Enterprises with complex IT environments often have to manage a large volume of data and systems, making threat visibility and response challenging. Same is the case for organizations handling sensitive data with a high compliance burden and SMBs with limited security resources.
No matter how big the budget, security teams may require managed service providers for effective detection and response programs. That’s where Managed Detection and Response (MDR) and the Security Operations Centre (SOC) add immense value.
So, what is the challenge? Both are built to detect, investigate and respond to threats. But how does your business choose the best one? This blog will take a closer look at SOC vs MDR as threat detection and response strategies, explore the fundamentals and offer a framework to help you make the right decision.
What is MDR?
Managed Detection and Response (MDR) comprises cutting-edge threat detection technologies, 24/7 human expertise and swift incident response. The service name itself gives these characteristics away.
But how does your business benefit on a deeper level? MDR service provider gives complete visibility of your environment, helping security teams find malicious activities in real or near real time.
Operations become seamless instantly with the help of added resources and 24X7X365 coverage. Advanced technology stack and expertise help analyse threat actor behaviour and fix them before anything goes out of hand.
Endpoint Detection and Response (EDR), behavioural analytics and real-time threat intelligence – all these features – sets MDR apart. However, you should partner with those MDR service providers who go beyond and offers only true positive threats, deeper visibility, customized remediation measures and valuable insights.
That could be a real game-changer for security teams and bottom line for businesses.
Key features of MDR:
- Human experts monitoring and delivering incident response delivered
- Fast deployment with almost no dependency on in-house security teams
- Smart, pro-active threat hunting and external attack surface handling
- Automation for fast containment and investigation measures
MDR suits organizations seeking enterprise-grade protection or who desire to level-up their security posture.
Read our blog MDR Guide where we have covered in-depth about all the topics related to it.
What is SOC?
Security Operations Centre (SOC), some call it the nerve centre or heart of a security strategy, fills big security holes in modern companies. As a centralized function which manages ongoing threat monitoring, incident analysis and response coordination, SOC is a major boost to any cybersecurity program in place. Under Managed Security Service Provider (MSSP) or as a hybrid model, SOC works wonderfully for organizations.
SOC is basically a team consisting of experts who defend, respond and monitor on behalf of companies. A big team that typically operates using technologies like Security Information and Event Management (SIEM), threat intelligence platforms and automated workflows. Their goal? To collect and analyse telemetry across the digital ecosystem that includes endpoints, cloud, networks and applications.
Key features of SOC:
- Centralized visibility and unified threat monitoring
- Coverage across IT, OT and cloud environments
- Easy integration capabilities with regulatory, compliance and audit systems
- Structured escalation and coordination with internal security and IT functions
Organizations with complex infrastructure, high regulatory burden or deeply integrated operations often rely on SOCs to anchor their cybersecurity program.
Read our blog SOC Guide, where we have covered all facets of Security Operations Center.
What is the Difference Between MDR and SOC?
While both MDR SOC are geared toward early threat detection and coordinated response, how they deliver that protection is markedly distinct.
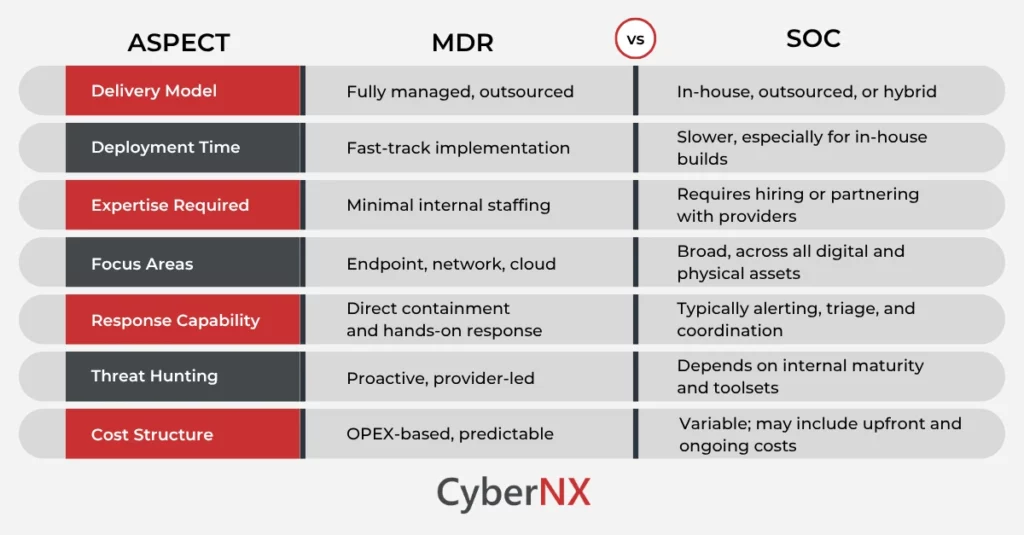
Where MDR and SOC Align
Both MDR and SOC offer continuous threat monitoring, integration with threat intelligence feeds, alert triage, investigation and escalation. Plus, they identify advanced threats such as zero-days and APTs.
Where MDR and SOC Diverge
The most defining contrast lies in ownership and execution. MDR providers are active participants in incident response. SOCs, depending on structure, may act more as observers, escalating threats to internal teams for remediation.
MDR vs SOC: Why Security Teams Need Managed Service Providers
Modern cyber threats are sophisticated and advanced in nature – thanks to AI and other technologies. Keeping a tab across the IT infrastructure for vulnerabilities may seem impossible with limited resources, expertise and technology stack.
There are a few other challenges which are briefly discussed below:
- Lack of experienced security professionals who have seen it all and done it all, and understands the evolving nature of threats
- Operational obstacles and budget constraints
- Alert fatigue from fragmented systems can make retaining talents difficult
- Mounting compliance pressure and governance demands every year
Managed services like MDR and SOC meet these needs by offering end-to-end protection.
MDR vs SOC: How to Choose the Right Approach?
Choosing a managed service provider might need a look into the fabric of your organization’s security maturity and priorities. It might be offloading certain processes, gaining an upper hand with specific expertise or 24X7X365 coverage. Here are a few other factors you should consider:
1. Scale and Complexity
If you are securing a few cloud-native workloads or a vast hybrid ecosystem, SOCs offer customization options and enough depth for large and complex environments.
2. Internal Capabilities
If you do not have experienced cybersecurity resources or the means to scale a team as of now, MDR is the best alternative with minimal challenges.
3. Deployment Timelines
When you need to secure fast, MDR solutions’ plug-and-play model delivers value in days or weeks. SOCs, especially in-house, may take months to mature.
4. Cost Predictability
MDR services are subscription-based models, whereas SOC investments may vary based on architecture, tooling, staffing and training.
5. Regulatory Pressures
If your business is into finance, healthcare or other regulated sectors, a SOC may offer better integration with compliance reporting and audit frameworks.
Conclusion
Choosing between managed services like MDR and SOC is all about which aligns with your organization’s architecture, risks and strategic direction.
Increasingly, many organizations are embracing a hybrid model, where MDR covers the frontline with precision, while a SOC drives broader visibility, governance and strategic oversight.
With a 100+ team of experts, cutting-edge technology and expertise across the security spectrum, we offer MDR services with our Elastic Defend platform with wide range of advanced detection and response capabilities.
We also provide AI Managed SOC services, boosting threat detection and response efficacy using commercial threat intelligence. Contact us today!
MDR vs SOC FAQs
Can MDR and SOC coexist within the same cybersecurity strategy?
Absolutely. Many modern organizations adopt a hybrid model, where MDR handles tactical detection and rapid response, while a SOC—internal or external—oversees strategic functions like compliance, long-term threat analytics, and enterprise-wide coordination. This dual-layered approach offers both agility and control, especially for businesses operating in regulated or high-risk environments.
How does the choice between MDR and SOC affect incident response time?
MDR services typically include automated containment and analyst-led response, often reducing mean time to detect (MTTD) and mean time to respond (MTTR) to minutes or hours. In contrast, SOC response time depends on internal workflows, staffing, and integration maturity. Organizations that prioritize fast response with minimal human bottlenecks often lean toward MDR.
What compliance frameworks influence the need for SOC over MDR?
Industries governed by regulations such as HIPAA, PCI-DSS, GDPR, or ISO/IEC 27001 often require centralized log management, forensic readiness, and auditable incident handling—capabilities that a SOC is typically better suited to deliver. While MDR providers can assist with compliance, a SOC provides the infrastructure for sustained governance and evidence collection.
What hidden costs should be considered when building an in-house SOC?
Beyond tools and talent, building a SOC incurs ongoing costs in training, retention, threat intelligence subscriptions, 24/7 shift coverage, compliance audits, and technology upgrades. There’s also the cost of false positives, operational burnout, and time lost during SOC ramp-up. These hidden expenses often lead businesses to re-evaluate SOC ownership in favour of managed solutions like MDR.




