Cybersecurity in India has entered a decisive new phase. With the 2025 CERT-In Comprehensive Cybersecurity Audit Guidelines, enterprises cannot treat audits as once-a-year routine. The new framework makes annual cybersecurity audits mandatory for both public and private organizations and expands the expectations well beyond compliance checklists.
These guidelines reflect today’s reality that cyber risk today is a business risk, and not just a technology concern. For business and security leaders, cybersecurity audits are now core elements of cyber resilience and organizations are prepared for real-world threats.
10 Major Takeaways from the New CERT-In Guidelines
As CERT-In empanelled auditors, our experts dissect the latest CERT-In guidelines and present 10 takeaways shaping India’s cybersecurity landscape in 2025 and beyond.
1. Mandatory Annual Audits
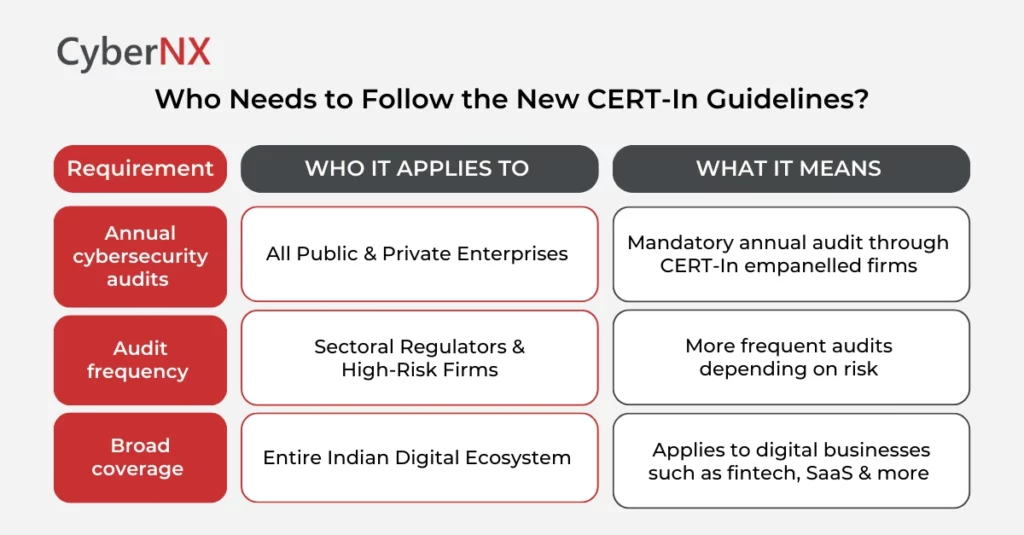
Every organization, public or private enterprise, must conduct yearly cybersecurity audits through CERT-In empanelled firms. Depending on the risk profile, regulators may also require more frequent checks. This creates a baseline of assurance across industries and forces enterprises to keep pace with evolving and modern threats.
Find below a quick snapshot of CERT-In guidelines for organizations in India.
2. From Compliance to Threat Readiness
The CERT-In audit guidelines signal a massive shift from check-box compliance to active threat preparedness. Instead of simply establishing security policies, organizations now have to demonstrate that security controls are working in practice. Continuous monitoring, VAPT and red-team style testing are encouraged to show threat readiness.
3. Stronger Audit Framework
Earlier, CERT-In guidelines only emphasized on preventive security measures for organizations such as implementing firewalls, antivirus and access rules. The new CERT-In audit guidelines, however, insist on active and ongoing security. Thus, organizations should invest in real-time detection, response and recovery. That means utilizing SIEM, SOAR, EDR/XDR, MDR and incident response strategies.
4. Attention on Key Attack Vectors
CERT-In guidelines have specifically put the spotlight on attack paths that have led to data breaches worldwide, which wasn’t the case earlier. This includes:
- VPN and remote access configurations which are common ransomware entry points for cyber attackers
- Supply chain dependencies, especially third-party risk assessments
- Access controls and identity management, which emphasizes enforcement of MFA and least privilege
5. Evidence Over Policies
Organization now cannot impress cybersecurity auditors with just neatly written policies. Hard evidence is mandatory as per the latest CERT-In guidelines. The examples include:
- Log samples showing that security monitoring across the IT system is active
- Secure configuration files and code repositories
- Cloud environment settings
- Proof of patching cycles and vulnerability fixes
6. Full ICT Coverage
Audits will need to cover the entire digital estate of an organization, mandates new CERT-In guidelines. This includes:
- Operational Technology (OT) in manufacturing and utilities
- Cloud platforms and SaaS applications
- APIs and microservices
- Custom applications and mobile platforms
In addition, both manual penetration testing and automated vulnerability scans are mandated to ensure depth and breadth of coverage.
7. Global Frameworks as the Base
Auditors are expected to map controls to international standards such as ISO 27001, NIST CSF, CIS Benchmarks and OWASP. Vulnerabilities must be assessed in terms of real-world exploitability and business impact. Adhering to CERT-In guidelines also makes Indian enterprises globally credible, easing compliance with cross-border clients and partners.
8. Mandatory Technical Checks
What was once considered optional best practice is now compulsory. Expect auditors to demand:
- Log retention for forensic investigations
- Code reviews for secure development practices
- Configuration checks for firewalls, endpoints, and cloud resources
- Incident response playbooks tested through simulations
This creates a more uniform and rigorous baseline across industries.
9. Board-Level Responsibility
Cybersecurity is now firmly a leadership issue, informs the latest CERT-In guidelines. Boards and senior management must:
- Define the scope of audits
- Approve remediation actions
- Ensure end-to-end coverage of risks
The guidelines embed accountability at the top, making CEOs and directors answerable if cyber risks are ignored. This is a clear move toward shared responsibility between IT teams and business leadership.
10. Skilled Auditors with Modern Expertise
Finally, the guidelines raise the bar for auditors themselves. CERT-In empanelled firms must demonstrate skills in modern architectures, including:
- Multi-cloud and hybrid setups
- AI/ML-based systems
- Highly connected IoT/OT environments
Auditors must bring technical depth and practical threat knowledge.
For actionable steps to implement these new guidelines, head to our blog How to Implement CERT-In Guidelines that covers pretty much everything you need to know.
Why This Matters for Indian Enterprises
The implications are profound:
- Cybersecurity is now a boardroom priority: CEOs and directors can no longer delegate responsibility entirely to IT.
- Audits are strategic, not symbolic: They test resilience against real-world adversaries, not just compliance frameworks.
- Proof is essential: Organizations must maintain continuous logs, technical evidence, and documented remediation.
- Partnership with auditors matters: Choosing a skilled CERT-In empanelled partner can make the difference between a painful audit and a resilience-building one.
For CISOs and CTOs, this means tighter collaboration with leadership, auditors, and regulators. For CEOs and founders, it means recognizing that cyber risk is business risk – with reputational, financial, and even legal consequences.
Conclusion
The 2025 CERT-In guidelines position India’s enterprises on a trajectory toward global best practices. By enforcing rigor, mandating evidence, and embedding leadership accountability, they aim to close the gap between policy and practice.
Enterprises that embrace these guidelines proactively will not only achieve compliance but also strengthen trust with customers, partners, and regulators. Those that treat audits as a burden risk falling behind – and facing both regulatory penalties and real-world breaches.
From initial assessment to final CERT-In submission, we handle every aspect of your cybersecurity audit. Our comprehensive approach ensures not just compliance, but improved security posture for your organization. Contact us today.
Latest CERT-In Guidelines FAQs
How often do enterprises need to undergo a CERT-In mandated cybersecurity audit?
Enterprises are now required to conduct annual cybersecurity audits. For critical sectors or organizations with higher risk exposure, CERT-In may call for more frequent reviews depending on threat intelligence or incident history.
Do the new CERT-In audit guidelines also apply to startups and mid-sized businesses?
Yes. The guidelines are not limited to large corporations. Any enterprise handling digital infrastructure, sensitive data, or customer information—regardless of size—must comply. This ensures that even smaller organizations don’t become weak links in the national cyber defence chain.
What role does the board or senior leadership play in CERT-In audits?
CERT-In guidelines put accountability at the leadership level. Boards, CEOs, and CXOs must approve audit outcomes, allocate budgets, and ensure remediation measures are implemented. This shifts responsibility from just the IT/security team to the entire leadership.
How do CERT-In audits differ from global cybersecurity frameworks like ISO 27001 or NIST?
While global frameworks are voluntary best practices, CERT-In audits are legally enforceable for Indian enterprises. However, the guidelines encourage alignment with international standards, making compliance both nationally mandatory and globally relevant.