Hardware risk is no longer theoretical. It is operational.
Organisations rely on servers, network devices, endpoints, IoT equipment, and specialised appliances. Yet many security teams still lack a clear view of what hardware actually exists inside their environments. Components are sourced globally. Firmware is updated irregularly. Third-party suppliers change quietly.
HBOM addresses this gap.
A Hardware Bill of Materials gives organisations a structured way to understand the physical components that make up their hardware assets. It brings visibility to chips, modules, firmware, and embedded components that often sit outside traditional security inventories.
In this blog, we explain what HBOM is, where it came from, and how it helps organisations manage hardware supply chain risk with more confidence.
HBOM origins
HBOM emerged from the same pressure that drove SBOM adoption, but with a hardware specific focus.
As global supply chains expanded, hardware manufacturing became more distributed. A single device could include components from dozens of vendors across multiple countries. This complexity increased exposure to counterfeit parts, tampering, undocumented changes, and firmware vulnerabilities.
High-profile supply chain incidents accelerated regulatory and industry attention. Governments and enterprises realised that understanding software alone was not enough. Hardware components, firmware, and embedded systems also needed transparency.
HBOM draws inspiration from traditional bills of materials used in manufacturing. It adapts those principles to cybersecurity by documenting hardware components in a structured, machine-readable way. Over time, HBOM has become a foundational concept for hardware assurance, especially in regulated and critical sectors.
What is HBOM?
HBOM stands for Hardware Bill of Materials.
It is a detailed inventory of the physical and logical components that make up a hardware product or system. This includes not just the finished device, but also its internal building blocks and dependencies.
Typical components captured in an HBOM
An HBOM can include:
- Processors, chipsets, and microcontrollers
- Memory modules and storage components
- Network interfaces and radios
- Embedded firmware and bootloaders
- Sensors, controllers, and peripheral modules
- Manufacturer and supplier details
- Version, model, and serial information
Unlike asset registers, HBOM goes deeper. It describes how hardware is composed, not just what device is deployed.
HBOM and firmware visibility
One critical aspect of HBOM is firmware awareness. Many hardware vulnerabilities originate in BIOS, UEFI, BMCs, and device firmware. HBOM helps security teams:
- Identify firmware versions in use
- Track update status and patch gaps
- Correlate firmware vulnerabilities to affected devices
This level of insight is difficult to achieve without a structured hardware inventory.
HBOM versus other BOMs
HBOM does not replace other bills of materials. It complements them.
- SBOM focuses on software components and libraries
- CBOM focuses on cryptographic assets
- HBOM focuses on physical hardware and embedded elements
Together, these BOMs provide a more complete view of technology risk across the stack. HBOM fills the gap that software-centric approaches cannot cover.
How HBOM helps your business
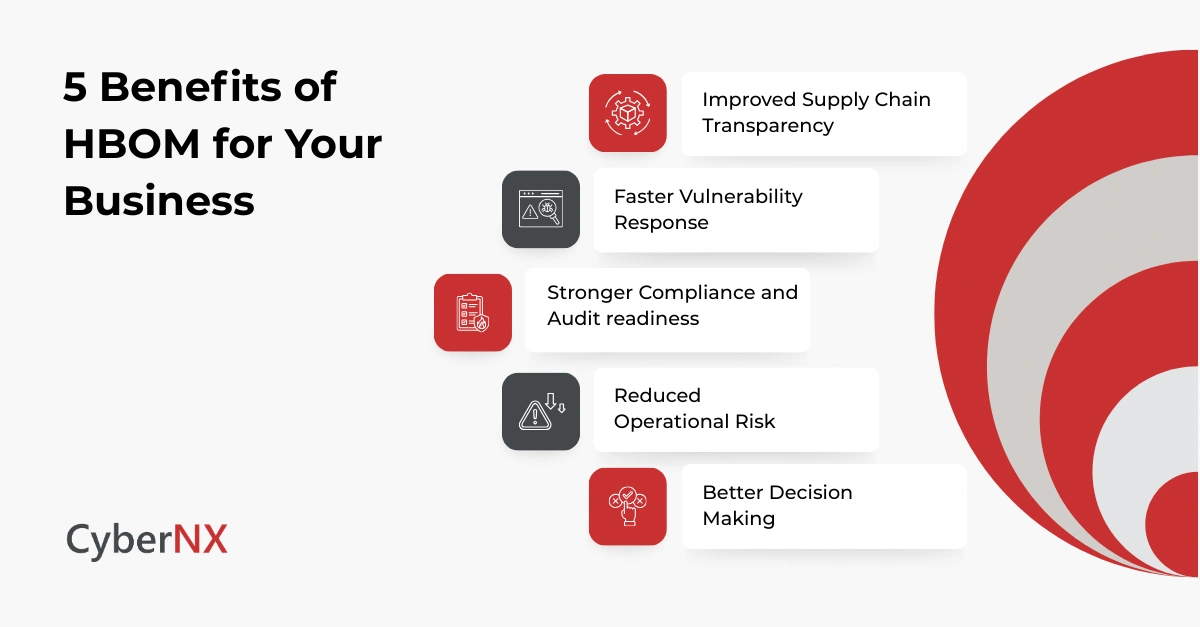
HBOM delivers value across security, compliance, and operations.
1. Improved supply chain transparency
HBOM helps organisations understand where hardware components originate and how they are assembled. This supports supplier risk assessments and reduces reliance on incomplete vendor declarations.
2. Faster vulnerability response
When a hardware or firmware vulnerability is disclosed, HBOM enables quicker answers to critical questions:
- Which devices contain the affected component?
- Where are they deployed?
- Which firmware versions are exposed?
This shortens response time and limits business impact.
3. Stronger compliance and audit readiness
Regulators and auditors increasingly expect evidence of hardware supply chain controls. HBOM provides structured documentation that supports due diligence, procurement reviews, and compliance reporting.
4. Reduced operational risk
Undocumented hardware changes and unknown components increase downtime risk. HBOM improves lifecycle management by supporting:
- Safer upgrades and replacements
- Better spare part planning
- Clearer end-of-life tracking
5. Better decision making
With HBOM, leaders can prioritise investments based on actual hardware exposure rather than assumptions. This leads to more targeted security controls and smarter procurement strategies.
Practical considerations for adopting HBOM
HBOM works best when treated as an ongoing capability rather than a static document.
- Start with critical systems: Focus first on infrastructure that supports sensitive data or core business functions.
- Leverage vendor collaboration: Many manufacturers already maintain internal BOMs. Aligning formats and expectations reduces effort.
- Integrate with asset and risk management: HBOM should feed into existing inventories, vulnerability management, and risk workflows.
- Plan for updates: Hardware evolves over time through replacements, repairs, and firmware changes. HBOMs must be refreshed accordingly.
Conclusion
HBOM brings long overdue visibility to hardware risk. It helps organisations understand what their devices are truly made of, not just what labels say on the outside.
As supply chains grow more complex and hardware attacks become more realistic, HBOM provides a foundation for trust, resilience, and informed decision making. It complements software and cryptographic inventories, completing the picture of modern technology risk.
At CyberNX, we help you align with security, compliance, and operational goals. Contact us today and our experts will guide you on SBOM, CBOM and HBOM generation.
HBOM FAQs
Is HBOM only relevant for large enterprises?
No. While large enterprises feel the impact first due to scale, HBOM is equally valuable for mid-sized organisations using third-party hardware, cloud infrastructure, or specialised devices. Any organisation with supplier dependency benefits from hardware transparency.
Does HBOM require deep access to manufacturer designs?
Not always. HBOM can start with high-level component and firmware information shared by vendors. Over time, maturity increases through supplier contracts, attestations, and verification processes rather than full design disclosure.
How often should an HBOM be updated?
HBOMs should be updated whenever there is a hardware change, firmware upgrade, component replacement, or supplier shift. For critical infrastructure, periodic reviews are recommended even without visible changes.
Can HBOM support incident response?
Yes. During hardware or firmware-related incidents, HBOM helps responders quickly identify affected devices, understand component dependencies, and assess potential impact, reducing investigation time and uncertainty.