Every regulated entity under SEBI must create and maintain a structured, actionable and board-approved cybersecurity policy. This requirement sits at the centre of the SEBI CSCRF. Because it sets the tone for governance, guides implementation and creates a shared language for risk.
Many organisations and compliance leaders worry about scope, approval steps and annual updates. To simplify it, you need a policy that can be used every day, not a long document that sits untouched. That is why a strong cybersecurity policy for SEBI CSCRF is essential. It aligns people, reduces confusion and supports audits, resilience and operational confidence.
This guide explains how to build a policy that meets SEBI CSCRF guidelines and standards. It covers graded applicability, governance, annual reviews and the structure you should follow. As a result, you will be able to design a policy that feels practical and not overwhelming.
Understanding the graded approach for policy development
CSCRF uses a graded model. It adjusts expectations based on the size and complexity of the entity.
| RE CATEGORY | POLICY REQUIREMENT |
| Self-certified REs | Basic policy covering essential areas |
| Small-size REs | Basic policy covering essential areas |
| Mid-size REs | Detailed cybersecurity policy |
This structure keeps the workload reasonable for smaller entities and ensures deeper coverage for organisations with higher exposure.
What your cybersecurity policy must cover
Even basic policies should address all essential areas. These areas shape day-to-day behaviour and long-term resilience.
Your policy should include:
- Governance roles and responsibilities
- User access rules
- Password and authentication standards
- Data handling and protection principles
- Network controls
- Asset management
- Change management
- VAPT and audit expectations
- Incident response actions
- Backup and recovery rules
- Vendor and outsourcing oversight
- Log management
- Monitoring procedures
We encourage clear language. Simple rules work better than long explanations. Teams follow policies when they feel easy to understand.
How to design a policy that fits your category
Every RE must follow the essential structure. Mid-size REs must add depth to reflect higher risk exposure.
1. For self-certified and small-size REs
A basic policy is enough. It should cover core areas but remain simple.
Focus on:
- Password rules
- Access rights
- Incident reporting
- Data protection
- Use of approved devices and software
- Remote access
- Handling of personal and client data
Leadership (MD, CEO, board member, partner or proprietor) is responsible for approving the policy.
2. For mid-size REs
A detailed policy is mandatory. It must include:
- Roles of the IT Committee
- Detailed access controls
- Advanced network and system controls
- Monitoring and logging standards
- Patch and vulnerability management
- Vendor risk controls
- Business continuity expectations
- Documentation and record-keeping rules
Mid-size REs must also maintain an IT Committee. The committee must include at least one external member. This supports transparency and stronger governance.
Governance and approval responsibilities
Policies gain authority only when backed by proper governance. CSCRF is clear about who must approve them.
- For mid-size REs: The IT Committee oversees policy creation and updates. Approval typically comes through this committee before it is presented to senior leadership.
- For small-size and self-certified REs: Since an IT Committee is not mandatory, the policy must be approved by:
- MD
- CEO
- Board member
- Partner
- Proprietor
Approval must be documented and traceable. We see many teams miss this part, which later creates issues during audits.
Annual review of the cybersecurity policy
Your cybersecurity policy cannot remain static. CSCRF requires a formal annual review for all RE categories.
During your review, assess:
- New threats
- New systems and tools
- Changes in business processes
- Findings from audits
- Lessons from incidents
- Feedback from teams
- Regulatory updates
Mid-size REs must not only review but also update their detailed policy every year. This keeps the policy aligned with real changes across the organisation.
Separate requirement: The cybersecurity risk management policy
Many organisations confuse the main policy with the risk management policy. CSCRF treats them separately.
The risk management policy must:
- Identify major risks
- Document risk scoring methods
- Assign ownership
- Set mitigation timelines
- Support board-level visibility
- Define reporting cycles
This policy must also be reviewed every year by all RE categories.
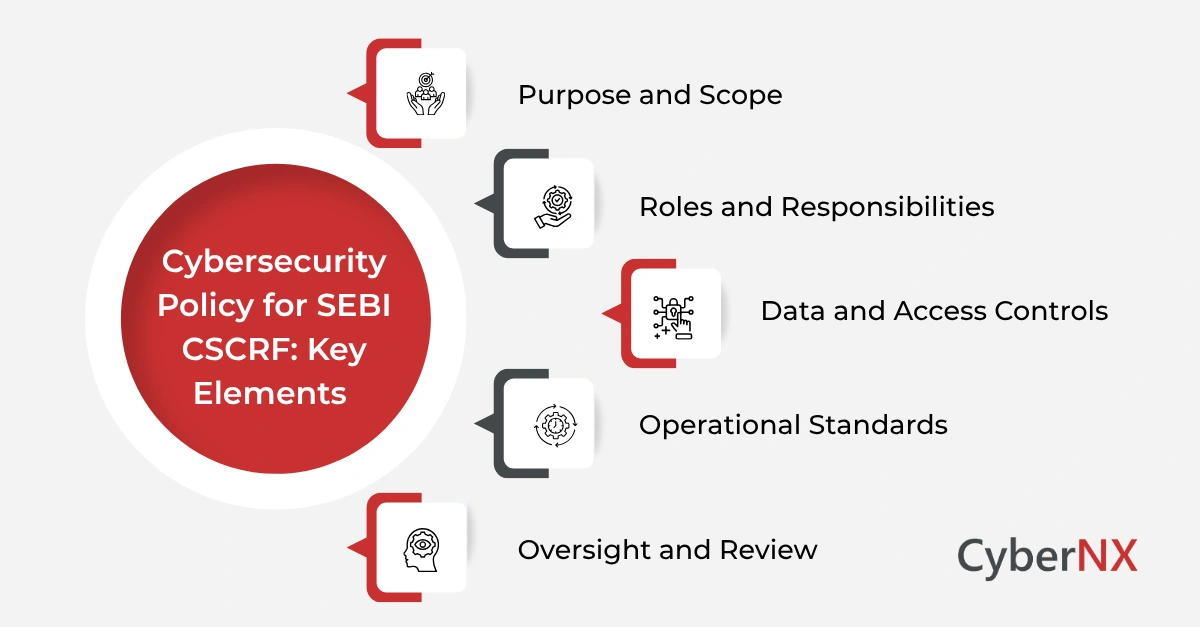
Structuring your cybersecurity policy for clarity
A good policy should guide behaviour and be easy to navigate. The following structure keeps it practical and usable for everyone:
- Purpose and Scope: Clearly state why the policy exists and outline the systems, people, and processes it applies to.
- Roles and Responsibilities: Define who is accountable for what – from leadership and IT to cybersecurity teams and end users – so expectations are unambiguous.
- Data and Access Controls: Set simple, clear rules for classifying, storing, and managing data, along with password, authentication, and access requirements.
- Operational Standards: Summarize monitoring, logging, and incident reporting procedures, specifying what is tracked, why it matters, and how issues should be escalated.
- Oversight and Review: Include technical control guidelines, vendor management steps (such as onboarding and performance reviews), and an annual review process to keep the policy relevant.
This streamlined approach helps teams understand and apply the policy in their daily work without feeling overwhelmed.
Ensuring the policy supports CSCRF requirements
Your cybersecurity policy for SEBI CSCRF must support the broader cybersecurity and cyber resilience goals. It must help your organisation:
- Anticipate risks
- Withstand disruptions
- Contain incidents
- Recover quickly
- Evolve through learning
Your policy is the foundation. It connects technical controls, governance and awareness. It informs how your teams behave during normal operations and unexpected events.
Conclusion
A strong cybersecurity policy for SEBI CSCRF provides direction and confidence. It shapes decisions, explains responsibilities and supports compliance across audits, VAPT cycles and resilience expectations.
It is important to design policies that feel clear and practical and build documents that teams actually use. Also, annual reviews are a must so nothing falls behind.
If you want help designing a SEBI CSCRF-aligned policy or reviewing your current one, our team of experts are ready to help. Together we can build a policy that strengthens your defences and supports long-term resilience.
Cybersecurity policy for SEBI CSCRF FAQs
What is the number one mistake REs make when drafting policies?
Many organisations create lengthy, jargon-heavy documents that employees struggle to follow. Keep policies concise, action-oriented, and written in plain language to ensure real-world adoption.
Do vendors need to follow our policy?
Yes. Any vendor or service provider that accesses your systems, data, or applications must adhere to your cybersecurity policy and related controls. It’s best to include this requirement in your vendor contracts.
What evidence do auditors check?
Auditors typically review your approved cybersecurity policy, version history, annual review logs, change records after incidents or audits, and evidence of management sign-off or board approval.
Can one policy cover all CSCRF requirements?
Not entirely. While a well-structured policy can address most requirements, SEBI CSCRF also mandates supporting documents – such as a Risk Management Policy, Incident Response Plan, and Vendor Management Framework – for full compliance.