“By 2028, multiagent AI in threat detection and incident response will rise from 5% to 70%,” says a report from Gartner. The projection is a wake-up call for organizations still undecided or reluctant on using Artificial Intelligence (AI) for security.
Security Operations Center (SOC) continue to face immense pressure against the onslaught of sophisticated, advanced and AI powered cyberattack campaigns in complex IT environments. AI driven SOC help security teams to match their adversaries by fundamentally changing how SOC teams detect, investigate and respond against modern threats.
AI upgrade of SOC boosts the speed, scale and precision of all the processes, giving SOCs the muscle to defend against today’s relentless threat landscape with ai driven soc automation.
What is an AI Driven SOC?
AI driven SOC involves the use of Artificial Intelligence and Machine Learning across SOC functions. What it essentially does is that it speeds up everything, from detection of anomalies to investigation and response actions, addressing the security concerns in shortest time.
AI driven SOC, developed under the guidance of experienced professionals and experts, are meant to help SOC teams and not to replace humans.
In fact, AI models analyse data across endpoints, networks, users and cloud platforms to identify patterns, predict threats and prioritize actions. A boon for SOC analysts. AI even recommends next steps based on the context.
Read our blog on SOC Guide to have better clarity about what SOC is, how it works, key benefits, KPIs that matter and more.
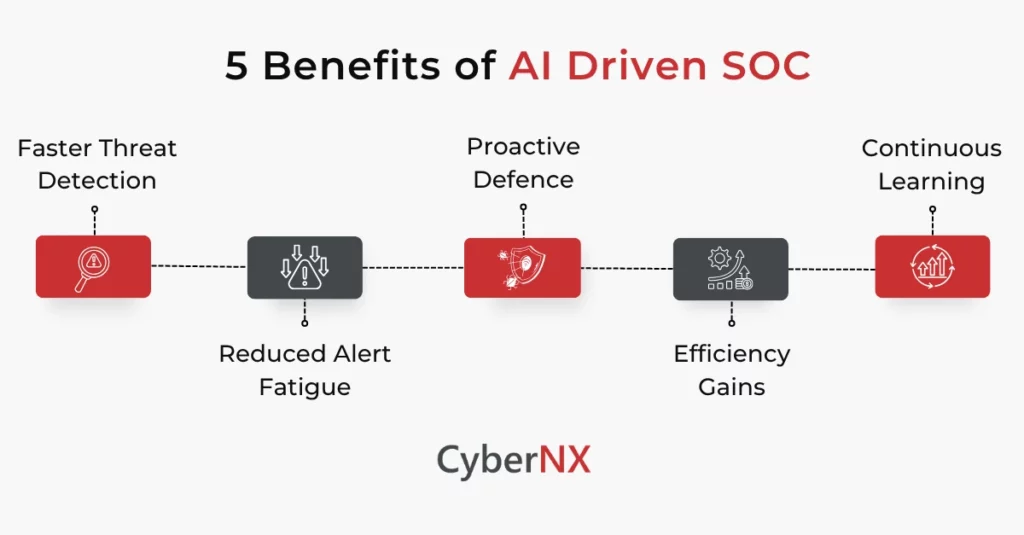
Benefits of AI Driven SOC
AI driven SOC means that many of the repetitive tasks are taken care by AI. Trained on past data, AI amplifies intelligence and transforms security operations. Here are the other benefits:
- Faster threat detection: AI algorithms spot anomalies in large volume of data sets that human analysts may otherwise miss. What it does? Well, AI reduces mean time to detect (MTTD), an important metric in the process.
- Reduced alert fatigue: ML models learn over time which alerts are false positives and which need attention. And once the model achieves that level of efficiency, it drastically cuts noise.
- Proactive defence: One of the biggest takeaways is predictive analytics, capable of identifying suspicious behaviours. This prevents threats to escalate into breaches.
- Efficiency gains: AI completely eliminates repetitive tasks, enabling SOC analysts to focus on high-priority threats or other security projects.
- Continuous learning: AI models improve with feedback, becoming smarter over time with real-world inputs. And under the guidance of experts, AI can deliver superior performance, helping organizations achieve better performance and ROI.
How AI Transforms Core SOC Functions
The goal of AI driven SOC should be to transform each step in the SOC lifecycle. This makes it easy for organizations and their security teams to use such services.
1. Detection
AI algorithms scan millions of logs and telemetry data in real time to catch stealthy attacks.
Example: In a finance company, AI would flag a rarely used admin account accessing sensitive records at odd hours, something a traditional system may overlook.
2. Investigation
Natural Language Processing (NLP) can summarize complex threat events and surface relevant indicators of compromise (IOCs).
Example: An AI engine can stitch together logs from email, endpoints and DNS traffic to uncover a phishing-led lateral movement.
3. Response
AI-powered SOC SOAR tools suggests or triggers responses based on predefined rules or risk levels.
Example: Upon detecting ransomware behaviour, the AI driven SOC will auto isolate the infected host and block outbound C2 communication.
4. Remediation
In case of an attack, AI recommends configuration fixes, patches and workflow changes to prevent reoccurrence.
Example: After mitigating an exploit, AI will suggest patching a vulnerable Apache server and updating internal firewall rules. This helps even the junior analysts in case a senior is not available immediately.
5. Reporting
AI can auto-generate detailed incident reports for compliance and executive briefings.
Example: A healthcare company SOC can use AI to summarize a breach timeline for HIPAA reporting in a quick time.
AI’s Role in SOC Tools
AI is transforming the SOC tools, thereby making the SOC process smarter and efficient. Find out how below:
1. Endpoint Detection and Response (EDR)
AI-enhanced EDR tools use behaviour analytics to identify fileless malware or advanced persistent threats (APTs) that traditional signatures are unable to catch. Read our blog on EDR tools to learn more.
2. Security Orchestration, Automation, and Response (SOAR)
AI is quite helpful in generating automated playbooks and decision-making trees. It assists SOAR systems to learn from past incidents, adapt responses and correlate data across tools. Find out more with our blog on SOAR Tools.
3. Vulnerability Management
AI simplifies patching by predicting which vulnerabilities are most likely to be exploited in your specific digital environment.
4. Threat Intelligence Platforms
AI curates threat feeds, de-duplicates IOCs and aligns them to threat landscape, offering actionable intelligence to analysts.
Related Content: Top 5 SOC Tools for Security Operations
Conclusion
Your organization should see AI driven SOC as an upgrade to the SOC team that is already protecting your entire IT environment. It is a crucial evolution for modern organizations facing modern cyber threats.
The key here is to blend human insight with machine intelligence. Our AI Managed SOC as a Service, offers exactly that and helps organizations across India and the world protect their business 24X7. Contact us to know more.
AI Driven SOC FAQs
How does an AI-driven SOC handle zero-day threats?
AI-driven SOCs use behavioural analytics and anomaly detection to identify unusual patterns rather than relying solely on known signatures. This approach enables them to detect zero-day attacks – threats that exploit previously unknown vulnerabilities. For example, if an endpoint begins exhibiting behaviours such as privilege escalation attempts, network scans, or lateral movement that deviate from its baseline, the AI flags it even if no existing signature exists. This predictive capability allows SOC teams to investigate and respond before damage escalates.
What skills are required for analysts in an AI-driven SOC?
While traditional SOC skills like threat analysis and incident response remain crucial, analysts in an AI-driven SOC need to evolve with the tools. They should understand how AI models interpret data, how to validate machine-generated alerts, and how to fine-tune detection logic based on false positives and evolving threats. Familiarity with SOAR platforms, scripting for automation (e.g., Python), and data interpretation also helps analysts collaborate effectively with AI tools rather than treating them as black boxes.
Is AI-driven SOC suitable for SMBs or only large enterprises?
AI-driven SOC capabilities are no longer exclusive to large enterprises with deep budgets. Many cybersecurity vendors now offer AI-infused SOC-as-a-Service (SOCaaS) tailored for small and medium-sized businesses. These platforms combine automated detection, managed threat hunting, and continuous monitoring without requiring a large in-house security team.
How can organizations ensure AI in SOCs is trustworthy and reliable?
Trusting AI in security operations means ensuring transparency, accountability, and explainability. AI models must be continuously updated with new threat intelligence, monitored for drift, and integrated into human-in-the-loop processes. A well-designed feedback loop allows analysts to validate and correct AI outputs, reducing biases and improving precision over time. Regular audits and ethical evaluations of AI logic further help align technology with business risk tolerance and compliance needs.