Unprecedently fast and increasingly sophisticated, cyberattacks take only minutes to happen now. Your traditional detection tools operating in silos, missing context and slow response could not match the threat actors of today. Organizations, therefore, need smarter, faster and integrated security solutions.
Extended Detection and Response – an evolution of EDR – is a cybersecurity force multiplier, in the words of Enterprise Strategy Group (ESG). Because it unifies visibility, detection and response across your entire digital environment, making security operations cohesive, effective and efficient.
What is the Concept of Extended Detection and Response?
Extended Detection and Response with the popular and widely used acronym XDR is a modern, unified and comprehensive threat detection and response approach in security.
When compared to Endpoint Detection and Response (EDR), XDR is holistic with wider coverage and better integration capabilities. Plus, it is infused with:
- Advanced attack chain visibility
- AI and automation
- Data analytics
- Vast threat intelligence
What does this mean for security teams and organizations? For one, XDR goes beyond traditional endpoints like servers, devices and covers cloud workloads, hybrid systems and email. It collects and correlates data from these multiple layers to provide comprehensive threat detection and streamlined incident response, boosting the efficiency of SOC teams.
Also, Extended Detection and Response works independently and delivers a connected, cross-layered approach with a centralized platform. It means, SOC teams do not have to switch from one tab to another.
Additionally, XDR helps organizations with deeper visibility, richer context and faster, automated responses, enabling them to combat modern and sophisticated threats and attacks.
What are the Benefits of XDR?
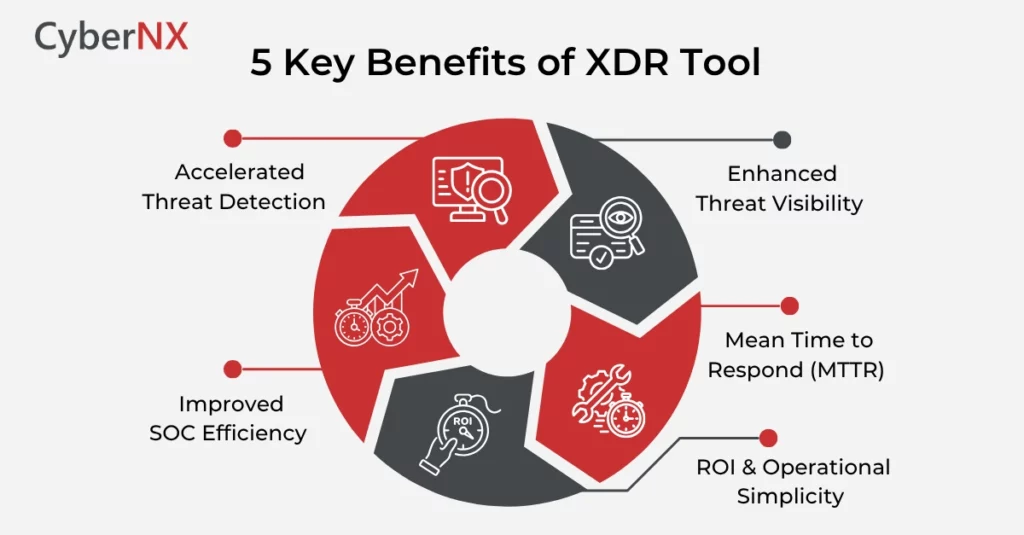
Extended Detection and Response offers a holistic approach to security with faster detection, deeper context and automated response capabilities. Here’s how organizations benefit:
1. Accelerated Threat Detection
Real time correlation of signals across domains via XDR tool enables early threat detection. This is critical when dealing with advanced persistent threats (APTs) that are designed to evade traditional security tools. Plus, because a threat is detected early, attacker’s opportunity to exploit the system reduces drastically.
2. Improved SOC Efficiency
XDR automates many of the repetitive and time-consuming tasks, often done by security teams. Centralized dashboard also gives SOC teams a single, comprehensive view, boosting efficiency while responding to critical threats faster. This time could be allocated for higher-value activities, innovations and other projects.
3. Enhanced Threat Visibility
When the entire IT ecosystem is covered by XDR, it means that your security team has horizontal and vertical visibility. Horizontal includes assets and domains whereas vertical includes depth of activity, user behaviour and device posture. This comprehensive view makes sure that no stealthy tactics or sneaky techniques can go undetected.
4. Mean Time to Respond (MTTR)
Perhaps the most valuable metric for SOC teams, MTTR is reduced with XDR’s automation, intuitive investigation and immediate response features. Whether it is auto-isolating endpoints or triggering playbooks, every second saved helps contain threats before damage spreads.
5. ROI and Operational Simplicity
XDR tool’s integrated system feature replaces the patchwork of multiple security tools within an organization. Less tools means less complexity, easier maintenance and a lower total cost of ownership. For growing organizations, this means scaling security without scaling teams at the same pace and scaling efficiently.
How XDR Works?
XDR tools utilize latest AI and analytics capabilities to monitor entire digital environment, identify the incidents and present high-fidelity alerts to security teams in shortest time. Here’s how it works:
1. Data Collection
XDR ingests from multiple telemetry sources/security layers such as endpoints, network, identity, cloud, email, etc. What differentiates XDR is that it integrates across the ecosystem. And an advanced XDR tool should be capable of integrating innovative technologies that come.
2. Data Normalization & Correlation
Next up, the raw data collected is normalized and correlated using pre-defined detection rules, behavioural analytics and threat intelligence. The organized and standardized data of high quality across multiple domains help security teams spot sophisticated, multi-vector threats.
3. Threat Detection
With AI-powered analytics, curated and rich contextual data is made available. XDR detects both known and unknown threats accurately, reducing false positives. This makes the work of SOC analysts smarter and faster.
4. Incident Investigation & Prioritization
Extended Detection and Automation (XDR) automatically relates suspicious events to create end-to-end attack stories or attack chains and presents them in a centralized hub. Security teams thus get a clear and contextual view, enabling faster triage and helps in carrying our root cause analysis.
5. Automated & Manual Response
XDR combines automated playbooks (like isolating a device or disabling user credentials) and manual response capabilities via a unified console. This means response to major cyberthreats is made possible. Plus, it helps in reviewing incident response reports and recommend appropriate measures to prevent future incidents.
5 Unique XDR Features
What makes Extended Detection and Response (XDR) stand out? It stops cyber-attacks in the shortest time possible. Here are five core capabilities that define an effective XDR platform:
1. Unified Data Integration
Extended Detection and Response (XDR) consolidates data across endpoints, servers, cloud workloads, identity systems, and more. Security teams get a comprehensive view of potential attacks instead of disparate and random data, making threat detection and response faster and productive.
2. Cross-layer Visibility
Because XDR tools break silos and offer correlated views across multiple domains, SOC analysts are able to catch modern cyberattacks. For example, XDR can correlate a suspicious file download on an endpoint with a related unauthorised login from an unusual location. This massively improves cross-layer visibility and saves time, which is not possible with domain-specific tools.
3. Advanced Analytics
Using behavioural analytics, heuristics and pre-defined detection rules, the Extended Detection and Response tool identifies lateral movement, privilege escalation and other complex attack techniques. This is all possible even for cyberattacks, which are happening in real time. Plus, it also supports root cause analysis to pinpoint how an attack unfolded for analysts to study and learn.
4. Artificial Intelligence and Machine Learning
XDR platforms employ AI models to automate detection, response and mitigation of possible attacks. This is achieved by using AI to monitor unknown threats, reducing false positives and sending alerts that matter. Machine Learning capabilities allow XDR tools to gather global threat data and past incidents, enabling smarter and more adaptive detection.
5. Automated Response Workflows
XDR’s inclusion of pre-configured playbooks and customizable automation workflows makes the life of security teams easy. They rapidly contain threats such as isolating infected endpoints, resetting credentials and blocking IP addresses, with minimal manual intervention.
XDR vs Other Detection and Response Tools
Let’s compare how XDR stacks up against EDR, MDR, and NDR:
| Feature | XDR | EDR | MDR | NDR |
|---|---|---|---|---|
| Scope | Multiple domains (endpoint, network, cloud, etc.) | Endpoints only | Managed detection & response across client tools | Network traffic only |
| Visibility | Cross-layer | Endpoint-centric | Depends on MDR vendor | Network-centric |
| Automation | High (built-in workflows) | Medium (mostly manual) | High (outsourced) | Low |
| Centralized Console | Yes | No | Depends on provider | No |
| Threat Context | High | Limited | Moderate to High | Low |
| Best For | Medium to large orgs with internal SOC | Organizations focused on endpoint protection | SMBs or teams lacking internal security | Organizations needing network visibility |
Top XDR Tools
Several cybersecurity vendors have come up with XDR innovations, offering robust platforms that unify and enhance threat detection and response.
There is CrowdStrike Falcon XDR, known for its seamless integration of telemetry from endpoints, cloud workloads, and identity systems, all backed by reliable threat intelligence.
Microsoft Defender XDR with native integration across the Microsoft ecosystem makes it ideal for organizations.
Meanwhile, Palo Alto Cortex XDR also brings together endpoint, network, and cloud telemetry with advanced behavioural analytics and machine learning for high-fidelity threat detection.
To learn more, read our detailed, expert-reviewed blog on Top XDR Tools.
How to Choose the Best XDR Tool?
The right XDR tool will impact detection speed, your security team’s productivity and overall security posture. Here’s what to evaluate when considering choosing the best Extended Detection and Response tool:
1. Native and Third-Party Integrations
First, always ask what native integrations the XDR solution supports. Does it include your core infrastructure that consists of endpoints, cloud workloads, email systems, firewalls and identity platforms? Additionally, ask if the XDR solution is future-ready to ingest data from existing and new third-party tools.
2. Use Case Alignment
Every business has different security needs. Also, different XDR platforms offer varying depth across domains. Choose the XDR tool that aligns with your highest priority use case. It does not matter how big or successful the solution provider is; whether it fulfils your needs like cloud threat detection, lateral movement tracking, or ransomware containment should be the priority.
3. Quality of Detection and Intelligence
If you are investing in an XDR tool, you must know its capabilities. So, do not hesitate to ask about the source for threat intelligence and how they are proactive with detection techniques. Technically, your security teams should inquire about pre-built analytics, rule sets and behavioural models. This is important because it drastically affects the outcome.
4. Automation & Orchestration Capabilities
Examine how the Extended Detection and Response platform handles response automation, a key aspect in security. Does it support customizable playbooks? Can it integrate with SOAR systems for orchestrated responses? Robust automation is a major force multiplier, easing the SOC teams and boosting efficiency.
5. Cost, Licensing and Support
Consider the total cost of ownership, not just licensing. Evaluate onboarding complexity, analyst training, support responsiveness and ongoing tuning requirements. It is necessary to know what is included and the support expected.
Implementation Strategies for XDR
You might ask – Why is an implementation strategy required for Extended Detection and Response? The answer is to extract the maximum value of your investment. Here’s how to approach XDR implementation:
1. Infrastructure and Gap Assessment
Start by mapping your current security tools, telemetry sources, coverage gaps and business priorities. Identify siloed tools that are not of much help and let XDR replace or consolidate them.
2. Define Clear Objectives and Use Cases
Defining clear objectives and use cases like ransomware prevention, phishing detection, and privilege escalation helps in configuring detection rules and response playbooks inside XDR software.
3. Integrate with SOC Processes
Ensure your SOC team is skilled and knowledgeable to implement and operationalize the XDR tool. Analysts can be trained on the console, playbooks and investigation tools. Also, update incident response plans to initiate automated actions.
4. Track KPIs and Improve
Establish Key Performance Indicators (KPIs) such as MTTR, false positive rate, dwell time or analyst time saved. Use these metrics to measure ROI and continuously improve the platform’s configuration to maximize impact.
What is Managed XDR?
Managed XDR, abbreviated as MXDR, is a service-based approach to Extended Detection and Response. This involves a third-party vendor who packs XDR technology with expert-driven threat monitoring, investigation and response services together. It is suitable for organizations that require advanced protection with tools like XDR but without the complexity of managing it in-house.
In this model, the provider takes control of alert triage, conducts in-depth investigations and executes response actions based on predefined rules or collaborative workflows. Managed XDR benefits organizations with limited internal resources, such as SMBs or enterprises without a fully staffed Security Operations Center (SOC).
Conclusion
XDR may sound like a buzzword for the unheard. But it is the next generation of detection and response, apt for the complexity of modern IT environments.
Our XDR services enable faster, automated and more accurate threat response, and empower your security teams to stay ahead of adversaries, always. Contact us today.
Extended Detection and Response (XDR) FAQs
Can XDR help detect insider threats or account compromise?
Yes. XDR is particularly effective at detecting insider threats and account compromises because it correlates behaviour across multiple domains—like unusual access patterns in identity systems, suspicious file downloads, or lateral movement within the network. By analysing this behaviour in context and applying user behaviour analytics (UBA), XDR can surface subtle threats that might otherwise go unnoticed.
Is XDR suitable for small or mid-sized businesses without a dedicated SOC?
While XDR platforms are often adopted by larger enterprises, many vendors offer managed XDR (MXDR) solutions that are tailored for small and mid-sized businesses. These services combine XDR technology with outsourced monitoring, enabling smaller teams to benefit from advanced threat detection and response without building a full-scale SOC internally.
How does XDR reduce alert fatigue compared to traditional tools?
Traditional security tools often flood analysts with isolated alerts that lack context, making it hard to differentiate real threats from noise. XDR addresses this by correlating alerts into unified incidents, showing how events are linked in an attack chain. This dramatically reduces redundant alerts, helping analysts focus only on high-fidelity threats.
Can XDR replace EDR or SIEM entirely?
XDR can complement or even replace EDR in many cases since it includes endpoint telemetry as part of its broader detection scope. However, it is not a full replacement for SIEM, especially when it comes to long-term log storage, regulatory compliance, or broad IT operations monitoring.
Find out the intricate details of how SIEM works with our blog SIEM Guide.
In many environments, XDR and SIEM work best together, with XDR enhancing real-time threat detection and SIEM handling audit and compliance needs.