Most organisations today are familiar with SBOMs. Some are already producing them while others are being asked for them by customers, auditors, or regulators.
But a new question is starting to surface in security discussions. Is an SBOM enough?
As encryption becomes deeply embedded across applications and infrastructure, software inventories alone no longer provide full risk visibility. Security teams are being asked to explain not just what software they run, but how cryptography is used inside it.
This is where the conversation shifts from SBOM to CBOM.
In this blog, we clearly explain CBOM vs SBOM, how they differ, and why they work best together rather than in isolation.
What is an SBOM?
SBOM stands for Software Bill of Materials.
It is a structured inventory of all software components that make up an application or system. This includes first-party code, open-source libraries, frameworks, and third-party dependencies.
An SBOM typically answers questions such as:
- What components are included in this software?
- Which versions are deployed?
- Who supplied them?
- Where are known vulnerabilities present?
From a security perspective, SBOMs help teams respond faster to vulnerabilities, improve supply chain transparency, and support compliance requirements.
However, SBOMs describe components. They do not describe behaviour inside those components. That limitation becomes clear when cryptography is involved.
What is a CBOM?
CBOM stands for Cryptographic Bill of Materials.
A CBOM focuses specifically on cryptographic assets and their dependencies. Instead of listing software libraries, it lists the cryptography those libraries and applications implement or use.
A CBOM can capture:
- Cryptographic algorithms and variants
- Protocols such as TLS or IPsec
- Certificates and their properties
- Keys and related cryptographic material
- Dependencies between applications, libraries, and crypto assets
Importantly, CBOM distinguishes between cryptography that is merely present and cryptography that is actually used at runtime. This makes CBOM far more actionable for risk and compliance decisions.
Why SBOM alone is not enough
SBOMs tell you what software you have. They do not tell you how secure that software is cryptographically.
For example, an SBOM may show that a system uses a specific cryptographic library. But it cannot answer:
- Which algorithms are enabled?
- Are weak primitives still in use?
- What key sizes or modes are configured?
- Which certificates are deployed and when they expire?
These details matter. Especially for compliance, incident response, and long-term planning such as migration to quantum safe cryptography.
CBOM fills this gap by making cryptography visible and measurable.
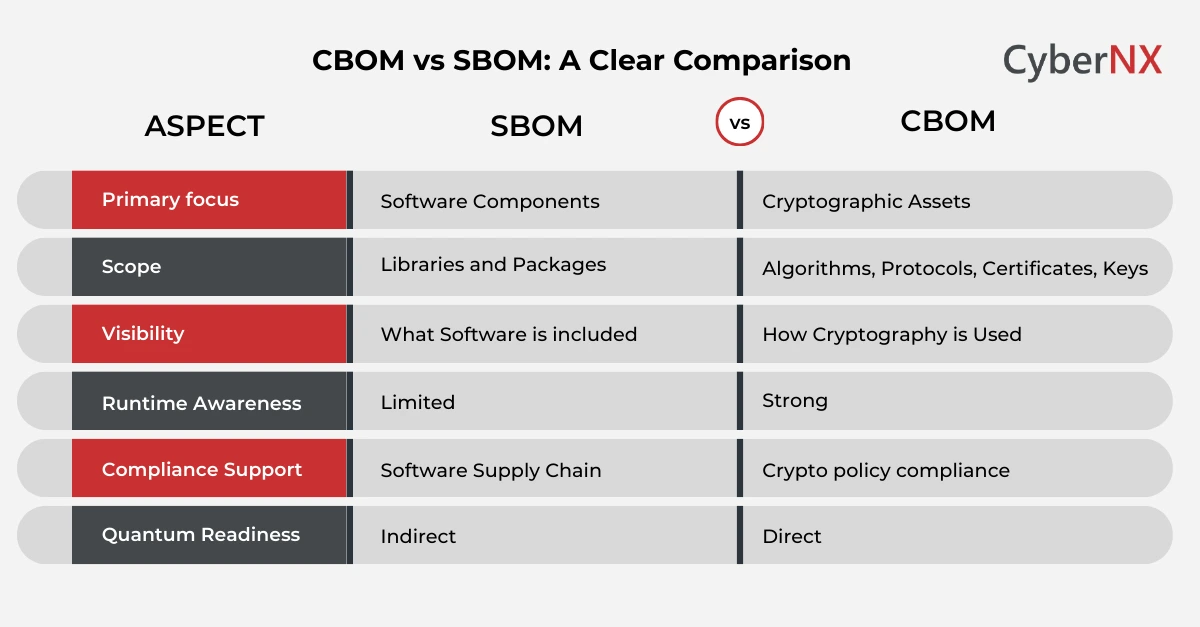
CBOM vs SBOM: A clear comparison
The table below highlights the core differences in a simple way.
This comparison shows why the two serve different but complementary purposes.
How CBOM and SBOM work together
CBOM is not a replacement for SBOM. It is an extension.
SBOM provides the structural view of software composition. CBOM adds a cryptographic layer on top of that structure.
Together, they allow organisations to:
- Trace cryptographic usage back to specific software components
- Understand which applications rely on weak or deprecated algorithms
- Prioritise remediation based on actual usage, not assumptions
- Automate compliance checks against cryptographic policies
This combined view is particularly valuable in large, complex environments where cryptography is deeply nested across multiple layers.
Business impact of choosing the right approach
Understanding CBOM vs SBOM is not just a technical exercise. It affects real business outcomes.
- Better risk prioritisation: CBOM helps security teams focus on cryptography that is actively used, reducing wasted effort on low-impact findings.
- Stronger audit readiness: Auditors increasingly ask for evidence of cryptographic controls. CBOM provides structured answers that SBOMs cannot.
- Faster incident response: When a cryptographic vulnerability emerges, CBOM shortens investigation time by showing exactly where affected algorithms or protocols are in use.
- Smarter long-term planning: For organisations planning cryptographic modernisation or quantum safe transitions, CBOM provides the discovery foundation required to build realistic roadmaps.
When should you adopt CBOM?
CBOM becomes particularly valuable if your organisation:
- Operates in regulated industries such as BFSI, healthcare, or critical infrastructure
- Develops or distributes software to enterprise or government customers
- Manages large numbers of certificates, keys, or encrypted systems
- Is planning for cryptographic agility or post-quantum migration
In these scenarios, SBOM alone will not provide sufficient visibility.
Conclusion
The debate is not CBOM vs SBOM. It is SBOM and CBOM.
SBOM gives you clarity on what software you run. CBOM gives you clarity on how cryptography behaves inside that software. Together, they provide a more complete picture of modern security risk.
As regulatory expectations grow and cryptographic threats evolve, organisations that extend SBOM practices with CBOM will be better positioned to respond, comply, and plan with confidence.
At CyberNX, we help organisations integrate SBOM and CBOM into practical security programs that deliver real visibility, not just documentation. If cryptography is still a blind spot in your environment, now is the time to address it. Connect with us to know about our SBOM management tool and how it can help you achieve supply chain security.
CBOM vs SBOM FAQs
Can CBOM be generated if an SBOM already exists?
Yes, and that is often the best starting point. An SBOM provides the structural view of software components, which CBOM can build on to discover cryptographic assets inside those components. In many cases, CBOM generation reuses SBOM data and enriches it with cryptography-specific findings rather than starting from scratch. This makes adoption faster and more practical.
Does CBOM require access to source code?
Not always. While source code access improves accuracy, CBOMs can also be generated using binary analysis, configuration inspection, runtime observation, and certificate discovery. This makes CBOM viable even for third-party software, commercial off-the-shelf products, and legacy systems where source code is unavailable.
How does CBOM support cryptographic agility?
CBOM enables cryptographic agility by giving organisations a clear map of where algorithms, protocols, and keys are used. Without this visibility, changing cryptography becomes risky and slow. With CBOM, teams can assess impact, prioritise upgrades, and switch algorithms with confidence as standards evolve or threats change.
Will CBOM increase operational overhead for security teams?
Initially, there is some effort involved in setting up tooling and processes. However, over time, CBOM reduces operational load by automating cryptographic discovery and simplifying audits, incident response, and compliance reporting. Instead of chasing scattered information, teams work from a single, structured source of truth.