Imagine launching your new web app and assuming that it is secure (because the code looks clean). But it is like a bank with strong walls with the assumption that no one will barge through the door. Well, cyber attackers can.
Dynamic application security testing or DAST is like a professional who acts like a burglar to test the strength of your bank and in this case like a hacker, trying to breach into your app.
Irrespective of how the app was built or the code used, DAST experts poke and prod to break into the system. And one thing that sets it apart is that testing happens when the app is running.
This comprehensive guide will explore everything you need to know about DAST, from fundamental concepts to implementation strategies and future trends.
What is Dynamic Application Security Testing?
Dynamic application security testing (DAST) is a Black Box Security Testing methodology that examines applications in their running state. Unlike other testing approaches that require access to source code, DAST works from the outside in, simulating the actions of a malicious attacker to identify vulnerabilities that could be exploited in a real-world scenario.
DAST tools operate by sending various HTTP requests to web applications and analysing the responses for security issues through DAST automated test. This approach allows security teams to discover vulnerabilities that might not be apparent through static code analysis, such as authentication problems, server configuration errors, and input validation flaws.
5 Key Benefits of DAST Implementation
Dynamic Application Security Testing (DAST) helps identify runtime vulnerabilities in web applications by simulating real-world attacks using dynamic application security testing software. It enhances security posture, ensures compliance, and reduces the risk of breaches in production environments.
1. Real-World Vulnerability Detection
By simulating actual attack scenarios, dynamic application security testing identifies vulnerabilities that could be exploited by real attackers. This approach provides a practical assessment of your application’s security posture rather than theoretical risks.
2. Language-Agnostic Testing
Since dynamic application security testing works from the outside in, it doesn’t depend on the programming language or framework used to build your application. This versatility makes it ideal for testing diverse application portfolios with multiple technologies.
3. Reduced False Positives
Compared to other testing methods, DAST typically produces fewer false positives because it verifies vulnerabilities in the running application. This saves security teams valuable time that would otherwise be spent investigating non-issues.
4. Pre-Production Security Validation
Implementing dynamic application security testing in pre-production environments allows teams to identify and fix vulnerabilities before applications go live, preventing potential breaches and associated costs.
5. Compliance Support
Many regulatory frameworks and industry standards require regular security testing. DAST helps organizations meet compliance requirements by providing documented evidence of security testing and vulnerability management.
Common DAST Challenges and Mitigation Strategies
While dynamic application security testing offers significant benefits, organizations may encounter challenges during implementation. Understanding these obstacles and how to overcome them is crucial for success:
Challenge 1: Authentication Complexity
Problem:
DAST tools may struggle with complex authentication mechanisms, limiting their ability to test protected areas of applications.
Solution:
Use DAST tools that support various authentication methods, including cookie-based, form-based, and API token authentication. Configure pre-authentication scripts to ensure comprehensive coverage of secured application areas.
Challenge 2: Performance Impact
Problem:
Intensive scanning can affect application performance, potentially disrupting user experience in production environments.
Solution:
Schedule scans during off-peak hours or implement them in staging environments that mirror production. Consider incremental scanning approaches that distribute the testing load over time.
Challenge 3: Business Logic Vulnerabilities
Problem:
Standard DAST tools may miss vulnerabilities related to application-specific business logic.
Solution:
Supplement automated DAST with manual penetration testing for critical applications. Use modern DAST tools that support custom scripts to test application-specific workflows and business rules.
How Does DAST Work?
Understanding the mechanics behind dynamic application security testing helps organizations implement it effectively. The Dynamic Application Security Testing process typically follows these key steps:
1. Scanning
DAST tools begin by crawling the application, mapping all accessible pages, links, forms, and entry points. This creates a comprehensive view of the application’s attack surface.
2. Analysis
As requests are sent, the tool analyses responses for anomalies, error messages, and unexpected behaviour that might indicate vulnerabilities.
3. Attack Simulation
The scanner simulates various attacks like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) to identify security weaknesses.
4. Vulnerability Identification
When potential vulnerabilities are detected, the DAST tool records their location and response for further investigation.
5. Reporting
Finally, the tool generates detailed reports outlining discovered vulnerabilities, their severity, and potential attack scenarios to guide remediation efforts.
Since DAST operates without knowledge of the application’s internal workings, it provides an authentic perspective on how attackers might exploit vulnerabilities in your running application through DAST dynamic application security testing.
7 Best Practices for Effective DAST Adoption
Implementing dynamic application security testing successfully requires a strategic approach. Follow these best practices to maximize the effectiveness of your Dynamic Application Security Testing program:
1. Integrate DAST into CI/CD Pipelines
Automate security testing by incorporating DAST into your continuous integration and delivery workflows. This ensures that every code change is automatically scanned for vulnerabilities before deployment.
2. Prioritize Critical Applications
Start by implementing dynamic application security testing for your most business-critical and high-risk applications. This focused approach allows you to address the most significant security concerns first.
3. Combine with Other Testing Methods
Use DAST alongside SAST, SCA, and manual penetration testing for comprehensive coverage. Each method catches different types of vulnerabilities, creating a more robust security posture.
4. Test in Pre-Production
Run DAST scans in staging or QA environments that closely mirror production. This allows you to identify and fix vulnerabilities before they reach production without affecting live systems.
5. Establish Remediation Workflows
Create clear processes for addressing discovered vulnerabilities, including severity-based prioritization, assignment protocols, and verification procedures.
6. Train Development Teams
Educate developers about common web application vulnerabilities and secure coding practices. This proactive approach reduces the number of security issues introduced during development.
7. Monitor and Measure
Track key metrics like vulnerability detection rates, remediation times, and security debt to measure the effectiveness of your DAST program and identify areas for improvement.
Real-World Examples: DAST Preventing Breaches
E-Commerce Platform SQL Injection Prevention
A major e-commerce platform implemented DAST as part of their security program and discovered a critical SQL injection vulnerability in their product search functionality. The vulnerability could have allowed attackers to access customer data, including payment information.
By identifying and patching this issue before it was exploited, the company avoided a potential data breach that could have affected millions of customers and resulted in significant financial and reputational damage.
Banking Application XSS Vulnerability
A financial institution’s regular DAST scan identified a cross-site scripting (XSS) vulnerability in their online banking portal. This vulnerability could have allowed attackers to inject malicious scripts and steal user credentials.
The security team quickly remediated the issue, preventing a potential attack that could have compromised customer accounts and led to financial fraud.
Healthcare Portal Authentication Bypass
A healthcare provider’s DAST implementation detected an authentication bypass vulnerability in their patient portal. This security flaw could have allowed unauthorized access to sensitive medical records.
By discovering and fixing this issue during pre-production testing, the organization prevented a potential HIPAA violation and protected patient privacy.
Top 5 DAST Tools in 2026
| Tool | Best For | Key Features | Integration Capabilities | Pricing Model |
| StackHawk | DevOps, CI/CD teams | API testing, automation, dev-friendly UI | CI/CD tools, issue trackers, Slack | Free & paid plans |
| OWASP ZAP | Budget-conscious teams | Open-source, plugins, active community | Jenkins, GitHub Actions, Docker | Free |
| Burp Suite Professional | Security pros, manual testers | Proxy, manual testing tools | CI systems, extensions | One-time purchase + annual renewal |
| Acunetix | Enterprise with large-scale needs | AcuSensor tech, low false positives, reporting | DevOps tools, vuln. Mgmt. systems | Enterprise licensing |
| Netsparker | Large orgs needing scan validation | Proof-Based Scanning™, WAF, compliance reports | SDLC tools, issue trackers, WAFs | Subscription-based |
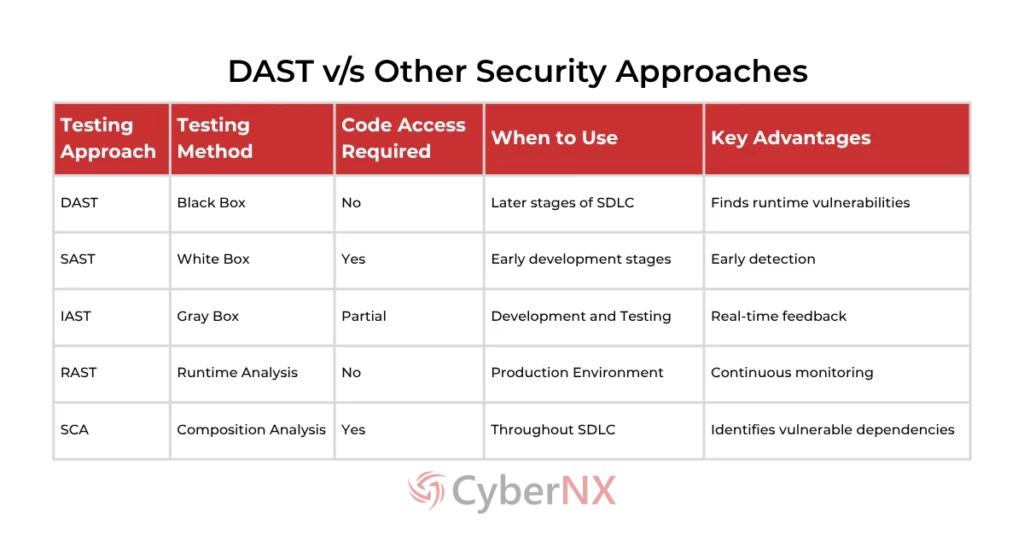
DAST vs. Other Security Testing Approaches
To build a comprehensive application security strategy, it’s important to understand how dynamic application security testing compares to other testing methodologies:
While each testing approach has its strengths, many organizations implement multiple methodologies for comprehensive coverage. DAST complements static application security testing (SAST) particularly well, as SAST identifies issues in the source code while DAST catches vulnerabilities that only appear during runtime.
Future Trends in DAST Technology
DAST is evolving with AI-driven vulnerability detection, deeper integration into CI/CD pipelines, and improved coverage of modern web technologies. These advancements aim to deliver faster, smarter, and more continuous security testing.
AI and Machine Learning Integration
Artificial intelligence and machine learning are revolutionizing DAST by improving vulnerability detection accuracy, reducing false positives, and enabling more intelligent scanning.
API Security Focus
As organizations increasingly rely on APIs for critical business functions, DAST tools are evolving to provide better API security testing capabilities.
Shift-Left Integration
DAST tools are becoming more developer-friendly and integrated earlier in the software development lifecycle, aligning with shift-left security principles.
Continuous Testing
Organizations are moving toward continuous DAST, providing real-time feedback on application security posture.
Automated Remediation
Advanced DAST tools are beginning to offer automated remediation suggestions and even code fixes for common vulnerabilities.
Conclusion
Dynamic application security testing is a critical component of a comprehensive application security program. DAST provides unique insights into security vulnerabilities that might otherwise go undetected until exploitation.
DAST serves as a powerful complement to other testing methodologies like SAST and SCA too, strengthening DAST application security.
By following the best practices outlined in this guide, organizations can significantly strengthen their security posture and protect sensitive data from increasingly sophisticated cyber threats.
CyberNX is a leading, trusted and experienced dynamic application security testing company, helping hundreds of clients protect their business. Want to know how we do it? dynamic application security testing.
Dynamic Application Security Testing FAQs
What types of vulnerabilities can Dynamic application security testing detect?
Dynamic application security testing can detect a wide range of vulnerabilities, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), insecure server configurations, authentication issues, and most of the OWASP Top 10 vulnerabilities.
When should Dynamic Application Security Testing be performed in the development lifecycle?
While DAST can be performed at various stages, it’s most effective when implemented in pre-production environments that closely mirror production.
How does Dynamic Application Security Testing differ from penetration testing?
DAST is typically automated and focuses on identifying known vulnerability patterns, while penetration testing involves human testers and can uncover complex, chained vulnerabilities.
Can DAST be used for mobile applications?
Yes, specialized DAST tools are available for mobile applications, particularly for testing backend services and APIs.
How often should DAST scans be performed?
For frequently updated applications, integrate DAST into CI/CD pipelines. Stable applications can be tested monthly or quarterly. Critical apps should be tested more often.