The cybersecurity landscape is in constant flux, with cyberattacks growing in sophistication and frequency. We have moved beyond simple malware to face threats that adapt and evolve in real-time.
Artificial intelligence (AI), while offering incredible potential for defensive cybersecurity, is also being weaponised by malicious actors.
This necessitates a new breed of defence: AI Penetration Testing.
This blog post will explore this crucial security mechanism and guide CISOs on navigating this new frontier.
The Changing Face of Cybersecurity
Cyberattacks are no longer simple smash-and-grab operations. They’re intricate, targeted and often leverage the very technologies we rely on.
AI plays a dual role in this landscape. While security teams are exploring AI-driven threat detection and response, attackers are also harnessing its power for more effective and evasive attacks.
This makes AI Penetration Testing, a proactive approach to identifying vulnerabilities in AI-powered systems and defences against AI-driven attacks, more critical than ever.
Understanding the Blend of AI and Penetration Testing
Let us demystify some key concepts about AI Pen testing here.
- Artificial Intelligence, in its simplest form, is about enabling computers to perform tasks that typically require human intelligence.
- Within AI, Machine Learning (ML) focuses on algorithms that allow computers to learn from data without explicit programming.
- Deep Learning (DL) uses complex neural networks to analyse vast amounts of data.
Traditional penetration testing involves simulating cyberattacks to identify vulnerabilities in systems and networks. However, traditional methods often struggle to keep pace with the speed and adaptability of AI-powered attacks.
This is where AI comes into play. AI is transforming penetration testing by automating tasks, enhancing analysis and simulating more realistic attack scenarios.
The Surging Demand for AI Penetration Testing
The rise of AI-powered attacks is a serious concern. Malicious actors are using AI for:
- Automated vulnerability discovery: AI can scan systems for weaknesses far faster and more comprehensively than humans.
- Adaptive malware: AI-powered malware can learn and adapt to security measures in real-time, making it harder to detect and neutralize.
- Social engineering attacks: AI can craft highly personalized and convincing phishing emails or social media scams.
Traditional security solutions and penetration testing methods, designed for more conventional attacks, are often ill-equipped to handle these AI-driven threats.
AI Pen testing offers a proactive defence, enabling organizations to identify and mitigate these vulnerabilities before they can be exploited, leading to a surge in its demand.
Read: Top 10 AI Pentesting Tools: Reviewed by Experts (2025)
AI Penetration Testing: A Deep Dive
AI Pen testing focuses on identifying vulnerabilities in AI-powered systems and defences against AI-driven attacks. It goes beyond traditional penetration testing by incorporating AI techniques to simulate and counter these advanced threats.
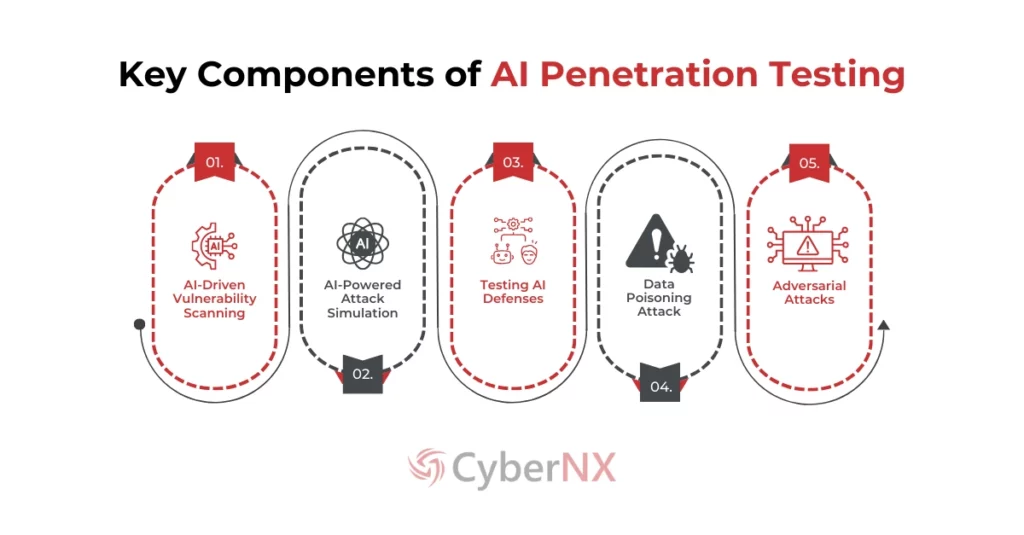
Key Components of an AI Penetration Test:
- AI-Driven Vulnerability Scanning: AI automates and enhances vulnerability scanning by identifying patterns and anomalies that might be missed by traditional tools. This involves leveraging automated penetration testing tools and AI tools specifically designed for penetration testing
- AI-Powered Attack Simulation: AI can simulate realistic attacks, including those that leverage AI techniques like adversarial attacks and data poisoning, providing valuable insights into an organization’s resilience.
- Testing AI Defences: AI Pen testing evaluates the effectiveness of existing AI-based security solutions, ensuring they can detect and respond to AI-driven threats.
- Data Poisoning Attacks: AI Pen testing assesses an organization’s vulnerability to data poisoning attacks, where malicious data is injected into training datasets to manipulate AI models.
- Adversarial Attacks: These attacks subtly manipulate input data to fool AI systems. AI Pen testing checks for robustness against such adversarial examples.
Benefits of AI Pentesting
All things said, what benefits does AI Pen testing offer to your business? Find the answer below:
- Enhanced Vulnerability Discovery: AI can uncover hidden vulnerabilities that might be missed by traditional methods.
- Proactive Risk Mitigation: Identifying and addressing vulnerabilities before they are exploited minimizes potential damage.
- Improved Security Posture: AI Pentesting strengthens the overall security posture of an organization.
- Compliance and Best Practices: Many compliance standards and frameworks recommend or require advanced security testing like best AI for pentesting.
Conclusion: Embracing the Future of Cybersecurity
AI Penetration Testing is no longer a luxury but a necessity in today’s threat landscape. As AI becomes more prevalent in both attack and defence, understanding and mitigating its risks is paramount.
Contact CyberNX Technologies – Your CERT-IN Empanelled Penetration Testing Partner today for a free consultation or security assessment. Let’s discuss your AI Penetration Testing needs.
FAQs
What is the difference between traditional penetration testing and AI pentesting?
Traditional pentesting relies on manual techniques and tools to identify vulnerabilities. AI penetration testing leverages artificial intelligence to automate tasks, enhance analysis, and simulate more realistic, AI-driven attacks. It specifically focuses on identifying weaknesses in AI systems and defences against AI-powered attacks.
Why is AI penetration testing necessary?
Traditional security measures often struggle to keep pace with the speed and sophistication of AI-powered attacks. AI pentesting provides a proactive approach to identify and mitigate vulnerabilities before they can be exploited by malicious actors using AI.
What types of vulnerabilities does AI penetration testing uncover?
AI pen test can uncover a range of vulnerabilities, including weaknesses in AI models, data poisoning vulnerabilities, susceptibility to adversarial attacks, and vulnerabilities in AI-based security systems themselves. It also assesses the effectiveness of your defences against AI-driven attack vectors.
What skills are required for AI pen testing?
AI pentesting requires a combination of cybersecurity expertise, knowledge of AI and machine learning, and familiarity with specialized tools and techniques. It’s best performed by experienced professionals with expertise in both areas.
How much does AI pen test cost?
The cost of an AI pen test varies depending on the scope and complexity of the assessment. Factors influencing the cost include the number of systems being tested, the depth of the analysis, and the expertise of the penetration testing team. Contact CyberNX for a tailored quote.
Can AI pentesting be automated entirely?
While AI can automate many aspects of penetration testing, human expertise remains crucial. Interpreting results, designing sophisticated attack simulations, and developing effective remediation strategies require human judgment and creativity. AI is a powerful tool to augment, not replace, human pen testers.