HBOM vs SBOM is a question we hear more often now. And it usually comes from organisations dealing with both software risk and physical infrastructure risk. Cloud-first companies are asking it. So are manufacturers, banks, and critical infrastructure providers.
SBOMs gained attention first, largely due to software supply chain attacks and regulatory pressure. HBOMs followed quietly, driven by hardware tampering risks, firmware vulnerabilities, and the growing overlap between IT and OT environments.
The confusion is understandable. Both sound similar. Both aim to improve visibility. Yet their scope, ownership, and implementation approach differ significantly.
This guide breaks down HBOM vs SBOM in practical terms. We look at what each one covers, where they matter most, how they support compliance, and how to implement them without creating process overload.
What SBOM really covers
SBOM stands for Software Bill of Materials. It is an inventory of all software components used in an application or system.
An SBOM typically includes:
- Open source and third-party libraries
- Application frameworks and modules
- Versions and dependency relationships
- Licensing information
- Known vulnerabilities mapped to components
SBOMs are most effective when generated automatically and updated continuously.
Why SBOM matters today
Modern software is rarely built from scratch. Most applications rely heavily on reused components. Without an SBOM, teams often struggle to answer basic questions during incidents.
- Which applications use a vulnerable library?
- Where is the affected version deployed?
- Who owns remediation?
SBOMs make those answers visible.
What HBOM really covers
HBOM stands for Hardware Bill of Materials. It focuses on physical and embedded components.
An HBOM may include:
- Hardware components and part numbers
- Chipsets, processors, and memory modules
- Firmware versions
- Suppliers and manufacturers
- Country of origin data
HBOMs are especially relevant in environments where hardware integrity directly affects safety, uptime, or compliance.
Why HBOM is gaining attention
Hardware supply chains are complex and global. Risks include counterfeit components, unauthorised modifications, and outdated firmware.
As IT and OT environments converge, hardware visibility becomes a security requirement, not just a procurement concern.
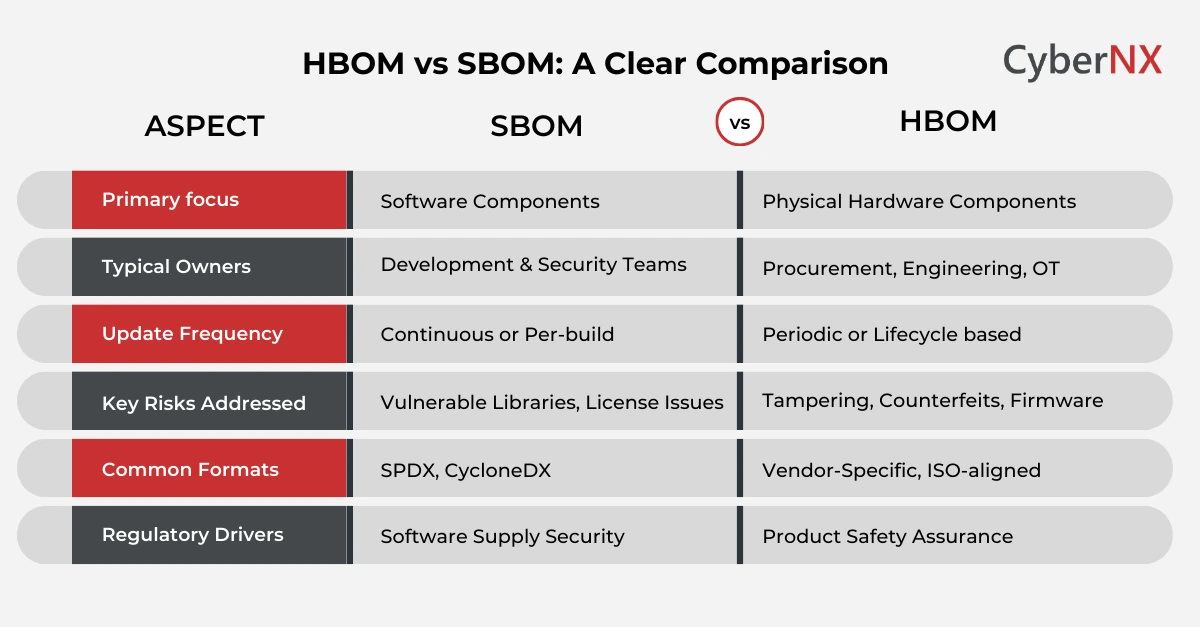
HBOM vs SBOM: Core differences explained
Before implementation, it helps to see how HBOM vs SBOM differs at a fundamental level.
Both matter. They simply answer different questions.
Where HBOM vs SBOM fits in real-world environments
When you discuss HBOM and SBOM, it is important to know where they could be helpful.
1. Pure software organisations
SaaS providers and digital-native companies often start with SBOMs only. Hardware risks still exist, but they are usually abstracted by cloud providers. In these cases, SBOM implementation delivers faster value and clearer ownership.
2. Enterprises with hybrid environments
Banks, telecoms, and large enterprises operate across software platforms and physical infrastructure. Here, SBOM and HBOM complement each other. An application may be secure at code level but exposed due to outdated firmware on underlying hardware.
3. OT and critical infrastructure
Manufacturing, energy, and transport sectors often prioritise HBOMs first. Safety, uptime, and regulatory scrutiny drive the need for hardware transparency. SBOMs still matter, especially where embedded software is involved.
HBOM implementation: what changes
HBOM implementation follows a different rhythm. HBOMs often integrate with:
- Procurement systems
- Asset inventories
- Maintenance and lifecycle management tools
They evolve more slowly than SBOMs but require strong supplier coordination.
Hardware without firmware visibility creates blind spots. HBOMs should link hardware components to firmware versions and update histories. This linkage becomes vital during vulnerability disclosures affecting hardware platforms.
Compliance and audit perspective
HBOM vs SBOM becomes especially relevant during audits.
1. SBOMs and regulatory expectations
Regulators increasingly expect software supply chain transparency. SBOMs help demonstrate:
- Secure development practices
- Third-party risk awareness
- Ongoing vulnerability monitoring
For Indian enterprises, SBOMs support expectations from bodies like CERT-In and sectoral regulators.
2. HBOMs and assurance requirements
HBOMs support:
- Product integrity verification
- Supply chain traceability
- Safety and reliability audits
They are often reviewed during operational risk and compliance assessments rather than application security audits.
Do you need both HBOM and SBOM?
The honest answer is often yes, but not at the same time or with the same depth. Start with the area of highest risk. Build maturity there. Then expand. Many organisations begin with SBOMs due to immediate software risk. HBOMs follow as environments mature and hardware visibility gaps become clear.
Conclusion
HBOM vs SBOM is not about choosing one over the other. It is about understanding what risk you are trying to manage.
SBOMs bring clarity to modern software complexity. HBOMs strengthen trust in physical and embedded systems. Together, they form a more complete picture of supply chain risk.
At CyberNX, we help organisations design SBOM and HBOM strategies that fit their operating reality, regulatory environment, and growth plans. If you are evaluating where to start or how to scale, our SBOM management tool can save months of trial and error. Speak to our team to know more about our BOM capabilities and build supply chain visibility that works.
HBOM vs SBOM FAQs
Can HBOM and SBOM data be combined?
Yes. Some organisations link HBOM and SBOM data through asset management platforms to gain end-to-end visibility.
Are HBOMs relevant for cloud environments?
Indirectly, yes. While cloud providers manage hardware, regulated customers may still require assurance documentation.
Who should own HBOM governance?
Ownership often sits across procurement, engineering, and security teams, with clear accountability defined.
Is SBOM mandatory today?
Mandates vary by sector and geography, but expectations around SBOM adoption are increasing rapidly.