Gartner predicted that by 2025, over 90% of web-enabled applications will have a larger attack surface exposed via APIs than through the user interface.
That’s probably happening right now as you read.
Application Programming Interfaces or APIs are how software systems communicate to each other. Whether it’s a payment gateway syncing with a shopping cart or a mobile app showing your ride history from a backend, APIs are everywhere.
“How convenient”, we mutter unanimously. But convenience comes at a cost.
Because APIs expose business logic and sensitive data, they are often targeted by attackers. From data leaks and broken authentication to business process abuse, APIs have become a soft entry point.
So how can your business proactively defend APIs before they become a problem? The answer lies in API Penetration Testing.
API Penetration Testing: The Definition
API pentesting can be understood as a controlled, simulated real-world attack on APIs. This is done to identify and fix vulnerabilities before attackers get a chance to exploit them.
How is it different from traditional pen tests? API testing examines business logic, parameter-level validation and user-role segregation.
Here’s an example to understand better:
Imagine a car ride service with an API something like /getFare?distance=10&userID=123. A cyber attacker has the capability to manipulate the parameters and retrieve fares of other users or inject code to disrupt backend processes.
What API penetration testing essentially does is that it plugs these technical loopholes and ensures that APIs enforce business rules as they are intended.
Want to know about other types of Penetration Testing? Check our blog: Types of Penetration Testing: A Complete Overview
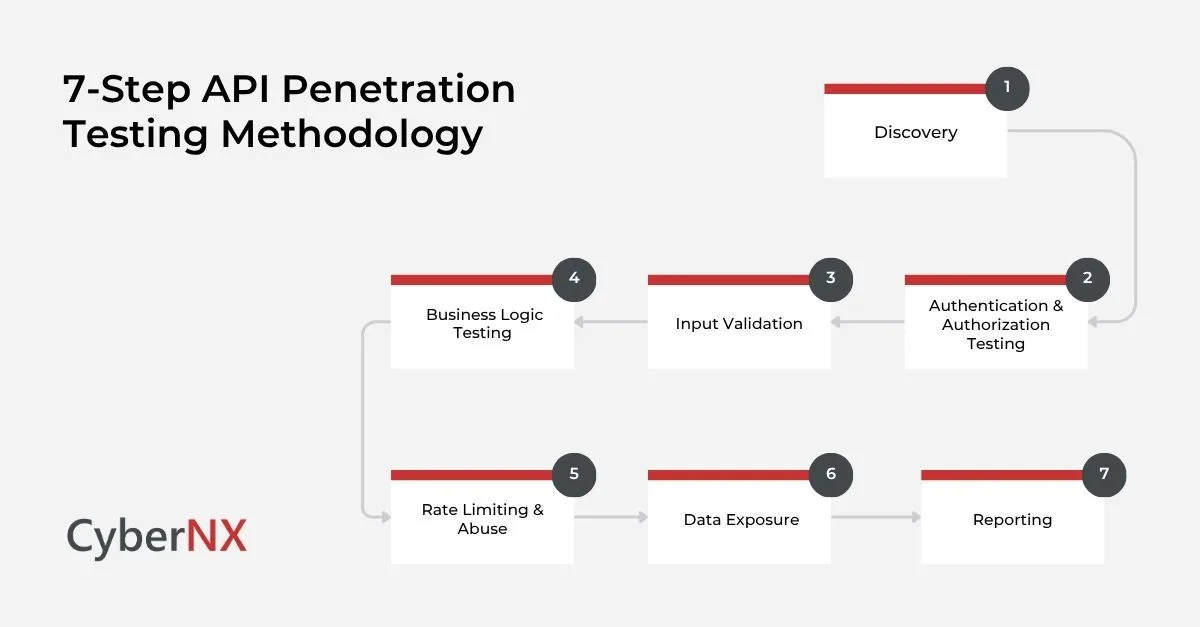
API Penetration Testing Methodology
A solid API penetration testing methodology follows a rigid structure:
1. Discovery:
Identifies and catalogues exposed endpoints. It may involve Swagger/OpenAPI docs, reverse engineering apps or intercepting traffic.
2. Authentication & Authorization Testing:
Validates if tokens, keys and roles are enforced correctly or not. Also tests for token reuse, privilege escalation and access bypass.
3. Input Validation:
Assesses how the API handles malformed or malicious input JSON fuzzing, parameter tampering and content-type changes.
4. Business Logic Testing:
Examines if workflows can be misused or bypassed (For example: skipping payment steps or exceeding discount limits).
5. Rate Limiting & Abuse:
Tests for brute force, enumeration or DoS vectors.
6. Data Exposure:
Analyses how much data an endpoint leaks (metadata, internal IDs, system info).
7. Reporting:
Findings are clearly categorised with risk levels, PoCs and remediation advice.
Common API Vulnerabilities & Best Practices to Avoid Them
API pentesting often reveals a recurring set of vulnerabilities that can expose sensitive business data and allow attackers to exploit system weaknesses. Understanding these common flaws – and knowing how to prevent them – is crucial for any organization that depends on APIs for digital operations.
1. Broken Object Level Authorization (BOLA)
One of the most critical issues found during API pentesting is BOLA. It occurs when APIs fail to properly validate object-level permissions, allowing attackers to access other users’ data simply by changing object IDs. As for best practices, implement strict object-level authorization checks for every API request. Each request should confirm ownership and access rights before returning data.
2. Broken Function Level Authorization
Another frequent vulnerability identified in API pentesting, this issue arises when APIs expose administrative or high-privilege functions to regular users. Here, the best practice will be to enforce robust role-based access control (RBAC) and verify user privileges at the function level for every API endpoint.
3. Mass Assignment Flaws:
In many API pentesting engagements, testers find that APIs accept more parameters than intended. Attackers exploit this by sending unexpected data to modify protected fields. Using parameter allowlists to restrict which fields can be modified and validating inputs strictly are some best industry practices you can follow.
4. Injection Attacks (SQL, NoSQL, Command)
Injection vulnerabilities remain a top finding in API pentesting. Poor input validation enables attackers to inject malicious commands or queries into APIs. In this case, the best practice is to always sanitize and validate user input, use parameterized queries, and avoid directly concatenating input into commands.
5. Lack of Rate Limiting
APIs without proper request throttling can be overwhelmed by brute force or denial-of-service (DoS) attacks. Best practice is to apply rate limiting and API throttling to restrict excessive requests and prevent abuse.
Regular API pentesting helps organizations uncover these vulnerabilities early and ensures secure, reliable API ecosystems.
Scope, Timeline and Cost
API penetration testing scope depends on endpoints, its complexity and the authentication mechanisms in place. In addition, third-party or internal system integrations will expand the scope.
API pen tests may also include testing across different environments like production, staging and development.
As for timelines, it also varies:
- Small application with 10–15 endpoints might take 3–5 days
- A medium-sized one with 30–50 endpoints may require up to 10 days
- For enterprise-level APIs, a full test will take over 2–3 weeks, especially when business logic needs thorough validation.
Cost reflects this complexity involving API pentesting. Cost will be less for simpler APIs as compared to more comprehensive and continuous testing. However, this investment often includes detailed reports, consultation sessions and retesting services.
Black, White and Grey Box Testing – How They Differ for APIs
Black box testing is performed without internal knowledge of the API. The tester simulates an outsider with no access to code or documentation, attempting to discover vulnerabilities by interacting with endpoints as an attacker would.
This is useful for identifying exposed endpoints, misconfigurations and weak authentication. But it can miss deeper logic or permission-based flaws.
White box testing involves full access to source code, API documentation and authentication credentials. It allows testers to deeply evaluate role-based access, input validation and error handling.
This is ideal for understanding internal workflows and catching sophisticated flaws that surface only under specific conditions.
Grey box testing is balanced. It provides limited access such as developer accounts or partial documentation, mimicking the perspective of an insider or semi-privileged user.
This approach is highly effective in mimicking real-world scenarios, especially in large organizations where internal threats are a concern.
Each type of API penetration testing methodology offers unique value, and a layered approach that combines all three often provides the best results.
API Penetration Testing Across the SDLC
Implementing API penetration testing throughout the Software Development Lifecycle (SDLC) transforms it from a point-in-time activity to a continuous assurance process.
- In the design phase, threat modelling helps software developers to anticipate potential API issues.
- During development phase, tools like linters and secure coding standards helps in preventing insecure API calls from being written.
- In the testing phase, security test cases are integrated into CI/CD pipelines. It enables rapid feedback on new features.
- In deployment, pre-production environments are tested to simulate live traffic and after release, continuous monitoring and retesting detect regressions and new risks.
For businesses, API integration brings many benefits. For one, it reduces the cost of fixing bugs later in the development process. Additionally, it shortens time-to-market by catching issues early. Finally, testing ensures APIs can scale securely.
Tools and Techniques: API Penetration Testing
API pentesting combines automation and manual efforts. Here are some tools recommended by our experts:
- Burp Suite Pro: Used for intercepting, manipulating and fuzzing API traffic.
- Postman: Enables API exploration, test scripting and collection-based testing.
- OWASP ZAP: Open-source scanning tool with powerful scripting support.
- Insomnia: Lightweight API client is good for REST and GraphQL testing.
- Nikto or Dirsearch: Very useful for endpoint enumeration and surface mapping.
- JWT.io or HackBar: Helpful for token decoding and on-the-fly manipulation.
- SoapUI or mitmproxy or Fuzzapi: Best for SOAP, proxying and fuzzing.
Challenges and Benefits
API penetration testing comes with its set of challenges. Many APIs lack proper documentation, making it hard to discover all endpoints.
Emerging protocols like gRPC or asynchronous GraphQL APIs introduce additional complexity. Testing is often throttled by built-in rate limits or anti-bot measures. Most importantly, business logic flaws are unique to each application and rarely detectable via automation alone.
Despite these challenges, the benefits are significant. Web API penetration testing helps prevent data breaches, enforces secure development practices and builds stakeholder trust.
It also improves regulatory posture for GDPR, SOC 2, or HIPAA compliance. Ultimately, it protects your business operations from silent but severe failures in API security.
Conclusion
APIs are gateways to digital services. With growing reliance on microservices and third-party integrations, securing APIs is important.
API penetration provides a strategic lens on how well your digital backbone is defended. CEOs, CTOs and founders should see it as a proactive investment that safeguards brand, revenue and customer loyalty.
If you are looking for a API penetration testing service provider, contact our experts at CyberNX. We are a leading pentesting company with rich experience of partnering with hundreds of clients, experts with certifications and tools and techniques to deliver best security outcomes.
Contact today!
API Penetration Testing FAQs
Why is API penetration testing methodology necessary if we already have secure coding practices?
Even with secure development, APIs can have logic flaws, misconfigurations, or access control gaps that only real-world attack simulations can uncover. Penetration testing validates security beyond the code and ensures that business logic, authentication, and data exposure risks are thoroughly tested in live environments.
When is the ideal time to implement API penetration testing methodology in our development cycle?
The best time is just before major releases or after integrating third-party services. Ideally, testing should be integrated into the CI/CD pipeline to detect issues early, reduce remediation costs, and ensure secure delivery with every deployment.
Do we need to test internal or private APIs too?
Yes. Internal APIs can be exploited by malicious insiders or through compromised endpoints. Security should not rely on network boundaries. Testing all exposed interfaces ensures consistent protection across your entire architecture.
What deliverables should we expect from a professional API penetration testing?
A full report outlining discovered vulnerabilities, severity levels, real-world impact, reproduction steps, and prioritized remediation guidance tailored to your business context. You may also receive executive summaries, risk matrices, and post-engagement consultation for deeper understanding and action planning.