Organizations function today in a threat-heavy world. Deciding on how to secure your organization is about acquiring the best technology. Plus, it is about selecting a security partner who can think ahead, act fast, and scale with you. That’s where the MDR vs MSSP conversation becomes essential.
Oftentimes, businesses looking to invest in security can get confused by acronyms used interchangeably by experts, authors and service providers. Here we are to help you choose the best.
While both are managed services designed to unburden mostly overwhelmed IT and security teams, the real difference lies in how and when they do it. This blog explored MDR vs MSSP and helps you understand how each model performs under pressure. Additionally, you will come to know which one aligns best with your business, your risk appetite and your growth ambitions.
What is MDR (Managed Detection and Response)?
MDR, or Managed Detection and Response, is a proactive, intelligence-driven cybersecurity service model. It is often confused with EDR and XDR, which are tools and not services. To know the real difference between them, read our blog EDR vs MDR vs XDR.
Coming back to MDR, it is primarily focused on detecting genuine threats quickly and stopping them before any substantial damage is done. It blends human expertise with rich telemetry from endpoints, networks, identity systems and cloud environments.
When compared to traditional services that simply raise alerts and leave response to security teams, MDR steps into the combat the threats. It delivers context and clarity, supported by trained analysts, threat hunters and real-time incident responders.
Still unsure how Managed Detection and Response helps secure your business? Read our in-depth blog MDR Guide.
Benefits of MDR
For organizations navigating complex architectures, advanced threat actors and lean internal security teams, MDR is a game-changer. It provides a critical balance of speed, insight and action. Key benefits of MDR can be summarized as follows:
- Rapid Detection & Response: Threats are identified and mitigated in near real time.
- 24X7 Human Expertise: Security analysts continuously analyse threats and investigate alerts.
- Advanced Threat Hunting: Goes beyond signature-based detection to identify behavioural anomalies and stealthy attacks.
- Endpoint and Cloud Visibility: Offers deep visibility into endpoint, identity, network and cloud infrastructure.
- Automated and Manual Response: Combines automated playbooks with expert intervention for faster remediation.
With AI capabilities, global threat intelligence, correlation engine and tools like XDR, MDR enables security outcomes, bringing both precision and peace of mind to your security teams.
What is MSSP (Managed Security Service Provider)?
An MSSP is designed to help businesses manage and monitor cybersecurity infrastructure like firewalls, IDS/IPS systems, antivirus and SIEMs. They offer expertise and they act as trusted advisors tool. Their model is rooted in maintaining the health of your tools and ensuring visibility through log analysis and event monitoring.
Most of the MSSPs work as your infrastructure custodian, notifying you that something is off and work with your internal teams. However, the final action lies with your security professionals within an organization.
Advantages and Disadvantages of MSSP
MSSPs is a good entry point into managed security, especially for organizations that need 24X7 oversight but lack the resources for in-house capabilities. But their scope and approach are sometimes limited.
Advantages
MSSPs offer broad, affordable coverage for foundational security tasks like log monitoring, patching and compliance. They are ideal for organizations seeking outsourced support without building a full in-house SOC.
- Cost-Effective for Basic Monitoring: Ideal for companies looking to outsource foundational cybersecurity tasks.
- Broad Security Coverage: Can manage firewalls, patching, antivirus, compliance reporting and more.
- Scalable Service: Able to monitor a wide range of systems across multiple locations and business units.
Disadvantages
MSSPs can overwhelm teams with low-risk, unactionable alerts and may lack deep investigative capabilities. Their reactive model often leaves gaps in threat detection and real time incident response.
- Alert Fatigue: Many MSSPs send high volumes of alerts without prioritization or resolution guidance.
- Limited Incident Response: Most MSSPs do not actively investigate or remediate threats.
- Minimal Context or Threat Intelligence: Lacks deep behavioural analysis and often does not integrate with modern telemetry sources like endpoints or cloud services.
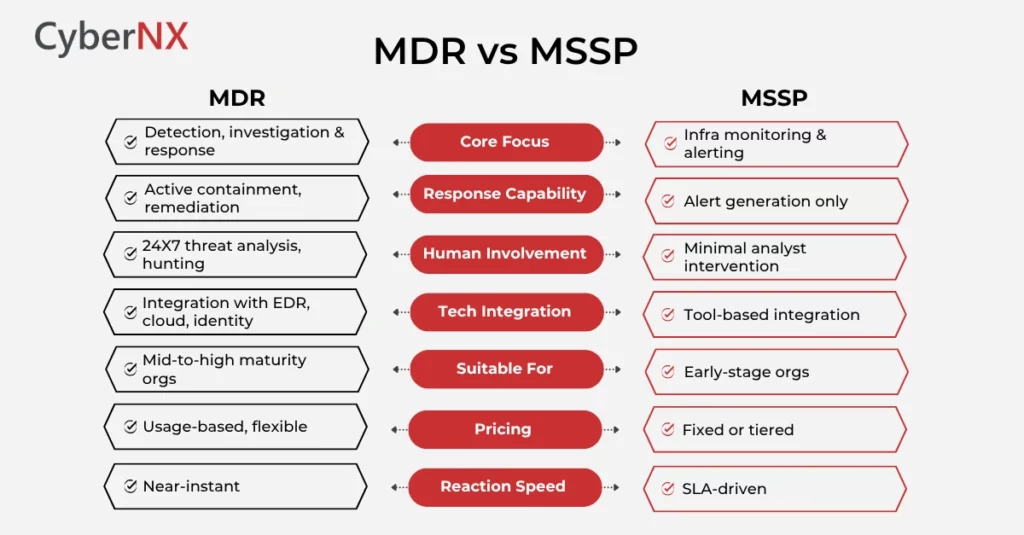
MDR vs MSSP: What are the Key Differences?
Both models may seem like offering external support for cybersecurity initiatives. But a closer look and you will realize that there are differences between MSSP and MDR. When incidents strike, the performance gap between MDR and MSSP cannot be ignored. This is where the discussion of managed detection and response vs mssp becomes crucial. Let’s see MDR vs MSSP differences from a strategic lens.
1. Service Offering
MDR is designed around response. It merges detection with investigation and action, providing a clear path from alerts to containments. MSSPs, in contrast, offer monitoring, event logging and compliance reporting, but often stop short of offering actionable insight or remediation.
2. Proactive vs Reactive
MDR proactively hunts threats, identifies early signs of compromise and initiates immediate response. MSSPs operate reactively, waiting for predefined threat signatures to trigger alerts and then passing the burden of action to your internal team.
3. Operating Model
MDR becomes an extension of your team. It integrates directly with your security stack, whether it’s EDR, cloud, or identity and operates in a 24X7 detection-response loop. MSSPs act more like third-party vendors with predefined SLAs and minimal environment-specific insight.
4. Pricing Model
MDR typically follows a usage-based pricing model, often determined by endpoints, data volume or incident complexity. It scales with your risk. MSSPs usually follow fixed pricing tied to services or device count, which can seem economical but may incur indirect costs during actual threat events due to delayed or limited response.
MDR vs MSSP: Comparison Chart
This chart breaks down the core differences between MSSP vs MDR across key areas It will help you the decision-makers quickly assess which service aligns better with your security priorities.
Conclusion
The MDR MSSP choice is ultimately about what kind of security partnership you want.
If you operate in a fast-moving, hybrid and high-risk environment, MDR offers sharper, faster and tailored defence. MSSPs still play a role, especially for businesses focused on foundational security and compliance.
But as threats evolve and boardrooms demand stronger risk visibility, MSSPs may not provide the level of active engagement required. MDR is the way ahead for stronger security posture for your organization.
Our MDR services involves advanced, in-built MDR platform with EDR, SIEM and SOAR tool integration, vast detection capabilities, global threat intelligence, AI powered function, cloud security and more. We offer 24X7X 365 security for your organization. Contact us today!
MDR vs MSSP FAQs
Can an organization use both MDR and MSSP services at the same time?
Yes. Many organizations use both, dividing responsibilities based on business needs. For instance, MSSPs can handle infrastructure monitoring, while MDR focuses on endpoint detection and threat response. This hybrid approach helps organizations balance cost, compliance, and active defence without overburdening internal teams.
Is MDR only suitable for large enterprises or can SMBs also benefit?
While MDR was initially adopted by larger organizations, many MDR providers now offer scalable solutions for SMBs. With cloud-based delivery and usage-based pricing, MDR brings advanced threat detection and response capabilities to smaller teams – especially those without dedicated SOCs or threat analysts.
How long does it take to switch from an MSSP to an MDR provider?
Transition timelines vary, but most organizations can shift within 30 to 90 days. The key steps include environment discovery, telemetry integration (EDR, cloud, etc.), and tuning detection logic. MDR providers often assist with onboarding, making the shift smoother than expected.
What certifications or frameworks should I look for in an MDR provider?
Look for providers with SOC 2 Type II, ISO/IEC 27001, and compliance alignment with NIST, MITRE ATT&CK, or CIS Controls. These frameworks ensure the provider follows structured, measurable, and recognized standards for threat detection and response.