In 2024, the cost of a data breach soared 4 million dollars. Perhaps, a grim reminder that digital blind spots can bankrupt biggest of business ambitions.
Today’s cyber attackers are not spreading random malware recklessly. Instead, they are far more patient, precise and often inside the systems long before you notice.
Now ask yourself: Who’s watching your network at 3 AM?
Firewalls are not chasing threats away. Antivirus does not think either. And your in-house team might be pre-occupied with a dozen things.
This is where Managed Detection and Response (MDR) tools step in, merging machine intelligence with human vigilance to detect, contain and shut down attacks in real time.
We had already discussed everything you need to know about MDR. Now let’s uncover the top 10 MDR tools defining 2026, so you can have the choice to outsmart, outpace and secure business.
What Are MDR Tools?
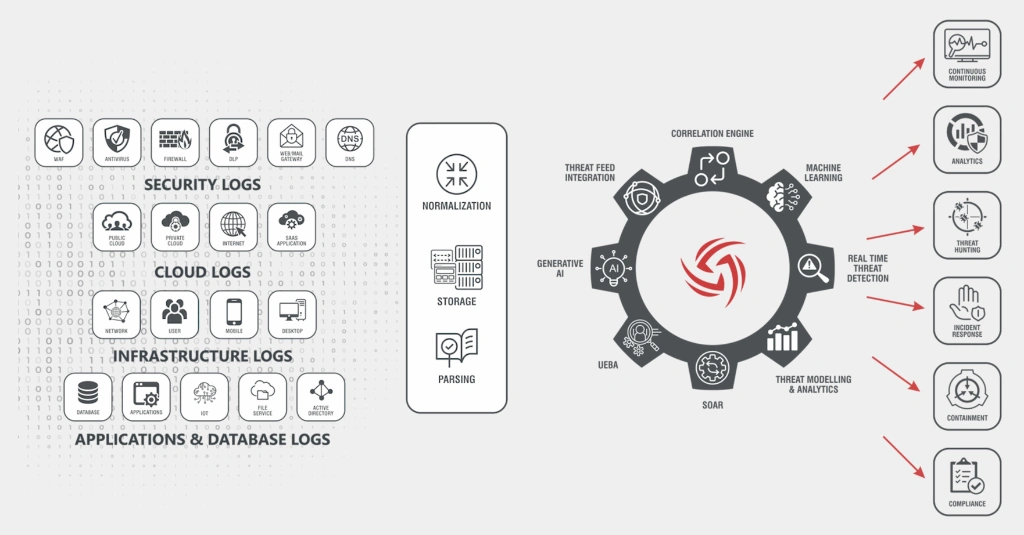
Managed Detection and Response tools are purpose-built cybersecurity solutions that are highly capable of detecting, investigating and neutralizing modern threats.
While traditional tools provide alerts, MDR tools go beyond and provide proactive monitoring, hunting and response as a managed service, bringing in skilled analysts 24X7. In short, MDR tools act, not just alert.
Going one step ahead, MDR tools are powered by AI, ML, curated threat intelligence and human security analysts. They scan beyond Endpoint Detection and Response (EDR) by covering multiple layers such as endpoint, network, cloud, identities and event logs.
Find below what MDR service typically delivers for a business:
- 24X7 monitoring of digital infrastructure
- Threat intel feeds and behaviour-based analytics
- Automated and manual threat hunting
- Incident investigation and root cause analysis
- Fast (near real-time) response and containment
- Compliance reporting and audit support
MDR Tools: Must-have Features
Assessing each of the tools and their providers isn’t an easy task. However, there are a few predetermined must-haves which can help you and your business to hire the right fit. We have listed them below for you:
1. Threat Intelligence Integration
MDR solutions should leverage global threat feeds and attack databases to detect emerging threats faster.
2. Proactive Threat Hunting
Rather than waiting for alerts, those MDR teams proactively looking for indicators of compromise across your environment deserves a further look.
3. Automation and Orchestration
Various tools now offer SOAR capabilities, which simply means automating repetitive tasks like quarantining infected devices, notifying teams or blocking IPs. This makes the whole process easier and better. So, that’s a clear must-have.
4. Skilled Security Analysts
Human expertise is key and necessary in the age of AI. If experienced security analysts are validating alerts, reducing false positives and guiding response – that’s where you should invest.
5. Compliance and Reporting
Dashboards and detailed reports help businesses meet regulatory requirements like GDPR, HIPAA, PCI-DSS, and more. It will make you and your compliance manager’s life a whole lot better.
Top MDR Tools to Know in 2026: The Ones That Matter
This is where you will find the highest-rated MDR tools 2026, making waves in 2026. There are hundreds of them worldwide, and the market is quite competitive. So, our experts have done rigorous research to list down the best mdr tools.
However, one that matters to your business might be cost-effective, scalable or just comprehensive. With that thought in the back of the mind, read on.
1. CyberNX Elastic Defend
One of the most advanced MDR services, CyberNX Elastic Defend is powered by EDR solutions, SIEM & SOAR platforms and other technology stack such as Cloud Security, User Behaviour Analytics and more.
The comprehensive detection platform monitors digital assets continuously. Plus, the advanced detection engine provides 24X7 visibility into existing and evolving threats and detailed view of malicious activities. One of the highlights include SOC cloud security monitoring that offers detailed view of cloud activities, configurations and more.
CyberNX Elastic Defend capabilities that you should know:
- AI Enabled Platforms & Investigations
- Advanced Threat Hunting
- Security Analytics
- Vast Detection Capabilities
- Cloud Security Posture and Risk Monitoring
- Digital & Brand Risk Monitoring
Key features include:
- MDR service is powered by commercial threat intelligence, gathered from global networks and enriched by the research team.
- Round-the-clock monitoring and response capabilities with follow-the-sun model ensuring organizations are always protected.
- Multi-tiered analyst structure ensures efficient triage, investigation and response with escalation paths to specialized experts when needed.
- Sophisticated behavioural analytics to identify anomalous activities that indicate potential threats, even when they do not match known signatures.
- Correlating signals across multiple data sources to identify complex attack patterns that would be missed when looking at individual alerts in isolation.
Contact CyberNX experts today to know in-depth about our MDR capabilities and how we are helping clients across India and abroad protect their digital infrastructure.
2. SentinelOne Vigilance Respond
A powerful MDR service indeed that integrates directly with their SentinelOne Singularity XDR platform. It provides 24X7 monitoring, expert-lead incident response and fast containment capabilities.
Arguably, one of their finest features is the automated active response. What it does is that it allows companies to isolate endpoints and roll back malicious changes – in quick time.
Key features include:
- Autonomous threat detection and remediation
- AI-powered threat analysis and story lining
- Seamless integration with existing security stacks
- Customizable reporting and compliance insights
3. CrowdStrike Falcon Complete
A trusted name in the security field, CrowdStrike combines its powerful EDR with a fully managed detection and response service. What does it cover? Endpoints, identity and cloud environments, offering a comprehensive XDR solution. In addition, a world-class team of threat hunters and analysts makes this tool excel in real-time response and forensic investigations.
Key features include:
- Real-time detection of ransomware and zero-day attacks
- Identity-based protection with integration across AD and cloud apps
- Elite Falcon Overwatch threat hunting team support
- 24/7 SOC coverage with guaranteed SLAs
4. Trend Micro
Another trusted MDR provider, it is well-known for offering a cohesive view across email, cloud, servers and networks. As far as MDR is concerned, it enables faster and accurate threat response as it is capable of fusing telemetry from different sources into one single investigation thread.
Trend Micro’s approach is focused on correlation, which it achieves by connecting dots across digital ecosystem and providing context-rich incident information and well-guided remediation.
Key features include:
- Detection across endpoint, cloud, email and network is possible
- Smart, contextual threat correlation reduces alert noise
- Experts deliver root cause analysis and response guidance
- Integrates easily with their Trend Micro Vision One platform
5. eSentire MDR
Mainly built for enterprises which need comprehensive visibility, it delivers threat detection, threat hunting and response across endpoint, network and cloud.
The platform includes its Atlas XDR engine and integrates third-party tools for end-to-end security.
Key features include:
- 24/7 global SOC operations
- Automated and human-led investigations
- Customized dashboards for reporting and compliance
- Sector-specific threat intelligence, ideal for finance and healthcare
6. ESET MDR
For ESET, MSPs and SMBs are their target customers. The tool combines its lightweight EDR with managed services, focusing mainly on affordability and ease of use.
Integration with Microsoft 365 and cloud workloads makes it ideal for hybrid and remote-first environments.
Key features include:
- Multi-tenant dashboard for MSPs
- Real-time alerting and triage
- Affordable pricing models for smaller organizations
- Built-in anti-ransomware and zero-trust features
7. Rapid7 Managed Threat Complete
Rapid7’s MDR is an exciting name, and they use Insight platform, which includes InsightIDR, InsightVM, and InsightConnect. This MDR tool is known for SIEM integration, deep user behavior analytics and SOAR capabilities that automate common workflows. They excel in securing what matters at affordable prices.
Key features include:
- Built-in orchestration to automate remediation
- Real-time detection based on user behavior analytics
- Native integration with vulnerability management
- Scalable for cloud and hybrid infrastructures
8. Sophos MDR
AI plus human threat detection capabilities is the mantra for Sophos MDR. It supports a bring-your-own telemetry model, allowing organizations to use third-party data sources.
Sophos also offers threat response services with full incident investigation and root-cause analysis.
Key features include:
- Threat resolution handled by Sophos experts
- Advanced AI-powered detections
- Option to retain full control or fully outsource SOC operations
- Endpoint, server, email, and network integration
9. Barracuda SKOUT Managed XDR
Clearly aimed at MSPs and mid-sized businesses, this MDR tool offers XDR-level capabilities with integrations across Microsoft 365, firewalls and endpoint solutions.
Key features include:
- Simplified dashboard for threat visibility
- Custom alerts and flexible integrations
- Email security and identity protection included
- Designed for ease of use in lean IT teams
10. Blackpoint Cyber MDR
It is essentially a threat-focused MDR platform with a background in offensive security. It uses patented SNAP-Defense technology to detect lateral movement and privilege escalation early.
Blackpoint is effective for organizations looking for internal network security.
Key features include:
- Real-time internal network monitoring
- Fast response from in-house cyber ops centre
- Built-in compliance reporting
- Affordable solution for SMBs and IT providers
MDR Tools Comparison Chart
This MDR tools comparison chart gives a quick overview of all the tools we have discussed.
| MDR Tool | 24/7 SOC | Cloud Support | Automation & SOAR | Threat Hunting | Best For | Unique Strength |
| CyberNX | ✅ |
✅ |
✅ |
✅ |
Business of any size | Advanced and Customized Services |
| SentinelOne Vigilance | ✅ | ✅ | ✅ | ✅ | Enterprises | Autonomous remediation with rollback |
| CrowdStrike Falcon | ✅ | ✅ | ✅ | ✅ | Enterprises, Hybrid Cloud | Identity protection with elite Overwatch team |
| Trend Micro | ✅ |
✅ |
✅ |
✅ |
Mid-market and Enterprises | Unified, correlated threat view across layers |
| eSentire | ✅ | ✅ | ✅ | ✅ | Regulated Industries | Vertical-specific threat intelligence |
| ESET MDR | ✅ | ✅ | ⚠️ Limited | ⚠️ Partial | SMBs, MSPs | Lightweight and affordable EDR integration |
| Rapid7 MDR | ✅ | ✅ | ✅ (Insight Connect) | ✅ | Cloud-Native Businesses | Deep user behaviour analytics and orchestration |
| Sophos MDR | ✅ | ✅ | ✅ | ✅ | SMBs to Enterprises | BYO telemetry, full incident resolution |
| Barracuda SKOUT XDR | ✅ | ✅ | ⚠️ Limited | ⚠️ Partial | MSPs, Mid-sized Businesses | Strong email + identity security integration |
| Blackpoint Cyber | ✅ | ✅ | ⚠️ Partial | ✅ | Internal Network-Focused Teams | Patented internal lateral movement detection |
✅ = Fully supported
⚠️ Partial = Some features available or depend on the plan
Choosing the Right MDR Tool: Align with Your Business Goal
Every organisation’s size, threat landscape and existing security maturity is different. Therefore, there is no one-size-fits-all approach to select the right MDR tool.
What matters here: Alignment with your business goal.
Large enterprises may benefit from deep integrations and customizable workflows, while small businesses often require affordability and ease of deployment.
Pay close attention to the balance between automation and human-led analysis in managed detection and response tools. Plus, ensure your provider offers support for your specific environment, cloud, on-premises or hybrid.
Conclusion
MDR tools fill the gap between prevention and incident response by offering businesses real-time visibility, expert threat analysis and automated or guided remediation. This makes best mdr tools a must-have in the modern threat environment.
And there are additional benefits such as better resilience, meeting compliance requirements and building trust with customers. Of course, you can do your own research besides these top 10 MDR tools, depending on your requirements.
If you are looking for MDR service provider, know that CyberNX is one of the trusted, leading and reliable names in the cybersecurity industry. Contact us today!
MDR Tools FAQs
How is MDR different from hiring an in-house security team?
While an in-house team offers control and on-site presence, MDR provides access to a global pool of elite security experts, advanced tools, and 24/7 monitoring – at a fraction of the cost. MDR also scales faster, responds in real-time, and brings threat intelligence most in-house teams can’t match.
Can MDR tools integrate with my existing security stack?
Yes. Most modern MDR tools are designed to integrate seamlessly with SIEMs, firewalls, EDR platforms, cloud providers, and identity systems. This enhances visibility and response without disrupting your current architecture or requiring a complete overhaul.
What industries benefit most from MDR tools?
While MDR adds value across all sectors, it’s especially impactful for industries facing regulatory pressure or high-value data risks—such as finance, healthcare, legal, retail, and critical infrastructure. Startups and SMBs also benefit by gaining enterprise-grade security without the headcount.
Do MDR tools help with cybersecurity compliance audits?
Absolutely. Many MDR tools offer audit-ready reporting, log retention, incident documentation, and mapped controls aligned with frameworks like GDPR, HIPAA, PCI-DSS, and ISO 27001 – streamlining compliance efforts and reducing the risk of regulatory penalties.