By the end of the year 2025, there will be 55 billion connected devices across the world. The staggering stat reveals one key fact: IoT (Internet of Things) devices are now truly and deeply embedded in every aspect of modern life.
These technologies do enhance efficiency and user experience, but they also expand the attack surface for threat actors exponentially.
As businesses, big and small, rush to innovate and advance, many might overlook security implications until it’s too late. This the reason why IoT penetration testing should be in your boardroom discussions and priority list today.
Additionally, business leaders should proactively test and secure the very systems powering their digital transformation. This IoT pentesting guide will help you do exactly that.
What is Internet of Things Penetration Testing?
The Internet of Things (IoT) refers to a vast network of physical objects such as devices, sensors, machines and software.
All of these connect and communicate over the internet. These objects collect, exchange and sometimes act on data, often autonomously.
Example: An ATM system of a bank may use embedded sensors, encrypted network communication and cloud-based analytics to identify possible tampering attempts, monitor cash levels and trigger proactive maintenance (without manual intervention).
A testing mechanism around the ATM system could prevent potential data breach or unwanted security incident.
That’s exactly the purpose of Internet of Things penetration testing: To uncover vulnerabilities across the IoT stack consisting of hardware, firmware, network protocols, cloud services, mobile interfaces and more, before real-world attackers do.
Want to know about other types of Penetration Testing? Check our blog: Types of Penetration Testing: A Complete Overview
When Should You Conduct IoT Penetration Testing?
Now that the knowing why part is done. Knowing when to test is just as critical. Your business can consider pen testing at these points:
- Before releasing a new IoT product or firmware update
- After a major architectural or software change
- Post a cyber incident involving connected assets
- As part of due diligence in M&A involving IoT infrastructure
- While doing annual security audits or compliance assessments
Types of IoT Penetration Testing
Based on where the IoT device is in the ecosystem, different testing types become important. We discuss the major ones here:
- Hardware Testing Analysis of the physical components like ports, chips and communication interfaces is done to find exploitable flaws.
- Firmware Testing This is focused on embedded software within the device. Because threat actors often try to reverse-engineer firmware with the aim of finding hidden credentials or backdoors.
- Network Testing It involves checking for vulnerabilities in communication protocols like MQTT, CoAP or HTTP. Also, it examines encryption and authentication.
- Application Layer Testing Mobile and web apps that interact with IoT devices are thoroughly reviewed. This is done because poor coding could bypass even the best device-level security.
- Cloud Interface Testing IoT devices interact with cloud dashboards. Therefore, this layer must be tested for broken authentication, exposed APIs and misconfigured permissions.
IoT Penetration Testing Methodology
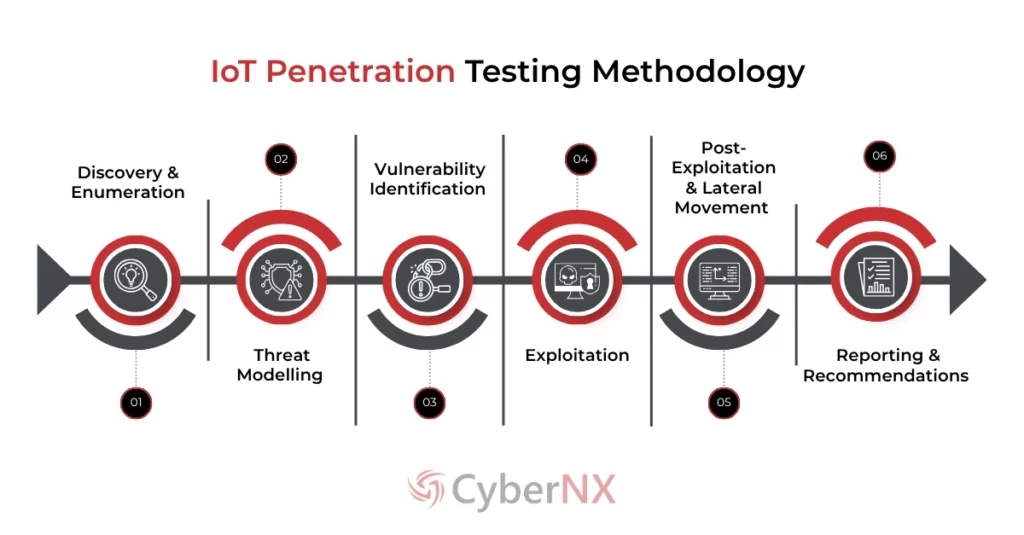
A well-structured Internet of Things penetration testing usually includes these stages:
- Discovery & Enumeration Identifies all connected devices and their interfaces (Bluetooth, Zigbee, Wi-Fi, etc.). A passive scanning is done to ensure no disruption happens to live systems.
- Threat Modelling This helps in understanding the context. What is the function of the device? Who are the users? Where does data flow? Answers to these questions help in prioritising risk-based testing.
- Vulnerability Identification Systems are checked for outdated firmware, insecure storage, hardcoded credentials or exposed ports. For this purpose, tools as well as manual methods are used.
- Exploitation In this stage, pentesters conduct controlled attacks simulating what real adversaries might do like hijacking a device to access internal networks.
- Post-Exploitation & Lateral Movement Once pentesters are inside, they explore if it is possible to move laterally across the network, reach sensitive data or escalate privileges.
- Reporting & Recommendations Results are compiled into a detailed report, highlighting risks in business-aware contexts and practical fixes are suggested.
OWASP Top 10 for IoT & Threat Examples
The OWASP IoT Top 10 lists the most critical vulnerabilities in IoT systems. Here’s a quick glance into them with real-world examples:
- Weak, Guessable, or Hardcoded Passwords Mirai botnet exploited default credentials in DVRs and routers.
- Insecure Network Services Open telnet ports expose embedded devices to remote attacks.
- Insecure Ecosystem Interfaces Poorly secured APIs and mobile apps lead to data leaks.
- Lack of Secure Update Mechanism Unverified OTA updates allow attackers to inject malicious firmware.
- Use of Insecure or Outdated Components Legacy libraries with known CVEs increase exposure.
- Insufficient Privacy Protection Wearables leaking GPS and health data due to lack of encryption.
- Insecure Data Transfer and Storage Unencrypted telemetry allows packet sniffing of sensitive data.
- Lack of Device Management No way to revoke, patch or monitor thousands of deployed devices.
- Insecure Default Settings Debug modes and verbose logs left enabled in production.
- Lack of Physical Hardening Attackers access debug ports like UART or SPI on circuit boards.
Challenges and Benefits: IoT Penetration Testing
pentesting IoT brings a unique set of challenges due to the diversity of devices, proprietary protocols and limited computing resources. Yet, the benefits far outweigh the hurdles. It helps organizations identify vulnerabilities early, strengthen compliance posture and build secure, resilient connected ecosystems, turning security into a competitive advantage. Find more about it below.
Why it’s Harder Than Regular Pentesting:
Internet of Things penetration testing presents several challenges.
First, device diversity makes the testing procedure complex. Each device may operate with different protocols, architectures and firmware, leaving no scope for one-size-fits-all approach.
Resource constraints further complicate matters. This is because many IoT devices lack the processing power or memory to support traditional security measures.
Additionally, third-party components such as open-source libraries or external modules integrated without assessment introduce potential vulnerabilities.
Finally, regulatory ambiguity across regions creates confusion about baseline security standards, making it difficult for organizations to ensure consistent compliance.
Strategic Value for Business Leaders:
- Prevents costly recalls, breaches and lawsuits for your business
- Builds consumer confidence and trust with secure products
- Accelerates compliance with standards like ISO/IEC 30141, ETSI EN 303 645
- Identifies hidden risks before attackers do, keeping you a step ahead of threat actors
- Becomes a key differentiator for your offering in a highly competitive market
Top 5 Tools for IoT Penetration Testing
- Shodan A well-known search engine for discovering internet-connected devices, Shodan is useful in the reconnaissance phase.
- Binwalk Binwalk extracts firmware images for analysis, thus helping to identify hardcoded secrets or misconfigurations.
- Firmware Analysis Toolkit (FAT) This tool automates firmware unpacking and emulation, eventually speeding up the analysis process.
- Wireshark A trusted tool worldwide, Wireshark is a powerful packet analyser that examines real-time data traffic. It is crucial for network layer testing.
- Burp Suite Another renowned security tool, it assesses the security of web applications and APIs interacting with IoT devices.
Conclusion
Every connected device today is a potential attack vector, and only proactive testing can protect your brand, users and bottom line. This IoT pentesting guide makes it quite clear.
Whether you’re deploying smart devices at scale or refining an existing product, penetration testing helps you launch with confidence, build trust and stay resilient. Therefore, IoT penetration test is a business-critical strategy.
CyberNX is a Cert-In Empanelled cybersecurity firm, offering IoT penetration testing services. To know about our full range of capabilities, contact us today.
IoT Penetration Testing FAQs
How does IoT penetration testing support regulatory compliance?
IoT penetration testing helps organizations meet compliance requirements such as GDPR, HIPAA, and ISO/IEC 30141 by validating the security of data handling, communication protocols, and device controls. It provides evidence-based assurance that connected systems adhere to required cybersecurity and privacy standards—essential for risk management and audit readiness.
How is IoT penetration testing different from traditional penetration testing?
IoT penetration testing is fundamentally more intricate than traditional testing. While standard pen tests focus on web apps, networks and APIs, IoT testing spans a broader ecosystem that includes hardware components, embedded firmware, device-level memory, and unique communication protocols like MQTT or Zigbee. It often requires physical access, custom hardware tools, and a deep understanding of constrained environments, making it more specialized and multi-dimensional.
When should a company perform IoT penetration testing?
The ideal time include just before product release, after firmware or software updates, during annual security reviews, or after integrating third-party components. It’s also critical post-incident, when compliance deadlines approach, or when scaling deployments. Regular testing ensures that evolving threats don’t outpace your defences, especially in devices expected to stay in use for years without regular patching.
What should business leaders look for in an IoT penetration testing provider?
Choose a provider with proven expertise across the full IoT stack—hardware security analysis, firmware reverse engineering, wireless protocol exploitation, and secure OTA update assessments. Ask for real-world case studies, methodologies tailored to your industry, and clarity in reporting that links vulnerabilities to business impact. Bonus points if they help prioritize fixes based on exploitability and operational risk.