Cybersecurity can be complex. While employees in your organization look for ease of use while utilizing software and other platforms, threats and vulnerabilities in these systems change every day. Plus, chances of a compromise are always inevitable. In this context, how confident are you in your organisation’s ability to detect and contain a breach?
According to IBM’s Cost of a Data Breach Report 2024, the average time to identify and contain a breach is 204 days. Long enough time for an attacker to exploit systems to their fullest. So, the question is how to build a secure IT environment where your business can thrive? Blue Teaming is the answer.
Blue Teams or your defence team makes it difficult for cyber attackers to breach your systems. They monitor, analyse and respond to threats continuously and immediately.
Read our Blue Team Guide blog for depth and guidance on the topic.
But even the most skilled defenders need the right instruments to perform at their peak. Blue team tools, open-source and commercial, are necessary for shifting detection into foresight and for turning raw logs into actionable intelligence. Plus, these tools give CISOs and CTOs the clarity to act decisively while facing modern threats.
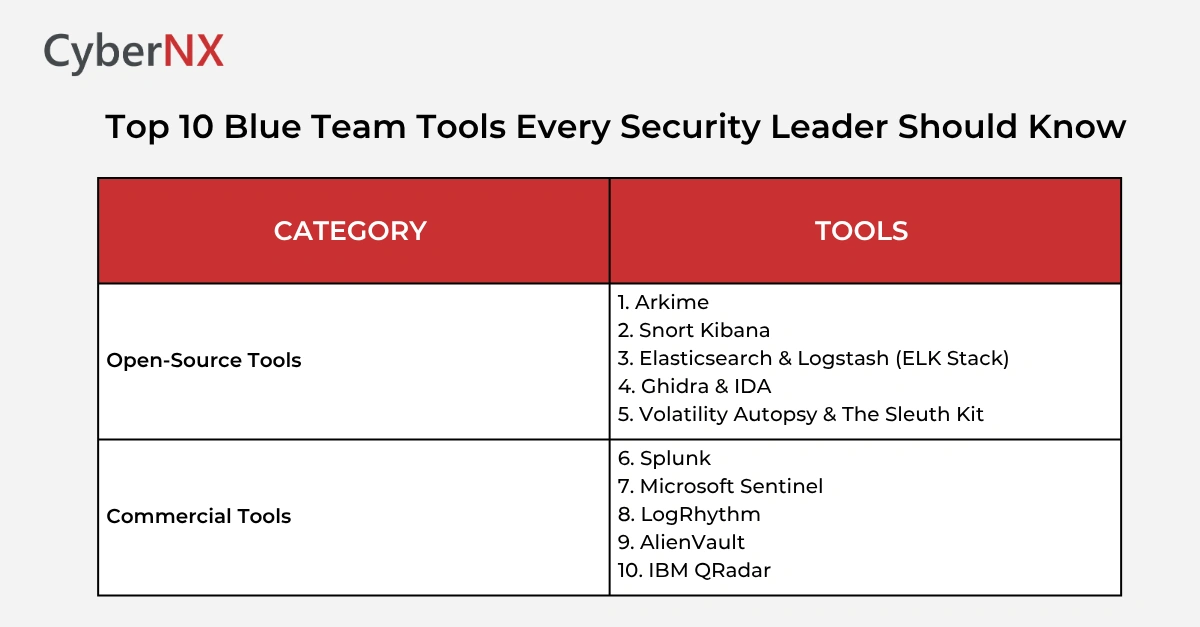
Quick Glance: Top 10 Blue Team Tools Covered in This Guide
A concise list of the essential blue team security tools every modern defender should know.
Open-Source Blue Team Security Tools
Open-source blue team security tools offer flexibility to cybersecurity professionals. They enable teams to adapt and innovate without waiting for vendor updates. These tools often come with active communities from across the world. The knowledge sharing ensures fresh perspectives on threat trends.
1. Arkime
Arkime is a network packet capture platform with scalability feature, apt for growing or expanding businesses. It stores and indexes massive volumes of PCAP data and makes them searchable too. Blue team experts like this tool for its detailed traffic analysis and correlating suspicious patterns across the IT spectrum.
2. Snort
Snort is an intrusion prevention and detection system (IPDS), well-known and excessively used by experts in the blue team field. It analyses traffic in real time, using customisable rule sets to identify and block malicious activity.
3. Elasticsearch + Logstash + Kibana (ELK Stack)
If you are not using commercial blue team tools, this is an effectively close alternative to them. The trio of Elasticsearch, Logstash and Kibana famously called ELK stack, ingests and visualises log data, turning an overwhelming flood of information into clear, searchable dashboards that help spot anomalies in a quick time.
4. Ghidra & IDA
Malware analysis is regarded as a deep rabbit hole kind of process. Gihidra helps security experts reverse engineer the process, allowing defenders to break down malware, suspicious binaries and embedded threats to understand their inner workings.
5. Volatility, Autopsy & The Sleuth Kit
These are open-source forensic tools designed to extract and analyse digital evidence, reconstructing breach timelines and enabling accurate incident reporting.
These blue team security tools are preferred by security teams for their cost-effectiveness and the freedom to customize defences to specific IT environments, depending on the type of industry.
Commercial Blue Team Tools: Stability Meets Scale
Open-source tools excel in flexibility. Commercial platforms deliver enterprise-grade performance, integrated features and professional support. This is important for large organisations where operational downtime is unacceptable.
1. Splunk
Splunk is the go-to tool for large enterprises, known for its powerful analytics and search capabilities. The commercial tool turns petabytes of data into actionable intelligence with real time dashboards and high-fidelity alerts.
2. Microsoft Sentinel
Microsoft Sentinel stands tall as a blue team tool. The features range from being cloud-native SIEM that combines scalability with advanced threat hunting to AI-assisted analytics and easy integration with Microsoft’s security ecosystem.
3. LogRhythm
LogRhythm offers blue teams a well-balanced blend of threat detection, compliance reporting and log management in one unified platform. This commercial team makes life easy for SOC teams.
4. AlienVault
The key features of AlienVault include SIEM capabilities, built-in threat intelligence, vulnerability assessment and asset discovery.
5. IBM QRadar
Essentially a SIEM platform, IBM QRadar is trusted for its ability to normalise, correlate and analyse massive volumes of security data. QRadar is efficient in identifying sophisticated attack patterns, automating compliance reporting and integrating seamlessly with both on-prem and cloud environments.
These Blue Team security tools, as you can guess, are extremely effective in large-scale deployments and enable rapid triage. This, in turn, provides detailed reporting and executive-level visibility, which is key for CISOs and CTOs balancing operational defence with business objectives.
Comparative Glance
A side-by-side view to help security leaders weigh open-source flexibility against commercial-grade stability.
| CATEGORY | TOOL(S) | STRENGTHS | IDEAL FOR |
| Open-Source | Arkime, Snort, ELK Stack, Ghidra, Volatility, Autopsy | Customisable, Cost-Effective, Transparent | Innovation-driven teams |
| Commercial SIEM | Splunk, Sentinel, LogRhythm, AlienVault, IBM QRadar | Polished analytics, Vendor Support, Scalability | Enterprise-wide visibility & ROI |
Conclusion
For CISOs, CTOs and Blue Teamers, the decision should not be about choosing open-source or commercial blue team security tools. Focus on building layered defences where each tool complements the other. Open-source platforms provide flexibility and innovation, whereas commercial solutions offer stability and scalability.
By utilizing valuable blue team security tools in your organisation’s security ecosystem, you ensure that defence is defined by readiness, foresight and resilience.
A stronger defence begins with small, focused steps. We partner with your team to build blue-team practices that improve visibility and resilience. Get in touch for blue team services and let’s plan your next move together.
Blue Team Tools FAQs
How do Blue Team Tools integrate with existing SOC operations?
Blue team security tools can be integrated into a Security Operations Center (SOC) through APIs, log forwarding, and orchestration platforms like SOAR. This ensures that alerts, threat intelligence, and forensic data flow into a central hub, allowing analysts to correlate incidents and respond faster without switching between multiple dashboards.
Are open-source Blue Team Tools secure enough for enterprise use?
Yes – when implemented with proper governance. Open-source blue team tools often have active communities that patch vulnerabilities quickly, but enterprises should conduct code reviews, limit tool access, and apply rigorous configuration management before deployment to reduce potential risks.
How often should an organisation update or replace its Blue Team Tools?
Tool updates should be applied as soon as security patches are released. Full replacements are typically evaluated every 2-4 years, or sooner if the threat landscape changes dramatically, new compliance requirements emerge, or the tool no longer scales with organisational needs.
Can Blue Team Tools help in compliance audits?
Absolutely. Many blue team tools generate detailed logs, audit trails, and incident reports that map directly to compliance frameworks such as ISO 27001, PCI DSS, and HIPAA. This documentation can significantly reduce the time and effort required during external audits.