You protect what is precious. That’s a simple truth. Not annually or quarterly, but always. So, when it comes to your business, continuous penetration testing does exactly that – it makes security always-on.
Modern IT environments face real-time threats as cyber attacks grow in sophistication and frequency. AI enabled ransomware, malware and phishing services being prime examples.
Also, the proliferation of cloud technologies, API-driven ecosystems and agile software development practices necessitates a continuous and dynamic security approach.
What is Continuous Penetration Testing?
Continuous Penetration Testing can be understood as an ongoing process where your IT infrastructure vulnerabilities are assessed continuously and in real-time. Which effectively means: your business is in the defence mode against modern threats, always.
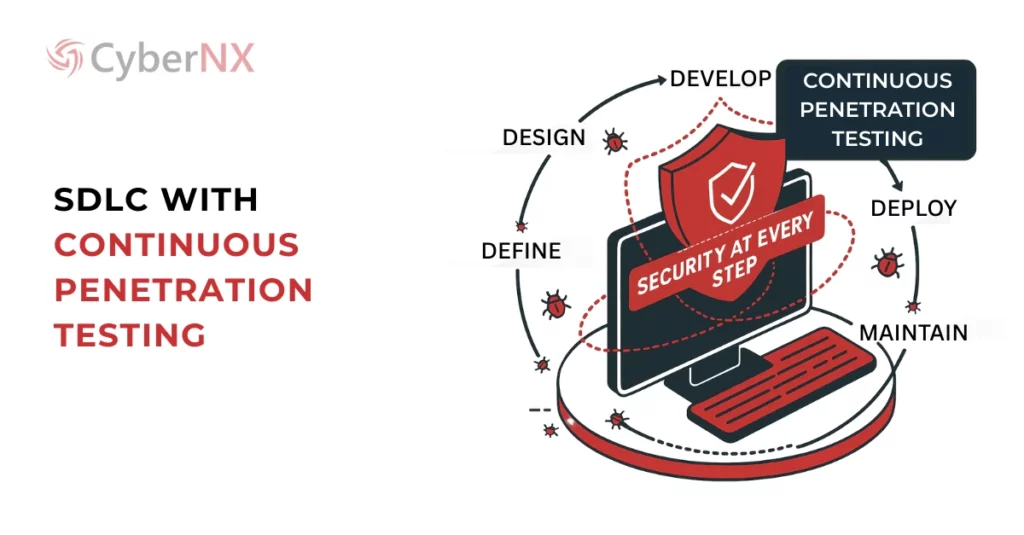
Let’s understand this with an example of the software development life cycle (SDLC).
SDLC process includes define, design, develop, deploy and maintenance. Each step should have security testing integrated. Else, security gaps can happen, causing irreversible damage.
Typically, a traditional penetration test would take a minimum of 2 weeks to set up and more to complete the process. Moreover, carrying out penetration testing once a year or quarterly could leave your applications vulnerable. And you may miss security issues.
That’s the reason why continuous penetration testing can turn out to be a proactive measure in the SDLC process. Both should run together, mitigating potential breaches, securing code and improving security controls constantly.
In addition, pentesters will provide a continuous look at the possible weak points and effective defence strategies.
Wondering if it is better than periodic testing? See our Manual vs Automated Penetration Testing analysis.
Traditional Penetration Testing vs. Continuous Penetration Testing
Traditional penetration testing involves a predefined assessment carried out at scheduled intervals. This approach is quite effective in finding weaknesses at a specific point in time.
But what about the time between the tests?
Evolved and unseen vulnerabilities can pop up anytime and remain unaddressed for months.
Continuous pen test closes these gaps. Human-led and automation-enabled monitoring, detection and exploitation of vulnerabilities as they appear proves to be a game changer for protecting businesses.
Inherently responsive and aligned with the agile and DevSecOps methodologies in modern development today, this continuous security approach is elevated to a necessary discipline rather than just a compliance task.
Here’s a quick look at the difference between traditional pen test and continuous pen test.
| Feature | Traditional Pentesting | Continuous Pentesting |
| Frequency | Periodic (annually/quarterly) | Ongoing (daily/weekly/trigger-based) |
| Scope | Predefined and static | Adaptive and evolving |
| Discovery Window | Vulnerabilities found may remain unaddressed until next test | Rapid identification and mitigation of issues |
| Coverage | Snapshot in time | Continuous assessment of changing environments |
| Cost Model | Project-based | Subscription or ongoing service |
Why Do You Need Continuous Penetration Testing?
Real-time threat detection
Threat actors, in the current landscape, may pose risk any time. Continuous testing helps in identifying vulnerabilities as they emerge, empowering organisations to address them before being exploited.
Moreover, real time threat detection would mean quick remedy and business continuity. That’s the most important reason why you should do continuous pentesting.
Secure Agile Environment & CI/CD
If your business has adopted Continuous Integration/Continuous Deployment pipelines and other agile methodologies, continuous testing approach is a must.
This is because code is often pushed to production in such environments.
Continuous pentesting keeps pace with such processes and ensures security remains high during the software development cycle.
Cloud and API Changes
Cloud-native and API-centric architectures are increasingly complex, and therefore susceptible to unauthorised access, insecure endpoints and misconfigurations. Continuous pentesting is equipped to handle these dynamics by offering continuous monitoring and visibility into changes happening in the infrastructure and applications.
Regulatory Compliance & Audit Readiness
Your business can keep up with compliance requirements with continuous penetration testing services for compliance. Major industries like healthcare, finance and technology, governed by security standards, can maintain due diligence during audits with continuous pentesting service.
Reduces Dwell Time for Vulnerabilities
The longer a vulnerability remains undetected, the greater the risk it poses for your organisation. Identifying and addressing security flaws can reduce the Mean Time to Detection (MTTR). This in turn, reduces the window of opportunity for hackers.
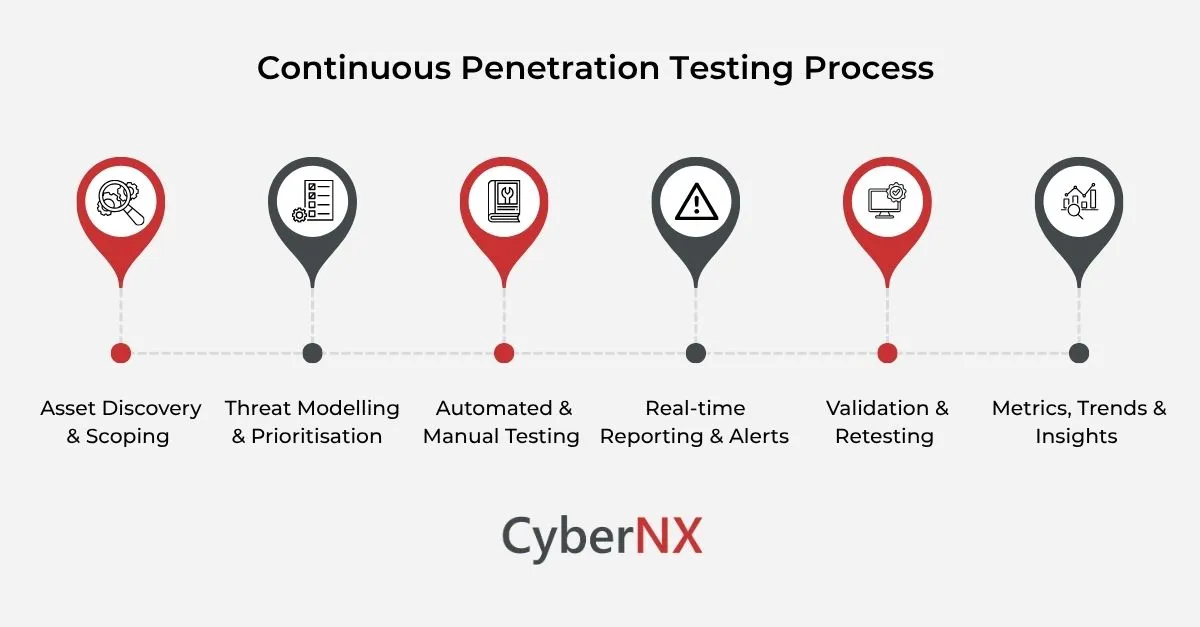
Process of Continuous Penetration Testing
Asset Discovery & Scoping
The continuous penetration test process begins by mapping the attack surface to ensure identification of all known and unknown assets that can be targeted by attackers. In modern environments, assets like APIs, containers or virtual machines are deployed fast. Thus, the process automatically starts asset discovering and scoping.
Threat Modelling & Prioritisation
Next up, threat modelling and risk prioritisation are done. Based on the business context, exposure levels and data sensitivity, continuous pentesting experts assess and determine assets with highest risks.
Automated & Manual Testing
Automation brings speed and scale, whereas manual testing adds depth. The hybrid approach, central to continuous testing, helps in the quick identification of known vulnerabilities and misconfigurations. Plus, it uncovers logic flaws through real-word attack chains.
Real-time Reporting & Alerts
Identified vulnerabilities are reported in real-time through easy-to-use dashboards, alerts or integration with issue-tracking platforms. The immediate and continuous feedback loop cuts typical delays and help teams take fast actions.
Validation & Retesting
Validation and retesting follow. It is verified whether fixes have been implemented effectively, and no residual issues remain. This is crucial for maintaining the security posture over time.
Metrics, Trends & Insights
Insights and trends are reported continuously. Organisations can view metrics like vulnerability recurrence, response times and exploitability trends, helping security leadership to learn where weaknesses persist, how to funnel resources and build better security strategy
When Should Your Business Consider Continuous Pentesting?
Based on the security posture and risk profile, your business can decide when to choose continuous pentesting approach.
Our experts provide more insight into it below:
- You deploy code frequently, then you are ready for continuous pentesting, as every new code pushed could produce new vulnerabilities. Plus, this security approach keeps pace with innovation.
- If you have a complex or rapidly growing IT environment, the attack surface also expands with APIs, cloud platforms and third-party integrations. Here, continuous pentesting will provide visibility into risk exposure.
- If your organisation is pursuing security certifications or undergoing compliance audits, continuous pentesting can be handy. Continuous documentation and evidence required to meet regulatory frameworks becomes easy with this process.
- Any recent data breach or potential incident should be a wake-up call to strengthen security. The continuous pen testing enables a proactive approach.
Explore smart testing with our blog on AI in Penetration Testing.
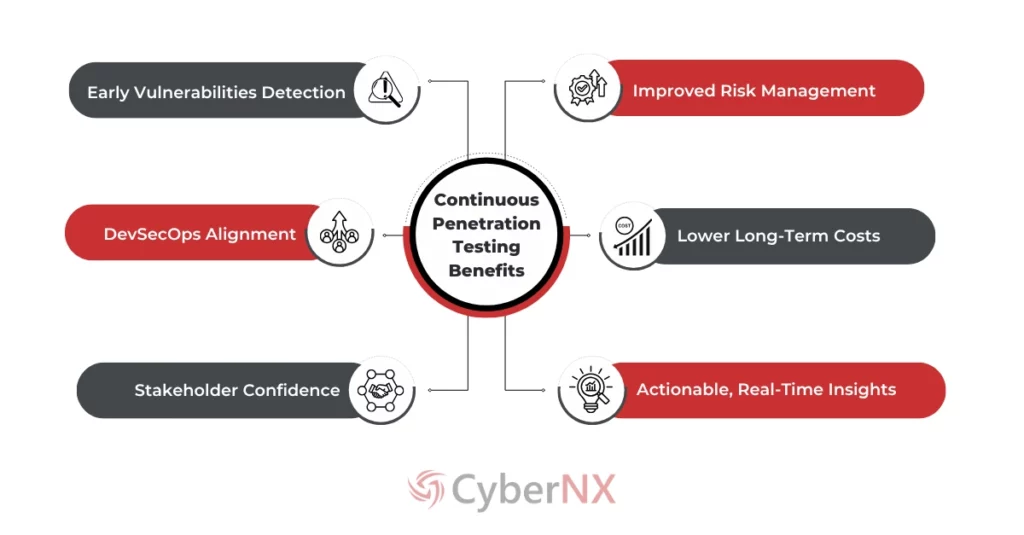
Continuous Penetration Testing: Benefits for Business
With continuous pen testing approach, organisations can gain the upper hand in maintaining a stronger and resilient security posture against modern threats.
Irrespective of your goals like building new applications, scaling infrastructure or compliance requirements, this approach delivers proactive defence your organization needs.
CyberNX is a leading, trusted and reliable name in the continuous penetration testing field. At a time when attackers move quickly, our advanced and innovative continuous security approach make sure you respond with agility.
Contact us today for more information about penetration testing service.
FAQs
How do I choose the right Continuous Pentesting provider for my business?
Look for a continuous penetration testing provider that offers hybrid testing (automated + manual), real-time reporting, CI/CD integration, and scalability. Ensure they support your tech stack (e.g., cloud platforms, APIs) and align with your compliance requirements.
What are some best practices to ensure CPT is effective?
Integrate CPT into your DevSecOps pipeline, focus on high-risk assets first, set up real-time remediation workflows, and periodically review findings with both technical and executive stakeholders.
Can Continuous Pentesting help reduce vulnerability reoccurrence?
Yes. A continuous penetration test includes automated retesting and trend analysis, allowing security teams to track whether vulnerabilities reappear and address root causes rather than just symptoms.
Is Continuous Pentesting suitable for internal infrastructure as well as public-facing assets?
Absolutely. While most start with external assets, mature programs include internal applications, employee endpoints and lateral movement scenarios to cover the full attack surface.