Four years ago in 2021, hackers exploited a single compromised password to breach Colonial Pipeline’s network, costing the company millions.
One overlooked vulnerability inside a huge corporate network, triggered such a big crisis. That’s the scale and risk every business is dealing with today.
Enterprise networks are not static data corridors. They are vast, constantly shifting ecosystems of endpoints, cloud connections, VPNs, remote devices, third-party integrations and legacy systems.
Everything is connected everywhere. And every new connection gives birth to a potential point of failure.
You can avoid such data breaches and evolving modern threats by employing Network penetration testing. A direct, reliable way to measure your network’s resilience before a cyber attacker does.
What is Network Penetration Testing?
Network penetration testing is a type of pen test where your entire computer network is targetted by ethical hackers. What is the objective? To identify and reveal possible vulnerabilities that could be fixed before attackers exploit them. It is done ethically and in a controlled environment.
The exploitable gaps across your internal and external networks include unpatched systems, misconfigured devices, exposed ports and poor access controls. It should be seen as a security exercise, a risk assessment for a strong security posture.
That answers the “what is penetration testing in network security” question that we often come across.
If you want to know more in-depth about other types of penetration testing, read our blog: Types of Penetration Testing: A Complete Overview
Methodology: How to do Network Penetration Testing
While there is no one-size-fits-all approach for network pentesting methodology, but here’s a commonly followed structured methodology:
1. Scoping:
Defining objectives is the first step. Potential questions include – are you testing internal systems, external-facing assets or both, what is the tolerance for disruptions.
2. Reconnaissance (Passive & Active):
Pentesters collect data about the target environment. Passive reconnaissance involves analysing public data like DNS records, while active involves scanning for live hosts and open ports.
3. Enumeration & Vulnerability Scanning:
Testers go one step deeper and identify services, user accounts and known vulnerabilities using automated tools.
4. Exploitation:
Once everything is uncovered, pentesters make attempts to exploit vulnerabilities with the aim to gain unauthorized access, essentially emulating a real attack scenario.
5. Post-Exploitation:
If and when access is gained, testers assess how far they can go, pivoting across networks, extracting sensitive data and escalating privileges.
6. Reporting & Debrief:
A comprehensive report is delivered along with recommendations, prioritised risks and a remediation roadmap.
Why It Matters: The Business Case for Network Pentesting
Now that you know how to do pentest network, know why it matters.
Advanced firewalls, intrusion detection systems and strong endpoint protection – you have invested in them all. But those are only as good as their configurations and the people managing them.
Network pentest goes beyond and delivers:
1. Risk visibility
It helps leaders to better understand the real-world impact of vulnerabilities in their respective business context.
2. Regulatory compliance
Many standards such as ISO 27001, PCI DSS mandate or recommend periodic network pen testing. So, it is a win-win situation for businesses.
3. Incident prevention
Perhaps the biggest benefit: network pen testing proactively discovering flaws prevents potentially catastrophic breaches.
4. Board-level accountability
Pen test reports offer C-level executives a clear narrative around cybersecurity risks and where to invest in security – in tools and training or restructuring IT assets.
Internal vs External Network Pentesting
Here’s a quick overview of what each approach entails before diving deeper.
1. External penetration testing
External penetration testing targets assets that are exposed to the internet. It includes web servers, firewalls and VPN gateways. It conducts a mock cyberattack to breach the perimeter.
2. Internal penetration testing
Internal penetration testing is done assuming the hacker is already inside through a compromised employee device or rogue insider. This test evaluates lateral movement, privilege escalation and the strength of internal segmentation.
Why does it matter?
This is important because most breaches start with an external compromise and escalate internally. So, you need eyes on both areas for a clear pen testing network security picture.
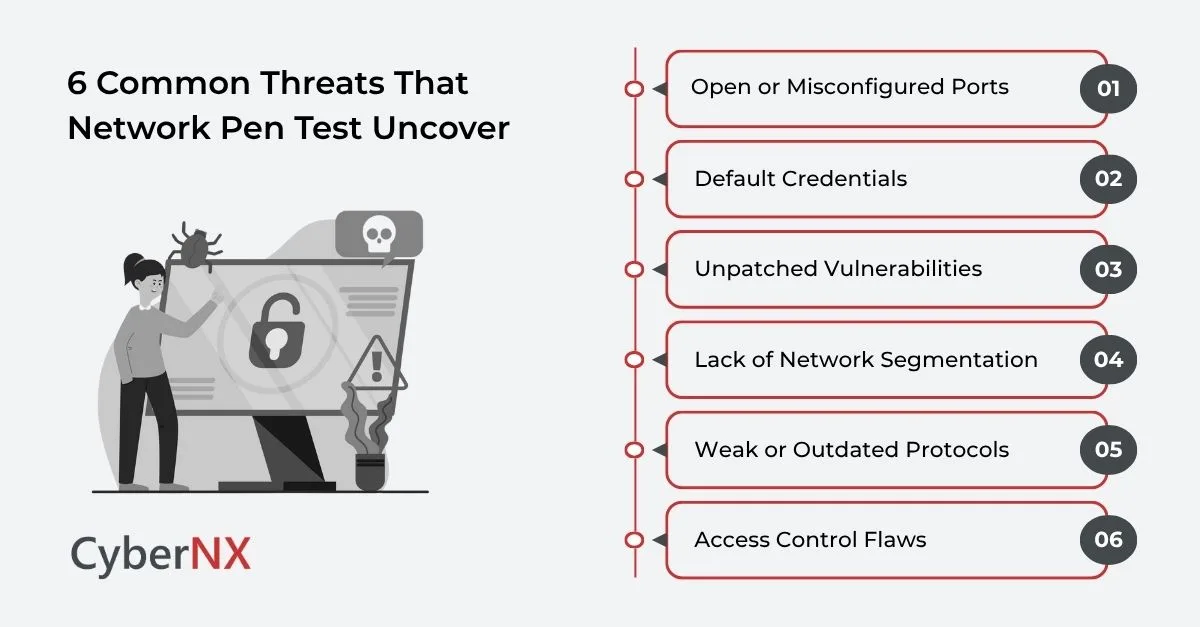
Common Threats That Network Pen Test Uncover
Even mature and well-established organizations are often surprised by the vulnerabilities uncovered during a professional network penetration test. These weaknesses can act as silent enablers for attackers to infiltrate, pivot, and exfiltrate data without detection. Below are some of the most common threats identified through network pen testing:
- Open or Misconfigured Ports: Unsecured or unnecessary open ports expose internal services and systems to external attacks, providing easy entry points for threat actors.
- Default Credentials: Devices like routers, switches, or printers often retain factory-set passwords, which attackers can easily exploit using credential databases or brute force.
- Unpatched Vulnerabilities: Outdated operating systems, firewalls, and third-party software often contain known flaws that attackers can exploit for privilege escalation or lateral movement.
- Lack of Network Segmentation: Flat networks make it easier for attackers to move freely once inside, compromising multiple systems from a single breach point.
- Weak or Outdated Protocols: Legacy protocols such as SMBv1 or unsecured SNMP lack encryption and authentication, exposing sensitive information to interception.
- Access Control Flaws: Misconfigured permissions allow users – and attackers posing as users – to access data or systems beyond their intended scope.
Tools Professionals Use for Network Pen Test
Network penetration testing relies on a blend of automation and human expertise. While tools form the foundation of the process, expert pentesters bring context, strategy, and interpretation that no automated scan can match. Commonly used tools include:
- Nmap: For network discovery and port scanning.
- Nessus: To detect vulnerabilities, misconfigurations, and missing patches.
- Metasploit: For exploiting discovered vulnerabilities and validating potential impact.
- Wireshark: To capture and analyse network traffic at a granular level.
- Burp Suite: Useful in network-related testing of web-facing assets.
Expert pentesters along with these top tools helps in connecting the dots and evaluating business impact, delivering best outcomes using a network pentesting methodology.
What Should a Network Penetration Testing Report Include?
A high-value pen test report does not include just a list of CVEs and IP addresses; it includes strategic insight for decision-making. Here’s what to expect:
1. Executive Summary
A non-technical overview of findings, risks and business impact
2. Detailed Technical Findings
Each issue explained with evidence, risk level, affected systems, and possible impact
3. Risk Prioritization
Vulnerabilities ranked by likelihood and impact
4. Remediation Guidance
Actionable, specific recommendations tailored to your environment
5. Attack Narrative
If exploitation succeeded, the report should detail the attack chain step-by-step
6. Appendices
Supporting data like screenshots, tool outputs and methodologies used
A strong penetration testing report by experienced network pentesting teams provides your leadership team utmost clarity as to what must be done.
Conclusion
Our Network penetration testing enables your business to understand where your defences truly stand. It shows you what attackers will see, how they will possibly exploit it and how far they could go.
Are you ready to take a clear-eyed look at your network’s security posture? Partner with experts at CyberNX who not only test your defences but help you strengthen them where it matters most. Safeguard for business continuity, brand reputation and operational trust. Contact us today!
Network Penetration Testing FAQs
How often should a company perform network penetration testing?
At a minimum, organizations should conduct network penetration testing annually. However, frequency should be driven by risk exposure. Businesses in finance, healthcare, or critical infrastructure – and those handling sensitive customer data – should test more frequently, often biannually or quarterly. Additionally, testing is essential after major changes such as infrastructure upgrades, new system deployments, cloud migrations, or mergers and acquisitions. Regular testing ensures vulnerabilities aren’t silently introduced into your evolving environment.
What’s the difference between a vulnerability scan and network penetration testing?
A vulnerability scan is an automated process that flags known security weaknesses across systems and devices. While it’s useful for identifying potential issues, it doesn’t validate how exploitable those issues really are. Penetration testing network assessments go further – emulating how real-world attackers would exploit those weaknesses to access systems, move laterally across your network, and exfiltrate data. The result is a far deeper understanding of actual risk, not just technical flaws.
Can network penetration testing disrupt business operations?
When properly scoped and executed, penetration testing is designed to avoid disruption. Ethical hackers coordinate closely with your internal teams to define safe testing windows, limit risk to production systems, and use non-destructive techniques. While some tests may simulate aggressive behaviour, controls are in place to prevent downtime or data loss. Any risk to operations is manageable and significantly lower than the cost of a real breach.
Is network penetration testing required for regulatory compliance?
Yes. Many industry standards and regulatory frameworks mandate or strongly recommend network penetration testing. PCI DSS requires regular testing of both internal and external systems. ISO 27001, SOC 2, HIPAA, and GDPR all emphasize the need to evaluate system defences against real-world threats. Beyond compliance, penetration testing network reports also provides auditors and stakeholders with demonstrable proof that your security program is proactive and effective.