizations. It provides a more detailed and ongoing security check. This new method has several advantages over traditional testing.
1. Continuous Security Assessment
Penetration Testing as a Service excels in continuous security assessment. It differs from traditional testing, which is done once. It keeps an eye on all your systems and tests an organization’s security all the time.
2. Real-Time Vulnerability Reporting
It provides real-time vulnerability reporting. This lets your organization spot and fix security risks quickly. In today’s fast-paced world, this timely reporting is key.
3. Cost-Effectiveness and ROI
It is a cost-effective option compared to traditional testing. Its subscription model (discussed later) helps organizations budget better and see a higher return on investment (ROI).
4. Scalability for Growing Businesses
As businesses grow, so do your security needs. Penetration Testing as a Service offers the scalability needed to meet these evolving needs. It ensures security measures grow with your business.
5. Improved Security Posture
PTaaS enhances your organization’s security posture through continuous testing and real-time reports. This proactive approach keeps businesses ahead of new threats.
6. Access to Specialized Expertise
PTaaS gives you access to expert testing team with industry-leading certifications and rich experience across diverse industries and testing environments. It also provide context-aware security insights and help address real risks to your business.
7. Reduced Security Blind Spots
Lastly, it reduces security blind spots by thoroughly testing an organization’s security setup. This detailed approach finds and fixes vulnerabilities fast.
PTaaS: The Subscription-Based Security Model
The Penetration Testing as a Service subscription model offers organizations a strategic and cost-effective way to manage security operations. It allows businesses to:
- Receive ongoing security checks without significant upfront investment
- Scale testing activities as the organization grows
- Leverage the latest cybersecurity tools and expertise
By choosing Penetration Testing as a Service, businesses can greatly improve application security. This ensures you are well-protected against new threats.
PTaaS: Comprehensive Testing Methodologies
Penetration Testing as a Service (PTaaS) employs a multi-layered testing approach to evaluate and strengthen the security of digital environments. It covers a wide range of attack surfaces to ensure a thorough assessment of an organization’s security posture.
1. Network Infrastructure Testing
PTaaS includes rigorous testing of network infrastructure components such as firewalls, routers, switches, and intrusion detection systems. These tests help identify misconfigurations, open ports, and other potential attack vectors that could be exploited by malicious actors.
2. Web Application Security Assessment
Web applications are tested against a broad spectrum of vulnerabilities, including SQL injection, cross-site scripting (XSS), broken authentication, and insecure deserialization. These assessments simulate real-world attack scenarios to ensure web assets are resilient under pressure.
3. Mobile Application Testing
With smartphones central to today’s application-driven ecosystem, mobile application testing is essential. PTaaS evaluates both iOS and Android apps for risks such as insecure data storage, improper session handling, and API exposure to ensure mobile users are protected.
4. API Security Testing
Application Programming Interfaces (APIs) form the backbone of modern applications and are frequently targeted. PTaaS includes API security testing to detect flaws such as broken object-level authorization, excessive data exposure, and improper rate limiting.
5. Cloud Infrastructure Assessment
As organizations increasingly adopt cloud environments, PTaaS also evaluates cloud-specific risks. This includes assessing configurations, identity and access management (IAM) policies, and exposed cloud storage services such as AWS S3 buckets to prevent data leakage and privilege escalation.
6. Social Engineering Simulations
Where applicable, PTaaS may include simulated phishing or pretexting attacks to assess employee awareness and the effectiveness of penetration testing social engineering training programs.
Reporting, Support, and Remediation Capabilities
In addition to comprehensive testing, PTaaS platforms typically offer powerful tools and expert guidance to support continuous improvement.
Advanced Reporting Dashboard
An integrated reporting dashboard provides real-time visibility into discovered vulnerabilities, their severity, and remediation status. This enables security teams to prioritize actions and maintain situational awareness.
Remediation Support and Guidance
When vulnerabilities are identified, expert teams provide actionable guidance to assist internal IT and development teams in applying fixes, patches, or configuration changes. This accelerates the remediation process and reduces risk exposure.
Compliance Mapping and Documentation
PTaaS services often include compliance-oriented testing frameworks that align with industry standards such as ISO 27001, PCI DSS, HIPAA, or GDPR. Detailed documentation helps demonstrate regulatory adherence during audits.
How the Penetration Testing as a Service Process Works?
The Penetration Testing as a Service process is designed to deliver comprehensive and adaptive security testing tailored to specific business requirements.
Step 1: Initial Security Assessment and Scoping
The first phase involves a detailed security assessment and scoping exercise. This helps in understanding the current cybersecurity posture, identifying potential weaknesses, and defining the scope of the testing engagement.
Step 2: Customized Testing Strategy Development
Following the assessment, a tailored testing strategy is developed. This strategy is aligned with real-world threat scenarios to uncover exploitable vulnerabilities that pose a risk to the organization.
Step 3: Continuous Monitoring and Testing Cycles
Our Pen Test as a Service includes ongoing monitoring and testing. This ensures your security is always evaluated and enhanced. It helps uncover new vulnerabilities and keeps security measures current.
Step 4: Real-Time Reporting and Alerts
Real-time reports and alerts are offered. This keeps clients informed of any security risks promptly. It allows you to act quickly to safeguard your digital assets.
Step 5: Remediation Guidance and Verification
The last step is providing guidance and verifying remediation efforts. The experts collaborate with your team to fix vulnerabilities, apply necessary patches, and confirm the effectiveness of these actions.
By adhering to this PTaaS framework, your business can greatly bolster your security posture and shield your systems against the modern cyber threats.
By following this structured PTaaS framework, organizations can significantly enhance their cybersecurity posture and defend against the constantly shifting cyber threat landscape.
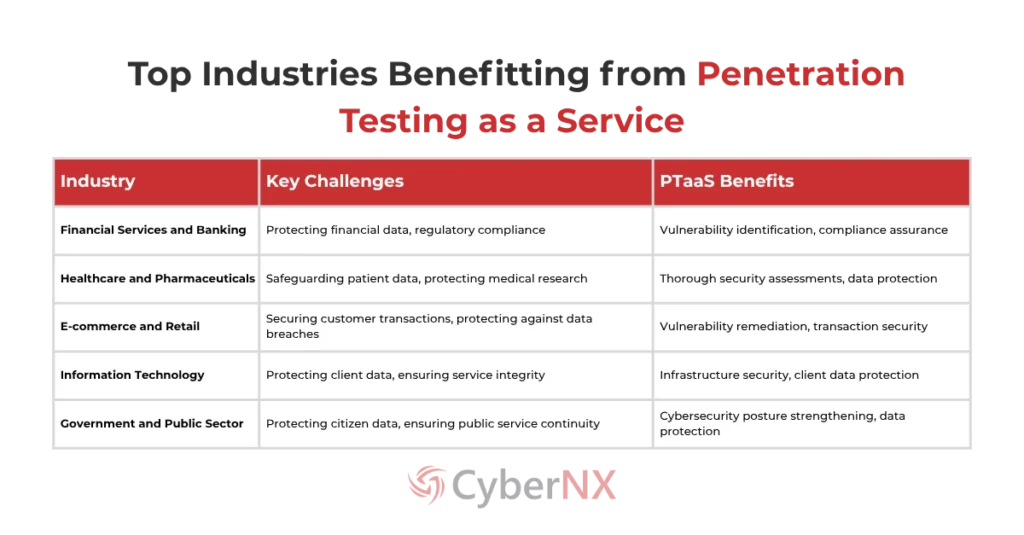
5 Industries Benefitting from Penetration Testing as a Service in India
By embracing Penetration Testing as a Service, industries can significantly bolster their cybersecurity, safeguarding against current and future threats.
PTaaS: Measurable Results and Outcomes
Penetration Testing as a Service has helped numerous organizations in India strengthen their digital defences against cyber threats.
| Industry | Vulnerabilities Identified | Remediation Rate | Security Posture Improvement |
|---|---|---|---|
| Financial Services | 25 | 95% | Significant |
| Healthcare | 30 | 90% | Moderate |
| E-commerce | 20 | 100% | High |
This highlights the role of Penetration Testing as a Service in boosting cybersecurity across industries.
How to Choose the Right PTaaS Provider for Your Business
Finding the right pentest as a service provider is critical for your organization’s security. It’s about detecting and fixing vulnerabilities effectively.
As you search for a provider, several important factors need to be considered.
Essential Provider Qualifications
Look for PTaaS providers with a strong background in cybersecurity testing. They should have the right certifications and meet industry standards.
- Check for certifications like CERT-In Empanelled, OSCP, CEH, or similar credentials that validate their expertise.
- Review their portfolio and case studies to gauge their success in handling similar projects.
- Assess their knowledge of the latest cybersecurity threats and penetration testing social engineering methodologies.
Service Level Agreement Considerations
A detailed Service Level Agreement (SLA) is key. It outlines the scope, timelines and expectations from the Pen Test as a Service provider.
- Clearly outline the testing frequency and coverage.
- Define the response times for vulnerability reporting and remediation.
- Establish metrics for measuring the effectiveness.
Integration with Existing Security Infrastructure
Make sure the Pentesting as a Service provider can integrate well with your current security setup. This means they should work with your existing tools and systems. They should also provide insights that enhance your security measures.
Pricing Models and Value Assessment
Examine the pricing models of Pen Test as a Service providers and evaluate their value to your organization.
- Consider the cost-effectiveness of the service.
- Assess the ROI in terms of enhanced security posture.
- Look for flexible pricing plans that can scale with your business needs.
By carefully considering these factors, you can make an informed decision. Choose a provider that meets your business needs and boosts your cybersecurity.
Conclusion
Companies today must focus on strong security to safeguard their digital assets. Penetration Testing as a Service is key to a solid cybersecurity plan. It offers ongoing security checks, immediate vulnerability reports and is cost-effective.
Moreover, choosing this service boosts a company’s security, closes security gaps, and meets regulatory standards.
Our unique approach provides a customized security solution. It includes a detailed testing method, an advanced reporting dashboard and support for fixing issues. To know more about how CyberNX Penetration Testing as a Service can fortify your digital future, reach out to us today.
Penetration Testing as a Service FAQs
What features should I look for in a Penetration Testing as a Service?
Seek thorough testing methods and advanced reporting dashboards. It should also offer remediation support and compliance mapping. This ensures a robust service.
How does PTaaS help with regulatory compliance?
Pentesting as a Service provides compliance mapping and documentation. This helps organizations meet regulatory needs and maintain a strong cybersecurity posture.
Can Pen test as a Service be integrated with my existing security infrastructure?
Yes, a good provider integrates their service with your existing security setup. This ensures effective and seamless cybersecurity testing.
What industries can benefit from Pentesting as a Service?
Financial services, healthcare, e-commerce, IT, and government sectors face unique cybersecurity challenges. Pentesting as a Service helps them meet these challenges and comply with regulations.