Adversaries today are always on the lookout to exploit that one vulnerability or stolen credential to hack into your systems, potentially causing irrevocable damage to your critical infrastructure. That’s why it is important to always plug the gaps across the endpoints and focus on detection and response mechanisms.
In this context, EDR and XDR solutions provide a massive boost for modern security operations. However, their capabilities, scope and strategic value for businesses differ. In this blog, we will focus on what is difference between EDR and XDR, their capabilities and factors you must consider while choosing an approach that best aligns with your security needs.
What is EDR?
To understand Endpoint Detection and Response (EDR), first, you need to know what endpoints are. They are nothing but devices like laptops, PCs, smartphones and IoT devices connected to the corporate or company network. Now, all these are important components of infrastructure.
EDR, developed to overcome the limitations of antivirus, emerged as a trusted security solution capable of monitoring, detecting, investigating and responding to any and every possible suspicious activity on endpoints.
To offer in-depth visibility of your environment and to detect compromises, EDR tools collect data from endpoints, analyse behaviour patterns using User Behaviour Analytics and trigger alerts in real time of possible threats.
Key capabilities of EDR include:
- Monitoring of endpoint risks and resultant activities plus prioritising remediation
- Threat detection based on data received and assessed from behavioural analytics
- In-depth investigation and early detection of attack chain visibility
- A blend of manual expertise and automated response capabilities
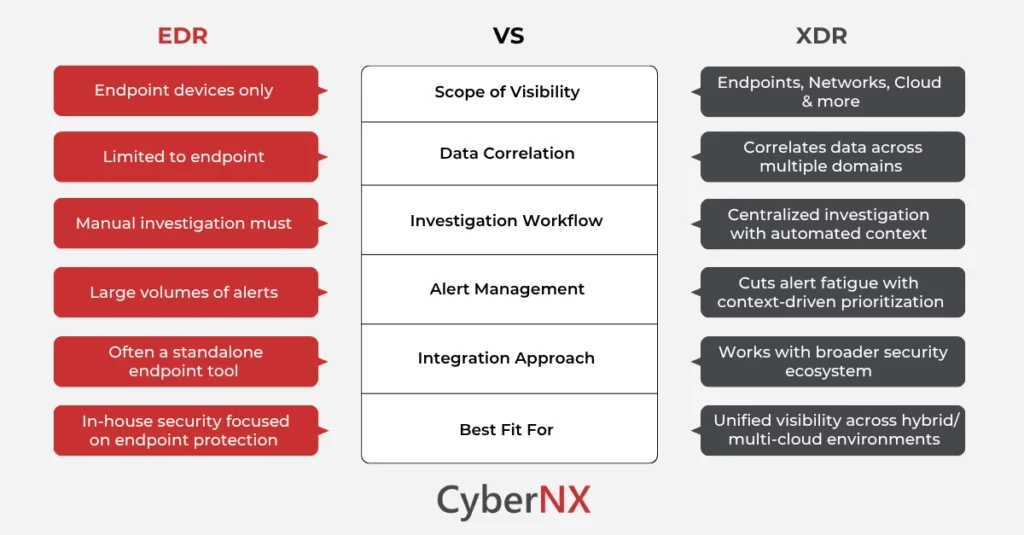
EDR tools give security teams much-needed visibility into endpoints and the people using them, enabling effective incident response. However, EDR has limitations. It can detect and respond against threats only on individual devices.
What if your business has a broader IT infrastructure that includes networks, cloud and email? What if you need insights across the digital ecosystem and want overarching protection? That’s where XDR comes into the picture.
Read our blog EDR Guide where we have covered everything in-depth from its benefits, challenges and workflow to implementation process, how to choose an EDR vendor and more.
What is XDR?
Extended Detection and Response (XDR), in one sense, can be described as a massive update on EDR with extended features and detection capabilities.
XDR clearly distinguishes itself from other solutions by collecting and correlating telemetry from multiple sources. what is XDR vs EDR It consists of endpoints, networks, cloud platforms, identity systems, and emails. If you see, modern enterprises today function using all these components. Thus, XDR offering a centralized view of weak points across the enterprise, is a boost for security teams.
Key capabilities of XDR include:
- Unifies threat detection and response across diverse systems in your organization
- Reduces alert fatigue through correlation and context, giving breathing room for security teams and lets them focus on innovation
- Gives a massive boost to investigation speed and accuracy, much-needed in high-stakes environments
- Automates response across environments, preventing security teams from engaging in repetitive tasks and focusing rather on productive things
XDR, in effect, is an integrated detection and response platform, highly capable of offering a comprehensive and cohesive picture of threats to the security team of your organization.
Read our XDR Guide to know everything about this tool.
Quick Glance at the Difference Between EDR and XDR
Here is a quick glance at what differentiates XDR vs EDR based on different parameters:
Choosing Between EDR and XDR
Choosing either EDR or XDR entirely depends on what your business is aiming for in the context of your current security posture.
Common factors which are considered by IT leaders include company size, IT environment complexity, maturity level of internal security and existing detection and response capabilities.
Here, our experts offer a simple overview of when to use what.
- Go for EDR if your infrastructure is endpoint-centric, if you need next-level security strategy with device-level visibility or if your team is experienced in manual investigation.
- XDR would be more suitable if your organization operates in hybrid or multi-cloud environments, you require unified visibility across multiple systems across the spectrum and your security team is in desperate need of contextual alerts and faster investigations.
There are other nuances that security teams of your company might need to dig deep to make the right call. However, they are beyond the scope of this blog. Consulting cybersecurity experts is the best way in such cases.
At the same time, organizations do not always need to choose between EDR and XDR as they could be a mutually exclusive option. Sometimes, XDR solutions are built on top of strong EDR foundations. EDR helps with endpoint devices and XDR looks after other components such as network, cloud and email.
Conclusion
Both EDR and XDR can turn out to be a viable and valuable technology depending on your security needs as well as budget. Understanding the difference between EDR and XDR allows IT leaders to align detection capabilities with their specific risk profiles and operational needs.
If you are looking to secure endpoints alone, opt for our EDR services. Else, if you want to manage threats across a distributed enterprise, our XDR services can help you enhance your threat detection and response capabilities. Contact us today!
Difference Between EDR and XDR FAQs
Can XDR replace an existing EDR solution entirely?
In most cases, XDR doesn’t replace EDR, it extends its capabilities. Many XDR platforms integrate tightly with EDR tools, making them complementary rather than mutually exclusive.
How does XDR help reduce alert fatigue compared to EDR?
XDR improves alert fidelity by correlating data from multiple sources, adding context to raw signals, XDR EDR, and filtering out noise. This reduces the number of redundant or false alerts security teams need to process.
Is XDR suitable for small businesses with limited IT resources?
XDR can benefit smaller teams by automating detection and response across environments. However, it may require an upfront investment and integration effort. Some vendors offer lightweight or managed XDR options tailored to small and mid-sized businesses.
How do EDR and XDR handle insider threats?
EDR detects suspicious activity on endpoints, such as privilege escalation or data exfiltration. XDR enhances this by identifying behavioural anomalies across email, identity, and network systems, making it more effective in spotting insider threats.
How MDR is different from EDR and XDR?
MDR is a managed security service that combines human expertise with tools like EDR and XDR to deliver 24/7 threat detection, investigation, and response. EDR focuses on endpoint-level threats, while XDR expands coverage across endpoints, networks, cloud, and more. Unlike EDR and XDR, MDR includes a dedicated team that actively hunts, analyses, and responds to threats. If you want an in-depth comparison of three modern detection and response solutions, read our blog EDR vs MDR vs XDR.