Cyber risks touch every part of the financial sector. Teams handle sensitive data and respond to constant operational demands. SEBI’s Cybersecurity and Cyber Resilience Framework (CSCRF) set clear expectations to help organisations stay prepared.
One of the core requirements is structured cyber awareness training. It builds sharper instincts, reduces mistakes and strengthens the first line of defence.
In our experience of working with different regulated entities, many worry about training consistency and compliance timelines. They want a simple approach that works. However, the complexity in understanding regulatory requirements can make the whole exercise hard.
This guide aims to simplify SEBI CSCRF requirements in the context of how you can design, deliver and review cyber awareness training. It breaks down the graded model, due diligence requirements, annual reviews and CCI connections. Each step helps you build a programme that is practical, measurable and easy to maintain.
Understanding the graded approach for training
CSCRF does not apply the same training expectations to every organisation. It uses a graded structure that reflects the size and operational exposure of each RE.
| RE CATEGORY | TRAINING REQUIREMENT |
| Self-certified REs | Annual cybersecurity training |
| Small-size REs | Annual basic cybersecurity training |
| Mid-size REs | Cybersecurity training twice a year |
Before you plan sessions, confirm your category. It sets the minimum baseline for frequency and depth.
Core requirements for cyber awareness training
Regardless of the category, the aim remains consistent. Teams must learn how to recognise threats, follow good practices and respond quickly.
Topics that often work well include:
- Secure password habits.
- Handling client data.
- Recognising phishing and social engineering.
- Correct steps for reporting incidents.
- Safe remote access.
- Using approved software and devices.
- Email security.
- Understanding common attack patterns.
Short, simple sessions improve participation and retention. This makes it easier for teams working under time pressure, such as operations and support desks.
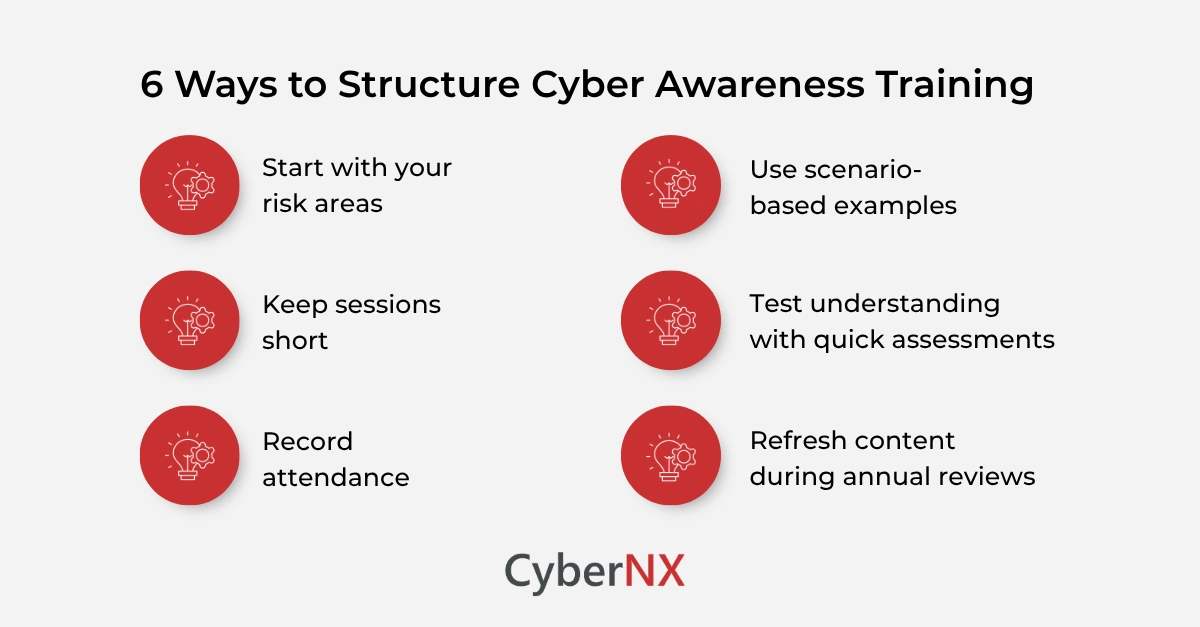
How to structure effective cyber awareness training
A clear training structure helps teams absorb information faster.
1. Start with your risk areas
Every organisation faces different challenges. Run a gap assessment, look at your internal operations and highlight the areas where human error could create the most impact.
2. Use scenario-based examples
Real situations make learning stick. Examples of suspicious emails, unsafe downloads or incorrect system use help people react calmly in real situations.
3. Keep sessions short
We see strong results with modules that run for 20 to 30 minutes. Teams stay focused and do not feel overloaded.
4. Test understanding with quick assessments
Simple quizzes give you measurable proof of training effectiveness. They also support audit readiness.
5. Record attendance
SEBI expects evidence of participation. Keep copies of the material and attendance logs.
6. Refresh content during annual reviews
Threats change. Therefore, training must reflect those changes. Update your content with new examples and insights from real incidents.
Personnel due diligence and screening
Training is only one part of CSCRF. Mid-size REs and above must also run formal due diligence and screening processes.
This includes:
- Background checks during hiring
- Screening individuals who access information systems
- Documenting screening outcomes for audit and compliance
These steps are not required for self-certified or small-size REs. But many organisations voluntarily adopt light screening to reduce insider risks.
Annual review of the training programme
All REs must review their cyber awareness training programme every year. This review must assess:
- Whether the content reflects current threats.
- Whether employees found it easy to understand.
- Whether training frequency is sufficient.
- Whether new risks or incidents require additional modules.
- Whether records and attendance tracking remain complete.
Annual reviews keep the programme relevant. They also help you adapt to changes in technology, teams and processes.
How training links to the Cyber Capability Index
Some organisations, such as Qualified REs and MIIs, must calculate their Cyber Capability Index (CCI). Personnel controls influence the score.
Parameter 14 of the CCI checks: How many individuals with system access have been screened, measured as a percentage.
Training, screening and documentation shape this outcome. For REs falling under CCI, we encourage early alignment of HR, IT and compliance teams. It avoids manual corrections later and ensures accuracy during assessments.
Delivering training across RE categories
Build awareness that scales with responsibility. Tailor frequency, depth and delivery style to each RE category. This helps every team learn what truly matters to their role and compliance needs.
- For self-certified REs: Deliver one training session each year. Keep it focused. Practical, short modules work best. Keep clear records.
- For small-size REs: Provide basic training annually. Emphasise incident reporting, password rules and awareness of phishing. Many small teams prefer short in-person sessions or simple videos.
- For mid-size REs: You must conduct training twice a year. You also have due diligence and screening obligations. Consider:
- Role-based content
- Interactive modules
- Regular awareness reminders
- Defined learning paths in a simple LMS
This approach helps you maintain consistency and supports audit checks.
Tips to improve engagement
We’ve seen these small changes create big impact.
- Use real phishing examples collected by your SOC or service provider.
- Share monthly awareness notes.
- Highlight common mistakes from internal audits.
- Keep reporting instructions simple and visible.
- Encourage managers to reinforce good habits.
- Recognise attentive behaviour with small appreciation tokens.
Training becomes more meaningful when people see it as part of daily work, not just a requirement.
Conclusion
Cyber awareness training strengthens your team and supports compliance under CSCRF. It shapes good habits, reduces everyday risks and it helps employees respond faster when something feels wrong.
We work with many regulated entities across categories. We see the difference that clear, well-designed training makes. It brings confidence, creates awareness and helps organisations stay resilient.
If you want support building or delivering a SEBI CSCRF-aligned cyber awareness programme, our team is ready to help. We’ll work with you to design sessions, create material and support compliance reviews.
Cyber awareness training FAQs
Do CSCRF audits check training quality?
Yes. Auditors review attendance logs, training content and annual review records.
Do vendors need awareness training too?
If they access your systems or data, you must ensure they understand and follow security expectations.
Should training differ by role?
For mid-size REs and above, role-based modules help significantly. Critical roles need deeper coverage.
What format works best for training?
Short, structured sessions – either online or in-person – work well. People absorb information faster in smaller segments.