Log volumes keep rising, cloud environments keep expanding and attackers keep changing tactics. Yet many organisations still rely on SIEM platforms designed for a different era. But successful and cybersecurity-conscious companies don’t.
This is where the debate around Elastic SIEM over traditional SIEM tools becomes important. Decision-makers are no longer asking which SIEM has more features. They are asking which platform adapts better to change, scales without painful cost spikes, and supports modern detection without locking teams into rigid vendor models.
In this blog, we explore how Elastic SIEM compares with traditional SIEM platforms, focusing on cost, scalability, AI-driven detection, compliance realities, and long-term operational impact. We also explain why it differs from other traditional SIEM platforms.
Cost and licensing models: flexibility versus fixed commitments
Cost is often the first friction point in SIEM conversations. It is also where the contrast becomes obvious.
Elastic SIEM pricing philosophy
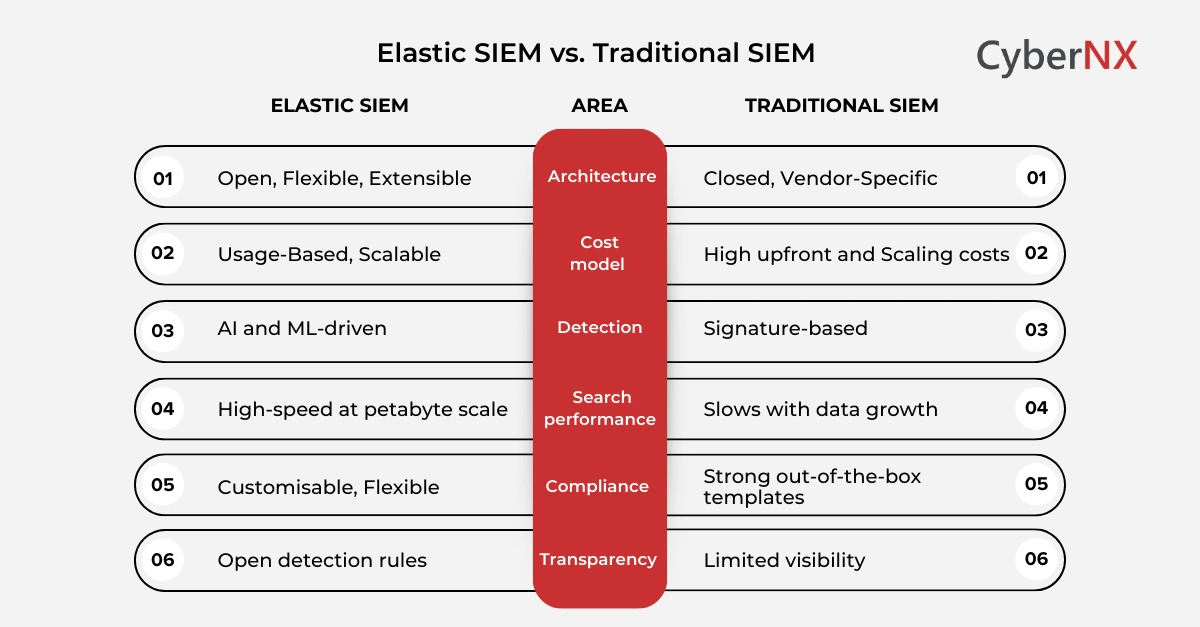
Elastic SIEM is built on open-source foundations. Organisations can start without licensing fees and scale gradually as needs evolve. You pay for what you use, whether that is advanced security features or managed services through Elastic Cloud.
This model suits growing environments. It also supports experimentation. Teams can test new detection ideas without renegotiating contracts or forecasting hardware upgrades months in advance.
Traditional SIEM cost structure
Traditional SIEM platforms like Splunk and IBM QRadar typically require high upfront investment. Licensing is often tied to data volume. Storage expansion means new hardware and additional licences.
Over time, this can limit visibility. Teams reduce log ingestion to control costs. That trade-off directly impacts detection quality.
Scalability and performance at enterprise scale
As data volumes grow, performance becomes a security issue, not just a technical one.
Elastic Stack performance model
Elastic SIEM is built on Elasticsearch, designed for high-speed search across massive datasets. It supports federated search, allowing analysts to query cloud and on-prem environments simultaneously without moving data.
This creates a live search layer across environments. Investigations stay fast, even at petabyte scale.
Performance limits in traditional SIEMs
Many traditional SIEM platforms slow down as databases grow. Queries take longer. Correlation becomes resource-heavy. Analysts wait for results while threats continue to move.
When response speed matters, this delay becomes costly.
Customisation versus out-of-the-box completeness
Security teams differ in maturity, skills, and priorities. SIEM platforms respond to this reality in very different ways.
Elastic’s custom-first approach
Elastic SIEM is highly customisable. Teams can adjust ingestion pipelines, build tailored dashboards in Kibana, and inspect or modify open-source detection rules.
This transparency builds trust. Analysts know exactly how detections work and why alerts trigger.
Traditional SIEMs as packaged solutions
Traditional SIEMs are often described as complete straight out of the box. Event correlation, alerting, and incident workflows are prebuilt.
This works well for teams seeking immediate structure. However, flexibility is limited to what the vendor allows. Deep customisation often requires professional services.
Detection capabilities and the role of AI
Detection quality defines the value of any SIEM.
Signature-based detection limits
Traditional SIEM platforms rely heavily on predefined rules and signatures. These are effective for known threats but struggle with new attack paths and subtle anomalies.
Alert fatigue becomes common. Analysts spend time triaging noise rather than investigating risk.
Elastic’s AI-driven evolution
Elastic integrates machine learning and agentic AI to support modern SOC operations.
Agentic AI correlates signals across data sources, suggests remediation steps, and automates parts of response. Analysts stay in control, but manual correlation drops sharply.
Conversational AI allows natural language investigation. Analysts can ask questions instead of writing complex queries. Retrieval Augmented Generation grounds responses in your own data, playbooks, and past incidents.
Elastic AI SOC Engine extends these capabilities even into existing SIEM deployments. This allows teams to modernise without immediate migration. This approach helped Elastic earn recognition as a Visionary in the 2025 Gartner Magic Quadrant for SIEM.
Open source, transparency, and community trust
Trust in detection logic matters, especially during incidents.
Open detection rules
Elastic publishes its detection rules openly. Analysts can review, adapt, and improve them. This openness encourages peer review and faster improvement. Community-driven innovation means defences evolve alongside real-world threats, not vendor release cycles.
Closed vendor ecosystems
Traditional SIEM vendors protect intellectual property by design. Detection logic often remains opaque. Customisation stays constrained. For highly regulated teams, this can limit confidence and slow response.
Unified architecture and federated search
Modern environments are fragmented. SIEMs must reduce that complexity, not add to it.
Elastic unifies SIEM, XDR, and cloud security on a single stack. Data ingestion happens once. Analysts move across use cases without switching tools.
Federated search allows live querying across clouds and on-prem clusters. There is no need to centralise or duplicate data. Elastic focuses on building attack narratives, not isolated alerts. Signals become context. Context becomes action.
Compliance realities: structure versus flexibility
Compliance remains a deciding factor for many organisations.
Out-of-the-box compliance strengths
Traditional SIEM platforms excel here. They offer preconfigured templates for GDPR, HIPAA, PCI DSS, and similar frameworks. Audit preparation becomes faster and more predictable.
Built-in archiving supports long-term retention without additional design work.
Elastic SIEM compliance flexibility
Elastic SIEM supports basic reporting but often requires custom dashboards for specific regulations. For experienced teams, this flexibility enables tailored audits and complex compliance needs. Searchable snapshots support long-term retention on cost-effective storage tiers, allowing years of data to remain searchable without rehydration.
Elastic is also progressing in regulated sectors, with FedRAMP High In Process designation supporting public sector adoption.
Lower TCO and operational simplicity
When we step back, cost and complexity shape long-term success. Elastic reduces total cost of ownership through infrastructure consolidation and flexible storage tiers. Automatic import and migration tools reduce onboarding effort.
Traditional SIEMs reduce setup effort initially but often increase long-term cost and rigidity. This is why many organisations are evaluating Elastic SIEM over traditional SIEM tools as part of their security transformation roadmap.
Concise comparison table
Conclusion
Choosing a SIEM is not about features alone. It is about alignment with how your organisation grows, investigates, and responds.
Elastic SIEM offers flexibility, transparency, and modern AI-driven detection. Traditional SIEM platforms deliver structure and compliance readiness. The right choice depends on your maturity, resources, and long-term vision.
At CyberNX, we help organisations assess, implement, and optimise SIEM platforms with clarity and confidence. If you are evaluating modernisation or hybrid approaches, we would be glad to support you.
Talk to us for managed SIEM services that fits your risk profile and growth plans.
Elastic SIEM over traditional SIEM tools FAQs
How long does it take to deploy Elastic SIEM?
Deployment time depends on data sources and use cases. Many teams achieve initial visibility within days, with advanced detections built over weeks.
Can Elastic SIEM replace an existing SIEM completely?
Yes, but many organisations choose phased adoption, running Elastic alongside existing platforms before full migration.
Is Elastic SIEM suitable for small SOC teams?
Yes. Its scalability and flexible pricing support both lean teams and large enterprises.
How does Elastic handle insider threat detection?
Elastic analyses behavioural anomalies across users, endpoints, and transactions to surface insider risk signals.