The threat landscape today is volatile, so much so that security operations teams are under constant pressure to detect, investigate and respond to incidents at speed. Security Operations Centers (SOCs) of past years are simply not enough to keep up with this pace.
When the gap between alerts and response grows wider, cybercriminals exploit them with increased frequency. SOC automation tools, powered by AI, machine learning and data orchestration gives that much-needed speed, agility and success. These tools fundamentally reshape how modern SOCs operate and boost productivity.
As a modern organization, SOCs are beneficial to your security posture. Therefore, you must know the key features of the SOC automation tools that are upgrading SOC team and their performance.
Related Content: Security Operations Center (SOC): The Brain Behind Modern Cyber Defence
What are SOC Automation Tools?
SOC automation tools are solutions that basically accelerate security operation processes. They automate repetitive, manual and time-consuming tasks. These tools integrate with SIEMs, EDRs and threat intelligence feeds to unify security data. Plus, these automate incident detection, triage and response.
Unlike legacy solutions, these automation tools act as digital analysts rather than depending on human intervention. The SOC tools ingest alerts, contextualize threats, assign priority and even initiate remediation with little to no manual effort.
They save time, accelerate decision making and allow security teams to focus on complex threats and reducing dwell time.
Benefits of SOC Automation Tools
Implementing SOC automation is a technical upgrade and a strategic move for organizations looking to take their security posture to the next level. Notable advantages include:
- Reduced Alert Fatigue: Analysts get a breather and do not get overwhelmed by low-priority alerts. Instead, they can focus on high-impact threats.
- Faster Incident Response: Automated triage and playbooks cut mean-time-to-respond (MTTR) dramatically, a key metric to assess the SOC performance.
- Improved Accuracy: AI reduces any possible human error and false positives, making detection more accurate and reliable.
- Scalability: As threats grow, SOC automation helps teams maintain control without needing to scale headcount proportionally.
- Better Compliance: Automated logging, documentation and reporting simplify audits and ensures you are aligned with the regulatory needs.
Key Features of SOC Automation Tools
Modern Security Operations Center (SOC) automation tools are packed with capabilities that go far beyond alerting or rule-based response. The standout features that define next-gen solutions are discussed below:
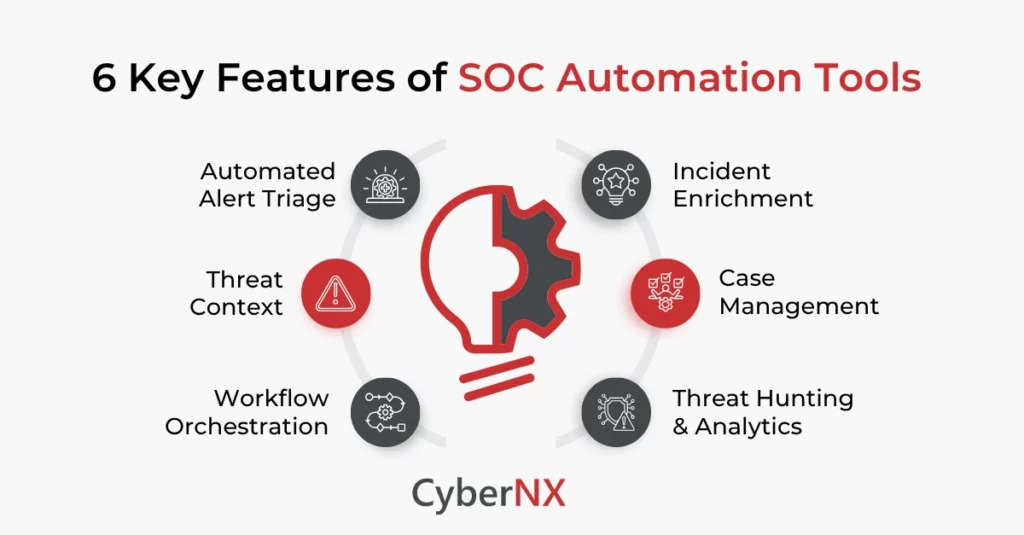
1. Automated Alert Triage
Security Operations Center automation tools use Artificail Intelligence models to accelerate the assessment process of incoming alerts for severity, false positives and context. This drastically reduces unwanted noise and ensures that SOC analysts only see the alerts that matter the most.
2. Threat Context
Intelligence without proper context is meaningless. SOC automation tools aggregate internal logs and external threat intelligence, offering a complete picture of the incident. Security teams get to know important information like who is behind it, what tactics are used, and which assets are affected.
3. Workflow Orchestration
Upgraded continuously, the predefined playbooks automate end-to-end response tasks such as blocking IPs, isolating endpoints, initiating scans, without manual intervention. Moreover, integration with ticketing systems ensures that everything is tracked.
4. Incident Enrichment
SOC tools gather data from different sources like SIEM, EDR, IDPs and threat feeds to enrich alerts with user behaviour, asset details and external reputation scores, making triage faster and accurate.
5. Case Management
Automation helps with built-in dashboards and collaborative investigation features. This enables teams to assign roles, document findings and maintain audit trails without much hassles.
6. Threat Hunting & Behavioural Analytics
By automating data queries and correlating across logs, SOC automation tools assist analysts in proactive threat hunting, reducing the need to start investigations from scratch. Some tools leverage UEBA (User and Entity Behaviour Analytics) to detect anomalies, insider threats and lateral movement patterns that may otherwise go unnoticed.
Best Practices for Using SOC Automation Tools
To fully realize the benefits of Security Operations Center automation tools, organizations need to adopt these best practices:
- Integrate Broadly: Integrate your SOC tool with platforms like SIEMs, EDRs, threat intelligence platforms, identity systems and ticketing software for a unified view.
- Start with High-Impact Use Cases: Initially, you should implement automation for repetitive, tedious tasks like alert triage, IP blocking and phishing response.
- Continuously Tune Playbooks: Use the power of automations to frequently update workflows as the threat landscape and business needs evolve.
- Measure ROI: Track metrics like MTTR, number of automated responses and reduction in manual alerts to evaluate success.
- Ensure Analyst Involvement: Always combine automation with human oversight for to achieve better decision-making goals on complex threats.
Top SOC Automation Platforms
Here are the top SOC automation platforms which can help your business boost security operations:
1. CyberNX
A fast-growing AI managed SOC service provider, CyberNX combines automation with expert-driven managed services. With 24X7 monitoring, real-time alerting and custom-built playbooks, CyberNX enables organizations to detect, triage and respond to threats faster and effectively, especially in regulated industries like BFSI, healthcare and fintech.
2. CrowdStrike Falcon
Known for cloud-native architecture and real time threat intelligence, CrowdStrike provides detection and automated response capabilities backed by its elite OverWatch threat hunting team.
3. SentinelOne Singularity
With a strong focus on AI-driven detection and autonomous response, SentinelOne provides full visibility into endpoints along with automated containment and rollback features.
Related Content: Top SOC Tools That Strengthen Enterprise Cybersecurity
Conclusion
Speed, precision and scalability are the game changers for security teams today. SOC automation tools are central to achieving all of them. By blending AI, orchestration and real time data processing, the SOC automation tools reduce analyst burnout and strengthen your organization’s cyber resilience.
Our AI driven SOC service can help your organization fortify most critical digital assets, 24X7X365. Contact us to know more.
SOC Automation Tools FAQs
What’s the difference between a SOC platform and a SOC tool?
A SOC platform offers a broad, centralized solution—think of it as the command center that connects various tools, playbooks, and workflows under one roof. A SOC tool, on the other hand, performs specific tasks like phishing analysis, log correlation, or case management. While platforms are ideal for end-to-end visibility, tools can be integrated to enhance specific functions.
Can small and mid-sized businesses benefit from SOC automation?
Absolutely. SOC automation isn’t just for large enterprises. SMBs often operate with lean security teams and limited budgets—automation helps bridge that gap by reducing manual workload, prioritizing alerts, and accelerating response time without hiring additional analysts. Cloud-based automation platforms also make adoption more cost-effective.
Does SOC automation eliminate the need for human analysts?
No. While automation handles repetitive, rules-based tasks with speed and accuracy, human analysts are still crucial for complex decision-making, threat hunting, and tuning automation rules. The best SOCs strike a balance between machine efficiency and human intuition—a hybrid approach that ensures no threat goes unnoticed.
How do SOC automation tools stay up to date with evolving threats?
Modern SOC tools continuously ingest threat intelligence feeds, behavioural data, and machine learning insights to adapt to emerging attack patterns. Some platforms even auto-update their detection logic or playbooks based on new vulnerabilities, threat actor TTPs (Tactics, Techniques, Procedures), and global threat landscapes.