Most cybersecurity breaches originate at endpoints such as laptops, workstations, servers and mobile devices. Today, the attack surface is also expanding with remote work, BYOD and cloud-first environments.
So, how do you protect endpoints which are no longer confined to office walls? By shifting discussions in the boardroom from “Do we need endpoint security?” to “Which EDR tool is best for defending your organization in the digital age?”
Endpoint Detection and Response (EDR) is a must-have for modern defence. Because it offers immense capabilities ranging from threat detection and deep visibility to swift remediation and forensic-level insights.
Based on our professional experience in the industry, peer reviews and customer talk points, we have curated this EDR tools list. Depending on your requirements, these EDR tools can strengthen your organizational security posture.
What is an EDR Tool?
Before jumping into the EDR tools list, find out what is EDR tool and how it helps security teams.
An Endpoint Detection and Response (EDR) tool is designed to detect, investigate and respond to suspicious activities or anomalous behaviour across endpoints in real time. It gathers rich telemetry, from processes, behaviours, file activity, and applies advanced analytics to uncover both known and novel threats.
Unlike traditional antivirus, which operates on signature-based detection, EDR solutions look for behaviours, lateral movement, privilege escalation and persistence mechanisms, offering security teams the context they need to act quickly and decisively.
Related Content: Endpoint Detection and Response (EDR): The Cornerstone of Modern Cyber Defence
How EDR Tools Work?
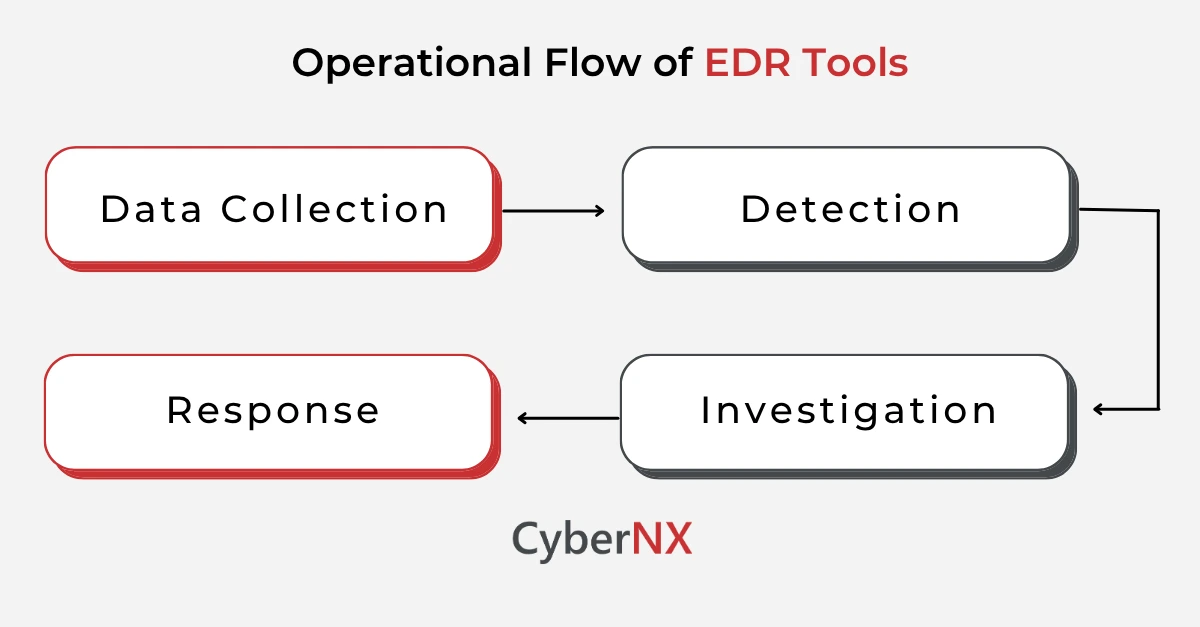
EDR platforms with specialized sensors are active participants in threat defence. Their operation generally follows four phases:
- Data Collection: Real-time data collection from endpoints—covering applications, memory, network activity, registry, and user behaviour.
- Detection: Use of behavioural analytics, AI, machine learning, and threat intelligence to spot anomalies and malicious activities.
- Investigation: Offering contextualized alerts, attack timelines and forensic details to trace threats to their source.
- Response: Containment of infected endpoints, terminating malicious processes and bringing back systems to pre-infection states automatically.
This powerful system minimizes the dwell time of threat actors inside your system and enables fast remediation.
Top 10 EDR Tools List in 2026
Here is our top EDR tools list for 2026 and beyond.
1. CyberNX
CyberNX is one of the trusted, reliable and fast-growing endpoint security solution providers. We have made our name in the field because of many factors. For one, we offer high precision & fast detection plus actionable response capabilities which are scalable as per business needs. We realize that our customers want best of security at the best price. As our clients grow, their security needs also grow proportionally. And we also make sure to scale our capabilities to support them always.
Thanks to the number of advanced features such as AI powered investigations, security analytics, User Behaviour Analytics, cloud security posture monitoring and more. The EDR offering, as part of the Elastic Defend MDR platform, acts something similar to a co-pilot for security operations.
Key Features that make CyberNX stand out:
- Tailored for Regional Threats: CyberNX gathers contextual threat intelligence from world’s trusted and best networks, local APT behaviour and regional sector vulnerabilities from across the world, providing relevant and low-noise detection.
- EDR + MDR Synergy: CyberNX embeds Managed Detection and Response (MDR) into its agile platform. This means that security professionals at organizations get expert-led monitoring, continuous threat hunting and proactive incident management.
- Real-Time Threat Containment: With automated, analyst-led and community-driven playbooks, compromised endpoints are isolated instantly before attackers could do anything and cause business disruption.
- Zero Complexity Deployment: Lightweight agents across endpoints, cloud-first architecture and policy templates make onboarding seamless, even for lean IT teams.
- Compliance-Centric: Supports compliance for BFSI, healthcare and government sectors plus align with ISO 27001, PCI DSS, and CERT-In requirements.
CyberNX experts understand the infrastructure, risk posture and budget boundaries. That’s why majority of our clients trust and rely on us. Enterprise-grade protection without bloated pricing makes us ideal for IT leaders/business heads.
2. CrowdStrike Falcon
Second on our EDR tools list is CrowdStrike. They have a cloud-native EDR with lightweight agent, threat graph correlation engine and real-time response. Their AI-driven detection and extensive telemetry offer good support to mature SOCs. Integration with threat intelligence and incident response playbooks also enhances post-detection agility.
3. Cynet 360 AutoXDR
Cynet’s EDR tool offers EDR, NGAV, deception and user behaviour analytics in a single platform. The key features include automation-first design, where response workflows can isolate machines, disable user accounts and trigger alerts without human intervention. It is ideal for small to mid-sized teams wanting breadth in their security.
4. Sophos Intercept X
Sophos Intercept X combines deep learning and anti-exploit technology. The key feature of their CryptoGuard ransomware rollback is protecting files and endpoints from encryption-based attacks. With synchronized security integration across firewall, email and mobile, the EDR tool is well-suited for companies looking for cohesive endpoint protection.
5. SentinelOne Singularity
SentinelOne EDR tool is known for autonomous remediation and rollback capabilities. Its behavioural AI engine operates at machine speed, neutralizing threats without needing cloud queries. It also offers zero-trust posture, container visibility and rich forensic context.
These top 5 names in our EDR tools list are enough to make your choice. However, different vendors offer unique features. And you might possibly need one of those to fix your unique security case. So, we have added 5 more EDR tools for you to have a look.
6. FortiEDR
Part of Fortinet’s security ecosystem, FortiEDR excels in pre-execution detection and real-time event correlation, stopping threats before they could materialize into breaches. With native integration into FortiGate firewalls and FortiAnalyzer, it supports a unified security architecture.
7. Cortex XDR (Palo Alto Networks)
EDR tool is embedded into the Cortex XDR from Palo Alto Networks. It merges data from network, endpoint and cloud sources into a single investigative timeline. Additionally, ML-driven analytics reduce alert fatigue and offers guided investigations.
8. Microsoft Defender for Endpoint
Defender EDR tool supports automated investigation, threat intelligence correlation and vulnerability management, all within the Microsoft 365 security suite. For companies working with the Microsoft ecosystem, it delivers strong protection.
9. Symantec Endpoint Security (Broadcom)
Symantec offers multi-layered EDR features, including deception, risk scoring and app control. Its Global Intelligence Network helps with precise detection, especially for fileless threats and PowerShell-based exploits.
10. Trellix
Trellix blends McAfee’s prevention tools with FireEye’s advanced threat detection for its EDR platform. The dynamic telemetry, integrated sandboxing and adaptive response mechanisms make it suitable for large-scale SOC environments.
How to Choose the Best EDR Tool?
Every organization is different. What works for a multinational may overwhelm a mid-size firm. Here’s how to make your decision:
- Detection Capabilities: Look for tools with behaviour-based, signatureless, and AI/ML-driven detection to capture advanced threats.
- Response Speed: Automated response workflows, rollback features, and endpoint isolation can drastically reduce incident impact.
- Integration Flexibility: Ensure the tool integrates with your existing SIEM, firewall, IAM, and cloud platforms.
- Ease of Use: Dashboards, policy management, and alert investigation should be intuitive, especially if your team isn’t SOC-heavy.
- Support & Services: Some vendors offer MDR as a service, which can be a game-changer for overburdened internal teams.
Some of the overlooked factors include your budget, sensitivity of your systems and criticality of information you are trying to protect. Consider these factors and go through our EDR tools list to make the final decision.
What Are Open-Source EDR Tools?
Open-source EDR tools are customizable and have budget options. However, these free EDR tools often lack the capabilities of commercial, enterprise-grade platforms discussed previously.
Here is a chart comprising the top free/open-source EDR tools available online, their key features and limitations.
| Tool | Key Features | Best For | Limitations |
| OSSEC | Host-based IDS, log analysis, rootkit detection | SMBs, compliance-focused | No real-time response |
| Wazuh | SIEM + EDR, agent-based monitoring, cloud support | Mid-size environments | Complex configuration |
| Security Onion | EDR + NIDS/NIPS, Elastic Stack integration | Research, MSPs | Heavy system requirements |
| Velociraptor | Endpoint visibility, threat hunting, IR tools | Blue teams, researchers | Steep learning curve |
| GRR Rapid Response | Forensics and live response toolset | DFIR professionals | Less intuitive for beginners |
Foresight: What’s Next for EDR Tools?
While we discuss and ponder over existing EDR tools list and their features, threat actors might be adopting stealthier techniques and AI-generated malware, this very minute. So, it is important to understand the next evolution of EDR.
According to our in-house detection and response experts:
- EDR will move towards proactive detection powered by machine learning and large language models (LLMs). Conventional EDRs rely on rules, signatures and behaviour patterns, and attackers are easily slipping past them using memory-only payloads, DLL injections and even EDR evasion frameworks like HookChain.
- To achieve “the next” for EDR tools, many vendors have started experimenting with LLM-driven threat detection, where AI models analyse live endpoint telemetry, command-line behaviour and even human-like attacker tactics in real time. This allows the system to predict malicious intent, even before the code is executed.
- Soon, LLMs may be able to reason through them like analysts, explaining attack paths, suggesting response actions and learning from every incident.
CyberNX is closely following this evolution, exploring how generative AI can further help security teams simulate evasive attacks, generate synthetic IOCs and augment threat hunting with intelligent automation.
Conclusion
Are you aiming to safeguard an enterprise or an agile tech startup? In the current threat environment where cyberattacks are sophisticated, discrete in approach and targeting every kind of business, choosing the right EDR tools in cyber security can make or break your incident response readiness.
CyberNX’s EDR services offers localized intelligence, real-time response and human-backed expertise, making it a security leader for organizations in India and beyond seeking practical and scalable protection across endpoints. Contact us today!
EDR Tools FAQs
Can EDR security tools detect insider threats?
Yes. Modern EDR platforms analyse user behaviour and access patterns, allowing them to flag unusual internal activity, often the hallmark of insider threats.
Are cloud-based EDR tools secure for sensitive environments?
Cloud-native EDR solutions use encrypted communication, data isolation, and compliance-ready frameworks to secure even highly regulated environments like healthcare and finance.
What’s the difference between EDR and antivirus?
While antivirus tools scan files for known signatures, EDR tools monitor behaviours, analyse system events, and offer real-time response capabilities – even against unknown threats.
Is EDR enough, or do I need XDR too?
EDR focuses on endpoints. XDR extends visibility across email, identity, cloud, and network layers. If your environment is complex and multi-vector attacks are a concern, XDR offers a broader defence. Learn everything about the modern endpoint security tool with our blog XDR guide.