SEBI’s Cybersecurity and Cyber Resilience Framework (CSCRF) set a new benchmark for the securities market. It raises expectations, clarifies responsibilities and pushes every Regulated Entity to uplift its cybersecurity posture with practical, measurable steps.
Many teams might feel the pressure, but you don’t have to. What you need to do is to balance daily operations with audits, VAPT, monitoring, vendor checks and rapid reporting timelines.
In our experience of working with firms across categories, we’ve seen how the right cybersecurity controls boost confidence. They remove ambiguities, guide priorities and help teams stay ready.
This blog breaks down the ten most important cybersecurity controls you must implement under CSCRF. In addition, we explain graded applicability, resilience goals, drill requirements and essential clarifications. Our aim is simple: to help you meet the framework with clarity and move your security posture forward.
Graded applicability under CSCRF
SEBI follows a graded structure. This ensures the right level of rigour for different entities. The category assigned to your organisation influences which cybersecurity controls apply, and how deeply you must implement them.
The five categories are:
- Market Infrastructure Institutions
- Qualified REs
- Mid-size REs
- Small-size REs
- Self-certification REs
If an RE fits into more than one category, the stricter category will apply. This removes grey areas and strengthens accountability. Before you choose tools or draft policies, confirm your category. It shapes every compliance milestone.
Core cybersecurity controls required for all REs
These controls apply across categories. The depth of implementation increases as the organisation size grows. Below is a simplified view.
| CONTROL AREA | SELF-CERTIFIED | SMALL-SIZE | MID-SIZE | KEY DETAILS |
| Cybersecurity Policy | Basic | Basic | Detailed and reviewed annually | Mandatory yearly review |
| Asset Management | Critical asset list + SBOM | Same | Same | SBOM for all core and critical software |
| VAPT | Annually | Annually | Annually | Must begin in Q1; fixes within 3 months |
| Cyber Audits | Annually | Annually | Annually | CERT-In empanelled auditor |
| SOC | Functional checks | Continuous monitoring | Continuous monitoring | Smaller REs may use Market-SOC |
| Incident Reporting | 24 hours on SEBI portal | Same | Same | Email report within 6 hours; forensic audit for major incidents |
| Operational Controls | Basic requirements | Same | Same | Privileged access review every 6 months |
| Training | Annually | Annually | Semi-annually | Increased frequency for Mid-size |
These are your foundation. Once these are stable, other controls can be built smoothly.
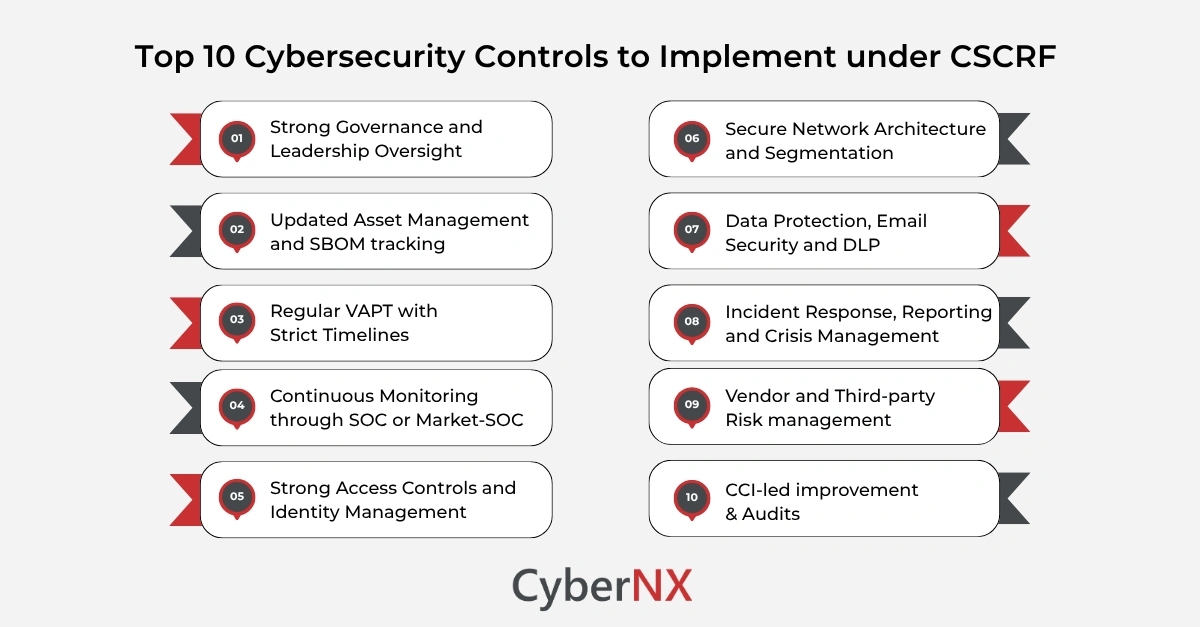
Top 10 cybersecurity controls you must implement under CSCRF
Below are the ten cybersecurity controls every RE must prioritise. We’ve expanded each to reflect CSCRF expectations and practical business impact. These are important to achieve SEBI CSCRF compliance.
1. Strong governance and leadership oversight
Clear leadership drives clarity in security. CSCRF requires well-defined responsibilities, escalation paths and committees.
You must:
- Maintain a documented cybersecurity policy.
- Review it every year.
- Appoint a qualified CISO for mid-size and above.
- Create an IT Committee with at least one external member (mandatory for mid-size).
- Track cyber risks and decisions formally.
Strong governance helps leaders anticipate threats and allocate budgets wisely. It keeps teams aligned and reduces blind spots.
2. Updated asset management and SBOM tracking
You cannot secure what you cannot see. CSCRF emphasises complete visibility across hardware, software and data assets.
Your team must:
- Maintain an updated critical asset list.
- Track a detailed Software Bill of Materials for all applications.
- Document third-party dependencies.
- Map which systems are critical for trading, settlement or client management.
We’ve seen firms uncover unknown services just by creating the SBOM. That visibility alone often reduces risk.
3. Regular VAPT with strict timelines
VAPT under CSCRF is not optional. It is structured.
Key points:
- Conduct VAPT annually across categories.
- Begin the assessment in the first quarter.
- Fix findings within three months.
- Qualified Stock Brokers must perform VAPT and cyber audits every six months.
We work closely with teams on VAPT closure. Short, clear remediation windows help avoid backlog and push steady improvement.
4. Continuous monitoring through SOC or Market-SOC
Monitoring is a major requirement. Entities must detect anomalies early and escalate fast.
Depending on your category, you must either:
- Run a full SOC, or
- Use the Market-SOC from exchanges.
Either way, the expectations are clear. You must collect logs, monitor them and retain integrity. You must also detect suspicious access patterns, network events and policy violations. This control reduces response time and improves containment.
5. Strong access controls and identity management
Poor access hygiene remains one of the biggest causes of breaches. CSCRF mandates simple, effective measures.
You must:
- Implement multi-factor authentication
- Enforce least privilege
- Review privileges every six months
- Isolate admin access
- Use PAM or PIM tools for mid-size REs and above
- Strengthen password policies and Active Directory controls
These steps reduce misuse and prevent lateral movement.
6. Secure network architecture and segmentation
Mid-size REs and larger entities must implement stronger technical controls.
These include:
- Segmented networks
- Zero-trust-aligned access patterns
- Capacity planning
- Continuous monitoring of network performance
Network segmentation plays a huge part in helping organisations withstand incidents without full shutdown.
7. Data protection, email security and DLP
Data exposure risks are high across securities businesses. CSCRF mandates structured controls.
You must:
- Classify data
- Encrypt data at rest and in transit
- Implement DLP or define strict data usage controls
- Deploy SPF, DKIM, DMARC and DNS filtering for email
- Mask sensitive fields
- Test patch stability before deployment
Every organisation we work with finds quick wins in this area. Even smaller changes reduce risk significantly.
8. Incident response, reporting and crisis management
Response is a major focus in CSCRF. Reporting timelines are strict.
Key expectations:
- Report incidents to SEBI within 24 hours.
- Send an email update within 6 hours.
- Conduct forensic audits for critical incidents.
- Maintain an incident response plan.
- Run annual live cyber crisis drills.
Resilience metrics are defined too.
- RTO must be 2 hours
- RPO must be 15 minutes
These targets set clear expectations for business continuity.
9. Vendor and third-party risk management
Third-party exposure grows each year. CSCRF holds REs accountable even when services are outsourced.
You must:
- Conduct due diligence on vendors.
- Ensure ISO 27001 certification for outsourced services.
- Assess and document vendor risks.
- Validate controls at hosting sites, cloud setups and SOC providers.
- Maintain contractual safeguards.
Your accountability does not transfer. It stays with you, even on cloud.
10. Continuous improvement through CCI and periodic audits
Cybersecurity is not static. CSCRF builds improvement directly into the framework.
For mid-size and above:
- You must measure maturity using the Cyber Capability Index.
- QREs must self-assess yearly.
- MIIs need third-party assessment every six months.
- Automated dashboards help submit compliance.
- Audits must be done by CERT-In empanelled bodies.
This approach supports evolution. It helps teams learn from incidents and change controls before issues grow.
Cyber resilience goals built into CSCRF
SEBI goes beyond cybersecurity to build resilience. The goals are:
| GOAL | MEANING |
| Anticipate | Prepare for threats using intelligence, policies and governance |
| Withstand | Keep essential operations running during an attack |
| Contain | Limit spread and isolate systems quickly |
| Recover | Restore services within the defined RTO and RPO |
| Evolve | Improve based on learnings, trends and new threats |
This structure encourages practical readiness, not theoretical plans.
Conclusion
SEBI’s CSCRF is detailed and demanding. But it also gives you a clear blueprint. When these cybersecurity controls work together, they reduce confusion and strengthen your entire environment. They improve visibility, enhance response and they reduce operational risk.
We help REs across all categories implement these controls with clarity and confidence. From audits to SOC to VAPT to cloud and vendor checks, we work alongside your team at every stage.
If you want a structured SEBI CSCRF gap assessment or implementation support, reach out to us. We’re ready to help you strengthen your defences and move ahead with confidence.
Cybersecurity controls FAQs
What is the difference between compliance and resilience under CSCRF?
Compliance means meeting the stated requirements of CSCRF (reports, controls, timelines). Resilience means being able to anticipate, withstand, contain, recover and evolve when an actual cyber-incident happens. CSCRF embeds both.
Do all regulated entities (REs) under SEBI have to implement every control listed in CSCRF?
The CSCRF classifies entities into categories (MIIs, Qualified REs, Mid-size, Small-size, Self-certification) based on risk, size and role. The obligations scale accordingly.
How often must VAPT be conducted under CSCRF?
While the exact frequency depends on the entity’s category and changes, the framework mandates VAPT after major releases/changes and periodically. Entities must patch critical vulnerabilities promptly (for example, within 24 hours for critical ones as per guidance).
Does CSCRF require data to be stored purely in India?
For certain regulatory or sensitive data sets, yes localisation or acceptable controls apply. Encryption, masking and controls over data flows are required. Organisations must check the specific stipulations in the CSCRF for their category.