The night before a product launch is a terrible time to discover a critical flaw. That’s exactly the situation a SaaS founder once described to us. An automated scanner flagged several low-severity issues. But a scheduled manual test, run a week later, uncovered a chained business-logic exploit that could have cost millions.
The lesson wasn’t that one approach is right and the other wrong; it was that each method answers different questions. This blog unpacks DAST vs Pen Testing so security leaders and founders can make pragmatic, budget-savvy decisions that actually reduce risk.
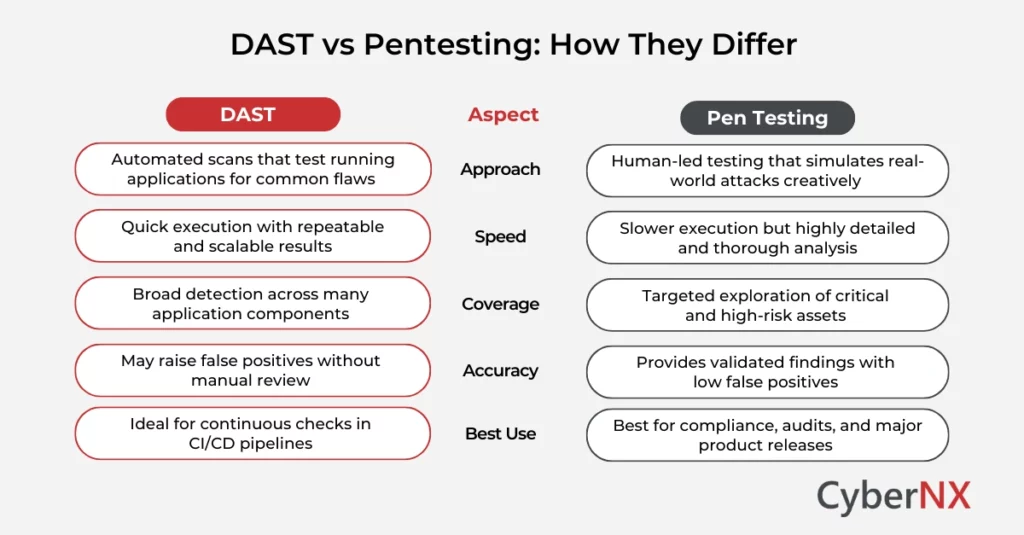
DAST vs Pen Testing: How They Differ
DAST automates runtime scans to detect common vulnerabilities, while pen testing relies on human expertise to uncover complex, high-impact attack paths. Together, they address different layers of application risk.
Let’s look at the two security exercises individually.
1. DAST (Dynamic Application Security Testing)
DAST is an automated scanning process that probes running applications. It can be APIs, web front ends, mobile backends. The goal is to look for common runtime vulnerabilities (XSS, SQL injection, insecure headers, etc.). It’s fast, repeatable and fits into CI/CD pipelines.
For comprehensive look into the topic and to find deeper insights, read our blog DAST Guide.
2. Penetration Testing (Pen Testing)
Pentest is a human-led, exploratory security test. Skilled pentesters use creativity, manual techniques and chain exploits to find real-world attack paths, Technically, it includes complicated business-logic, authentication bypasses, and chained vulnerabilities that automated tools miss.
This is a basic definition of Pentesting. Find expert perspective and full breakdown with our blog Penetration Testing Guide.
Why the Debate Exists?
People compare DAST vs Pen Testing as if it’s a single-choice binary. It isn’t. Each has different strengths, costs, and timelines. Think of DAST as constant surveillance and pen testing as a forensic inspection by an expert surgeon. Both deliver value – but they target different kinds of risk.
DAST vs Pen Testing: Strengths and Limitations
Each approach brings unique advantages and blind spots. Automation excels at speed and scale, whereas human-led testing delivers depth and real-world validation. The key is knowing when to apply each.
1. DAST Strengths and Limitations
DAST is fast, automated coverage that integrates seamlessly into CI/CD pipelines.
- Integrates into CI/CD for continuous feedback.
- Finds common, easy-to-exploit runtime issues quickly.
- Cost-effective at scale for frequent, broad coverage.
But DAST is limited in handling complex auth flows and prone to false positives.
- Struggles with complex auth flows, single-page apps, and deep business logic.
- Higher false-positive rates without human verification.
- Only as good as its attack surface visibility.
2. Pen testing Strengths and Limitations
Human intuition exposes chained exploits and business logic flaws.
- Human intuition discovers creative, high-impact attack chains.
- Validates real exploitability and produces pragmatic remediation steps.
- Excellent for compliance, pre-launch checks, and high-risk assets.
However, Pen testing can be expensive, periodic and reliant on tester skill for consistent results.
- Expensive and periodic – it’s a snapshot, not continuous.
- Coverage depends on scope and tester skill.
- Results can be inconsistent between vendors unless scope and methodology are standardized.
A Pragmatic Decision Matrix for Leaders
If you must choose where to spend your next security rupee, ask three questions:
1. What’s the business criticality?
Customer-facing payment flows and admin consoles demand human testing. Lower-risk internal dashboards may be well served by DAST.What’s the maturity of your engineering processes?
2. What’s the maturity of your engineering processes?
Teams with mature CI/CD and good observability benefit most from continuous DAST; early-stage teams may get more value from time-boxed manual reviews.
3. What compliance or contractual needs exist?
Some regulations and enterprise buyers require formal red-team or pen testing reports.
Mapping these: startups shipping fast → prioritize automated DAST in pipeline + targeted pen tests for critical modules. Regulated or high-value targets → mix scheduled pen tests with continuous DAST. Large, mature orgs → automated DAST everywhere + periodic deep pen tests + bug bounty for continual coverage.
A Realistic Sample Cadence (For Planning & Budgeting)
Security testing is most effective when it follows a predictable rhythm. A balanced cadence blends continuous DAST scans with periodic pen tests, aligning risk reduction with budget cycles.
- Continuous: DAST in CI for all services.
- Monthly: DAST full-scan and triage.
- Quarterly: Scoped pen test of highest-risk services and features.
- Annually: Pentest & business-critical red team for top-tier assets.
- Ongoing: Bug bounty program (optional) to catch real-world attacks.
Conclusion
When teams ask DAST vs Pen Testing, reframe the question: Which risks are we trying to reduce, how quickly, and at what cost? Automation buys speed and scale; human testing buys depth and contextual validation. Together they form a resilient, cost-effective program that speaks to compliance needs, board risk appetite, and engineering velocity.
Contact us today for expert-led Dynamic Application Security Testing (DAST) and penetration testing services. We are a CERT-In empanelled cybersecurity company with a certified team of professionals and experience of helping industries cut across sectors.
DAST vs Pen Testing FAQs
Can DAST replace the need for pen testing if I already run it continuously?
No. DAST is excellent for catching common runtime flaws quickly, but it lacks the creativity and contextual judgment of a human tester. Pen testing uncovers chained exploits, business logic flaws, and real-world attack scenarios that automation cannot reliably detect.
How often should a growing company budget for pen testing alongside DAST?
For most fast-scaling companies, quarterly or biannual pen tests—focused on critical features—strike a balance between cost and risk. Pairing this with ongoing DAST scans ensures continuous coverage without overextending budgets.
Does DAST work well for APIs and microservices?
Yes, but with caveats. DAST can scan APIs if properly configured, though it sometimes struggles with complex authentication or multi-step flows. In such cases, combining DAST with targeted pen testing provides stronger assurance.
What’s the business risk of relying only on pen testing without DAST?
Relying solely on periodic pen tests leaves long gaps between security checks, during which new vulnerabilities may slip into production unnoticed. Without DAST’s continuous scanning, organizations face increased exposure and delayed remediation.