Checking apps is as natural as sipping coffee, isn’t it? Recent reports reveal that an average person uses 18 apps and spends 4.8 hours daily on mobile apps.
Apps have become more than tools; they are now extensions of everyday life.
It is not a surprise that businesses now invest so much in mobile apps. But here is the part that should make your business pause: those apps are collecting and exchanging sensitive data, constantly.
And as some expert once said, “Where there’s data, there’s risk.”
So, if you build, manage or secure mobile applications, it is important to ask the question: Are we ethically conducting penetration testing for mobile apps against real-world attacks? If not, mobile application penetration testing is the wake-up call your business needs.
What Is Mobile Application Penetration Testing?
Like every other pentesting, mobile application penetration testing simulates cyberattacks with the goal of finding and fixing vulnerabilities before threat actors can get their hands on them. Only the difference is that the test is done on mobile apps. This proactive, ethical way assesses how secure your mobile app truly is for you as well as your users.
Want to know about other types of Penetration Testing? Check our blog: Types of Penetration Testing: A Complete Overview
Mobile App Pentesting by Platform
As soon as you hear mobile or smartphones, you know there are two popular operating systems on which they rub: Android and iOS. So, we have discussed briefly about penetration testing on both systems.
1. Android Penetration Testing
You must have seen files with .apk suffix if you are an Android user. They are required for the Android application to run. Android penetration testing involves static and dynamic analysis of APK files.
Issues like insecure data storage, exposed activities or services, weak cryptographic implementations and misuse of inter-process communication (IPC) via intents are detected. It also evaluates the app’s behaviour on rooted devices and checks for code obfuscation.
2. iOS Penetration Testing
iOS penetration testing targets IPA files to uncover vulnerabilities such as keychain data leakage, improper usage of URL schemes, insecure entitlements and unencrypted data in local storage.
It includes sandbox bypass attempts, runtime analysis using tools like Frida and reverse engineering of Objective-C or Swift binaries to identify logical and architectural flaws.
Moving on…
Types of Mobile Applications
There are mainly 3 types of mobile applications and their testing is discussed here:
1. Native Apps
Built specifically for Android (Java/Kotlin) or iOS (Swift/Obj-C), native apps need in-depth testing at both the binary and API levels.
2. Hybrid Apps
Created using web technologies like React Native or Ionic, but they run inside a native shell. They combine both mobile and web threats.
3. Mobile Web Apps
Accessed through browsers but optimized for mobile, mobile web apps security is largely like traditional web apps but with mobile UX layers.
As each app type has a unique attack surface, the mobile app penetration testing approach is adapted accordingly.
Importance and Benefits of Mobile Application Penetration Testing
Modern cyber threats have gone beyond imagination. Cyber attackers now use sophisticated toolkits, social engineering and zero-day exploits to go after mobile environments.
What’s scarier is that every app update, new feature or integration in a mobile app introduces new risks.
As businesses increasingly rely on mobile-first strategies, regular penetration testing mobile applications is the path to choose because of its obvious benefits.
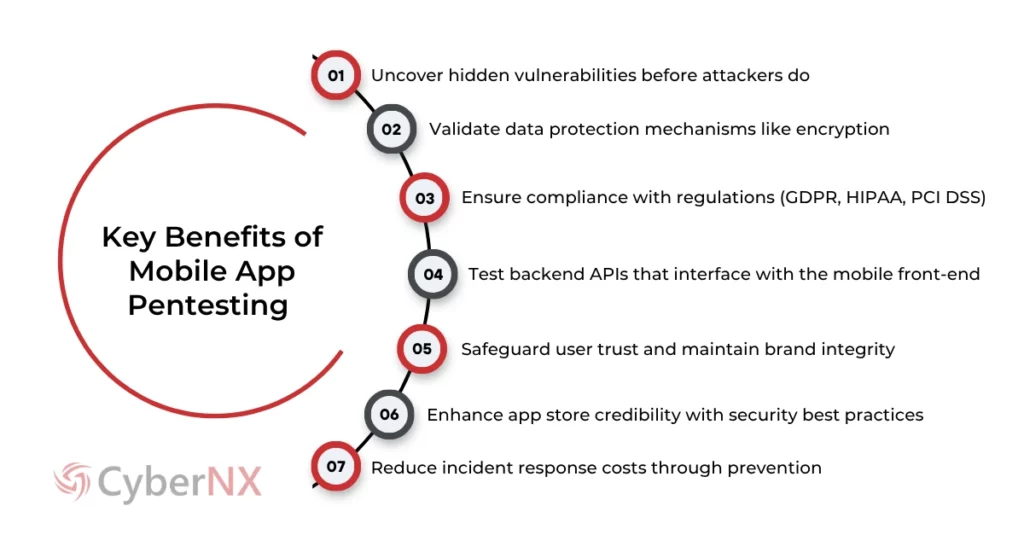
Key Benefits of Mobile Penetration Testing
Mobile app penetration testing is essential for businesses relying on mobile channels to engage customers and process sensitive data. It helps identify security gaps before they turn into costly breaches, ensuring your app remains secure, compliant, and trusted.
1. Identify and Fix Hidden Weaknesses Early
Mobile app penetration testing helps uncover security flaws in your mobile applications and backend APIs before cybercriminals can exploit them. This proactive approach ensures your app is resilient against real-world attacks and protects sensitive business data.
2. Strengthen Data Protection and Compliance
Through mobile pentesting, organizations can validate encryption, authentication, and session management controls while ensuring compliance with data privacy laws such as GDPR, HIPAA, and PCI DSS. This builds a stronger foundation for secure mobile operations.
3. Build Trust and Reduce Business Risk
By conducting regular mobile app penetration testing, businesses can safeguard user trust, enhance app store credibility, and significantly reduce the cost and impact of potential breaches. Prevention-driven testing strengthens brand reputation and long-term digital resilience.
Difference Between Web and Mobile Application Penetration Testing
Now that’s a question a lot of people ask. For once and for all, we wanted to address it. Mobile application penetration testing is not just web pentesting with smaller screens. Not, not all.
Here are key differences:
- Unlike web applications that operate in browsers, mobile apps sit on user devices. This striking difference opens an entirely different attack surface.
- Mobile apps store data locally, rely on device permissions, use hardware features (like GPS or camera) and often integrate with native OS functions.
- New risks like insecure local storage, improper platform usage or exposure of hardcoded secrets are introduced.
- Mobile apps interact with APIs differently, may use offline modes and often lack real-time monitoring.
Web app penetration testing focuses heavily on input validation and browser-based vulnerabilities. But mobile application penetration testing dives into binaries, de-compilation, runtime behaviours and platform-specific quirks.
If you are somehow only testing the backend and ignoring the app itself, know that you are only securing half the system.
Explore more about web apps pentesting: Web Application Penetration Testing: A Modern Imperative For Digital Security
Mobile Penetration Testing Methodology
The mobile pentesting methodology generally involve 6 steps. Take a look:
- Reconnaissance: Identifies the app version, architecture, third-party libraries and API endpoints.
- Static Analysis: Decompiles the app to examine source code, find hardcoded keys, insecure logic and flaws.
- Dynamic Analysis: Runs the app in a controlled environment to study behaviour, test permissions plus monitor data flows and intercept traffic.
- API Testing: Probes backend APIs for authorization flaws, sensitive endpoints, token leaks and injection attacks.
- Exploit Attempt: Tries real-world attack scenarios like privilege escalation, bypassing authentication or code injection.
- Reporting: Provides a comprehensive report with risk ratings, reproduction steps and actionable remediation guidance.
Mobile Penetration Testing Security Frameworks
Mobile penetration testing security frameworks provide standardized methodologies to evaluate the security posture of mobile applications and devices. They help ensure consistent, comprehensive testing across platforms like Android and iOS.
- OWASP MASVS (Mobile App Security Verification Standard): This is an industry benchmark for mobile application security. It covers everything from architecture and storage to communication and code quality.
- OWASP Mobile Top 10: A popular list of the ten most critical security risks for mobile apps every pentesting service provider should address.
- NIAP and CIS Benchmarks: Useful for government and regulated industries, these benchmarks act as platform-hardening guidelines.
Choosing these frameworks ensures that mobile application security testing is structured, repeatable and aligned with global best practices.
Common Security Threats in a Mobile Application
Mobile apps face a range of threats, from insecure storage to weak APIs. Knowing these risks is key to preventing data leaks and security breaches.
Despite its importance, mobile penetration testing can be challenging due to fragmented device ecosystems, complex architectures and third-party SDK dependencies.
These factors often create blind spots that limit visibility during testing. However, a structured mobile pentesting approach – integrated early in the SDLC and supported by regular API and SDK assessments – can overcome these limitations.
Combining mobile penetration testing insights with threat modelling, secure coding practices, and runtime protections such as tamper detection ensures comprehensive coverage and stronger mobile application security across all environments.
Common Tools for Mobile Application Penetration Testing
Our experts reveal the top tools used for mobile application penetration testing.
- MobSF: Works for both static and dynamic analysis of Android and iOS apps.
- Frida: Dynamic instrumentation toolkit that helps in inspecting and modifying app behaviour in real-time.
- Burp Suite: Intercepts and manipulates API traffic and it is essential for finding flaws in server-side logic.
- JADX & APKTool: For decompiling and analysing Android app binaries.
Mobile Application Penetration Testing Checklist
A checklist makes sure that no critical area is overlooked during mobile penetration testing. Find below what pentesters usually tick off while doing testing:
- Architecture Review: First analyse app type (native, hybrid, web), third-party SDKs and backend integrations.
- Static Analysis: Then decompiles APK/IPA files to examine hardcoded credentials, weak encryption, exposed APIs and insecure coding practices.
- Dynamic Analysis: This step involves observing runtime behaviour on emulators or real devices and looking for runtime anomalies.
- Authentication & Session Management: Tests for weak logins, session fixation, token leakage, insecure biometric implementation and timeout issues.
- Data Storage & Leakage: Checks for sensitive data in shared preferences, SQLite, keychain or external storage in plaintext.
- API & Backend Security: Performs fuzzing and injection attacks on mobile-to-API communication. Validates authentication, rate limiting and error handling.
- Transport Security: Verify HTTPS enforcement, TLS version, SSL pinning and certificate validation.
- Reverse Engineering & Tampering: Attempt to reverse-engineer or modify app logic using tools like Frida, Objection or Ghidra.
- Permission & Component Misuse: Identify excessive or misused permissions, exposed activities/services and insecure intent handling.
A robust checklist like this boost testing coverage and protects brands from the risks you did not see coming.
Advanced Threats, Emerging Trends & Future-Proofing
Modern mobile applications are no longer vulnerable only to basic exploits. They’re now exposed to sophisticated attacks like SDK supply chain compromises, runtime manipulation and API abuse.
With the rapid rise of 5G, IoT, and AI-driven apps, the attack surface has expanded dramatically. Mobile penetration testing plays a crucial role in identifying and mitigating these evolving threats.
By combining static, dynamic, and runtime analysis, mobile pentesting helps organizations detect complex vulnerabilities early. Regular and continuous mobile penetration testing ensures your security strategy evolves with emerging technologies, keeping your business future-ready and resilient against advanced attacks.
Duration of Mobile Penetration Testing
A comprehensive mobile application penetration testing typically takes 5 to 15 business days, depending on app complexity, number of platforms (iOS/Android), API surface and whether it’s a native, hybrid or web app.
A standalone Android app may take 5–7 days, while a complex multi-platform app with deep API integrations may require 2–3 weeks. You must consult experts to know latest information about duration.
Conclusion
Apps are not digital products anymore. They are the engines driving the business forward.
If your app handles customer data, payments, health records or even user preferences, it deserves the same level of security scrutiny as your network or backend systems. This is because every tap, every API call, every stored token is a potential vulnerability if left unchecked.
So, do not wait for a breach to happen, choose CyberNX mobile application penetration testing to secure your mobile apps today. Contact us to know more.
Mobile Application Penetration Testing FAQs
What’s the key difference between Android and iOS penetration testing?
Android testing involves reverse-engineering APKs, analyzing inter-process communication via intents, and evaluating behavior on rooted devices. iOS testing focuses on IPA file analysis, inspecting keychain data storage, checking entitlement configurations, and attempting to bypass Apple’s sandbox protections. Each platform requires distinct tools and techniques.
Can hybrid or cross-platform apps be tested with the same approach?
Not quite. Hybrid apps need a combined approach – web testing for frontend code (HTML, JavaScript) and mobile testing for the native shell. The communication bridge (like WebViews) must also be examined for security flaws.
How often should I schedule mobile application penetration testing?
At least once a year, or after major updates and new feature releases. Apps handling sensitive data – like fintech or healthcare – should undergo mobile application pentesting quarterly or continuously for maximum protection.
What factors influence the cost of mobile application penetration testing?
Mobile pentesting cost depends on scope: platforms covered, app complexity, API integrations, and testing depth. Pricing differs for basic tests and for enterprise-grade assessments involving advanced manual testing and remediation support.