If you are trying to find out what penetration testing is and how it can boost the security posture of your organisation, you are in the right place.
Because in this blog post, our team of cybersecurity experts are going to tell you all there is to know about Pen testing and more.
We are currently helping 200+ clients in India and abroad secure their respective businesses every day. And we are here to tell you exactly how pen testing works and why it must be in your security arsenal in 2025 and beyond.
So, let’s get started.
Introduction
At the outset, this might put things into perspective: financial institutions, government entities, law enforcement agencies, military and yes, private organisations use penetration testing. Are you?
In a digital-first world, where everything and everyone is connected, cyber threats are evolving, growing and reaching yet unknown levels. From sophisticated ransomware shutting down healthcare facilities to sensitive data leaks crippling financial institutions, cyber criminals are running rampant.
Make no mistake, startups and small businesses aren’t safe either, sometimes causing irreversible damage.
This is where penetration testing steps up as a gem of a solution, not just to counter but to take the attack to the cyber attackers.
Bhowmik Shah, one of our co-founder adds, “As the threat landscape evolves and takes different forms right in front of our eyes, businesses must start to see testing as a necessity. And in our observation, serious businesses are no longer taking security lightly as compared to the last decade.”
What is Penetration Testing? Our Experts Decode
Penetration Testing, often referred to as Pen testing or Pen test, is a process where your digital infrastructure, which includes computer systems, applications, networks etc. are tested for vulnerabilities or weaknesses.
Is it that simple? No.
To better understand what penetration testing is, imagine a cyber attacker hacking into your systems, exploiting vulnerabilities, accessing sensitive data and leaving your business in tatters. Now come back to reality.
Penetrating testing services include professionals who do everything as a hacker would do in the real-world – but here is the difference – with your permission and taking you into confidence.
The main goal of pen testing is to discover weaknesses and fix them before malicious attackers can exploit those loopholes.
Moreover, it provides a realistic picture of existing status of your organisation’s security posture – whether it is weak, strong or somewhere in between.
Penetration Testing: Why Does Your Business Need It?
Now that you know what is penetration testing, let’s go deeper. Shall we?
We have come up with top 5 reasons why your business needs penetration testing, further expanding on the points discussed in the last section.
Impactful Evaluation
As our expert pointed out, organisations face an ever-expanding array of threats in the form of phishing, ransomware, social engineering, zero-day exploits and insider attacks. Thorough and impactful evaluation of all risk levels and multiple surfaces helps your business to prioritise remediation efforts.
For example, if you are operating in a cloud environment and vulnerabilities exist, pen testing enables you to use a proactive and intelligent method to defend data and assets in the cloud.
Regulatory Standpoint
If you are in the finance industry, you know regulatory bodies mandate penetration test to comply with data protection laws. It includes, but is not limited to, PCI-DSS, HIPAA, GDPR, RBI, SEBI and others.
Failure to comply results in hefty penalties, unwanted legal consequences and loss of customer trust.
Additionally, running security tests consistently prove to your customers, investors, partners and other associates that you are serious about protecting sensitive data and supporting transparency, which brings us to the next point.
Business Enabler
In the hyper-connected digital world, a penetration test services can be a business enabler.
Wondering how?
Well, implementing security testing and other cybersecurity best practices positions your company as a forward-looking, proactive and modern company. It can certainly act as a catalyst in mergers and acquisitions and in closing important deals.
Imagine conducting your first discussion with a big potential business partner, and you have a CISO showcasing your security posture. When people trust you, it automatically results in more business.
Prevent Costly Data Breaches
Look at this staggering stat: “USD 4.88 million was the global average cost of a data breach in 2024. And this is a 10% increase from last year and the highest total ever,” according to a report released by IBM. What about the reputational damage caused and the resulting financial losses? A pen test fixes the security gaps before it can lead to such breaches.
Internal Security Awareness
Sometimes, IT teams can get too familiar with all the systems that they may miss the holes. Pen testing comes up as a wakeup call, revealing misconfigurations and weak access controls.
Besides, employees are the biggest asset as well as threat for an organisation with security loose ends. Expert-led pentesting can expose employee weaknesses, opening opportunities for awareness, training and establishing policy frameworks.
Bhowmik Shah adds, “We have seen cases where pen test has transformed the whole mindset of an organisation – right from leaders at the top to the employees working at the level one. It also helps in developing a security culture within the organisation, which I believe is the key.”
Types of Penetration Testing (Protection on All Fronts)
IT infrastructure has different parts – from networks and applications to people and devices. Therefore, pen test is not a one-size-fits-all solution. It is completely up to you to either choose protection on all fronts or where you need it the most.
Web Application Penetration Testing
Web apps are the primary touchpoint for customers in the present digital transformation era. This makes them the primary attack surface. To keep them safe, web app pentesting targets internal and public-facing applications and examines SQL injection, XSS, authentication bypass, broken access control & more.
Our expert reveals that web application penetration testing service is the most requested test today.
Mobile Application Penetration Testing
Mobile is the present and the future. As services go down the mobile road, mobile applications pentesting assesses insecure data storage, improper session handling and reverse engineering risks. It ensures APIs and code are secure.
Cloud Penetration Testing
With many companies shifting to Azure, AWS and GCP, cloud pen test service has gained significance among SaaS and enterprise companies. In addition, cloud breaches due to misconfigurations are increasing. The main targets include misconfigured S3 buckets, insecure APIs and identity & access management flows.
Wireless Penetration Testing
As the name suggests, this type investigates wireless access points and Wi-Fi networks for poor encryption protocols and unauthorised access. Real-world simulation of evil twin attacks and rogue access is used. Organisations with a remote work culture and Bring-Your-Own-Device (BYOD) choose this test.
Social Engineering Penetration Testing
Phishing emails, physical infiltration or tailgating and phone pretexting are some methods employed to manipulate employees into revealing sensitive information inside the organisation. The key objective is to assess employee awareness and how they follow security policies.
API Penetration Testing
This involves simulating real-world attacks on application programming interfaces to identify weaknesses like data exposure, broken authentication and improper access controls. API pentesting type is critical to design secure APIs and protect sensitive data from unauthorised access.
Network Penetration Testing
Routers, firewalls, servers – key components of internal and external network infrastructure are tested to identify vulnerabilities. Attempts are made by the professional pentesters to exploit weak network configurations, find open ports and implement spoofing techniques. This is done to find out if a hacker could get access to network.
Check out our blog on Types of Penetration Testing for an in-depth understanding of the topic.
The Process Behind the Scenes
Like we mentioned in the “what is penetration testing?” section, here you will learn the process behind the scenes.
The penetration test service includes a structured process or methodology. Cybersecurity service providers follow standards like OWASP, OSSTMM, NIST framework or others.
Here’s a breakdown of pen test phases that will give your business clarity:
Planning and Scoping
Goals are defined as to what systems or apps will be tested. Scope includes the business continuity safeguards plus the written consent for the test.
Intelligence Gathering
Open-source intelligence (OSINT) is used for intelligence gathering. Domains are identified plus employee information & server details are extracted
Vulnerability Assessment & Scanning
A wide range of tools like Nmap, Nessus are used to discover open ports, services and other vulnerabilities.
Exploitation
Vulnerabilities found are exploited using frameworks such as Metasploit. In addition, test for privilege escalation, data exfiltration or lateral movement is done.
Evaluation
Thorough evaluation is carried out to find what damages can be done by a real-world attacker and evidence is captured.
Reporting
A detailed report will include a summary, technical findings, proof of concept, rating of risk and remediation guidelines. Read our blog How to Read and Leverage Penetration Testing Report to know how it can help your business.
Retesting
Once vulnerabilities are fixed, retesting is done to validate the effectiveness of the patches done.
Remember, the pen test process will differ from one company to another. To have a comprehensive understanding of different phases, check out this blog: Find Everything to Know About Penetration Testing Phases.
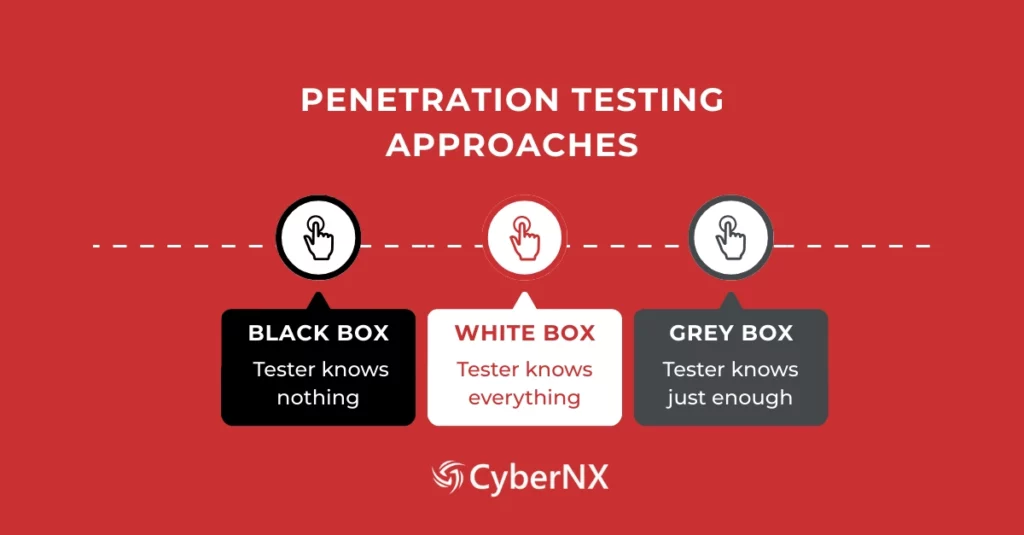
Penetration Testing Approaches – Make Your Choice
If your business decides to do penetration test, there are three approaches the service provider will put in place: Black Box Testing, White Box Testing and Grey Box Testing. These three approaches differ in the information shared by you with the professional team of pentesters.
Find out what they are and make your choice:
Black Box Testing
No internal information is provided to the pentesting team. This means that your business is targeted as a real cyber attacker would. The experts will use data available in the public domain and discovery techniques. Since it mimics a hacker, it is best for testing perimeter defences.
White Box Testing
This is the opposite of black box testing. Full details are provided to the tester, which include source code, network architecture and system documentation. The advantage is that pentesting experts find hidden vulnerabilities and logic flaws which may otherwise seem impossible.
Grey Box Testing
This is a hybrid approach, where partial information is provided to the testers. Because of the balance it offers, many companies opt for the grey box testing approach.
Note that the approach you choose will influence the depth and breadth of pen test outcomes. Learn how Black Box vs White Box Penetration Testing affect your test scope.
Penetration Testing Methodologies
Penetration testing methodologies provide structured approaches for assessing and improving an organization’s cybersecurity posture. These frameworks ensure tests are consistent, comprehensive, and aligned with industry standards.
By simulating real-world attacks, ethical hackers use these methodologies to uncover vulnerabilities before malicious actors do. A well-defined methodology not only improves testing accuracy but also boosts stakeholder confidence in security efforts. The top five widely recognized penetration testing methodologies include:
- OWASP Testing Guide
- NIST SP 800-115
- OSSTMM (Open Source Security Testing Methodology Manual)
- PTES (Penetration Testing Execution Standard)
- ISSAF (Information Systems Security Assessment Framework).
Dive deeper into methodologies in our blog Top 5 Penetration Testing Methodologies.
Challenges? Yes, There Are!
What challenges do businesses face when wanting to carry out pen test? For one, finding professional and trusted pentesters with technical knowledge and business know-how is sometimes daunting. Operational disruption can happen with unskilled pentesters.
The evolving and advanced threat landscape brings a new set of vulnerabilities. Occasional penetrating testing does not work.
Funnelling resources into comprehensive and continuous pentesting remains a challenge. Because certain types of penetration testing services can be costly.
How Do I Choose the Right Penetration Testing Partner?
- Certifications, certifications! The first factor to consider is credentials as well as certifications. Trusted and reliable cybersecurity companies have qualified experts with OSCP, CEH, GPEN, CREST certifications.
- Secondly, you shouldn’t overlook experience in the industry, as they know the common vulnerabilities and in-depth weaknesses of industries and may provide deep insight into them. Always ask about previous work, clients and domain expertise.
- Look for transparency in the discussion stage. Go for companies who offer complete information about their methodology, tools used and sample reports.
- Finally, evaluate what kind of support do the company offer post the testing phase. Choose the ones that deliver maximum value plus ongoing collaboration promise.
Conclusion
In 2025, organisations should move on from passive security defence options.
In the modern world, where businesses are opting for cloud, adopting digital transformation and racing for advanced technologies – active and continuous intelligence about their security posture is a must.
Penetration testing offers that and much more.
Knowing what is penetration testing is the first step but acting on it is what will truly matter for your business. Secure your business today!
How Can CyberNX Help?
CyberNX offer Proactive and Persistent Penetration Testing Services. Proactive because identifying and exploiting vulnerabilities drastically reduces your organisation’s security risks. And with our persistent approach, we don’t stop with surface-level checks, but dig deep to uncover vulnerabilities, strengthening your security posture and helping your business stay ahead of real-world threats.
Our human-led and automation-enabled pen testing opens security improvement opportunities, letting your business focus on core objectives and achieve growth.
Contact our experts today to know more about our penetration testing services.
FAQs
Typically, how long does a penetration test take?
Penetration tests would take anything between 2 to 4 weeks, depending on the scope, systems involved and the complexity of the given environment. Contact our experts to know more. If you are looking for ongoing security, explore Continuous Penetration Testing.
Can you tell the objective behind doing penetration test?
Simply put, the objective is to detect and resolve security vulnerabilities before attackers could. This helps your business to protect digital assets, meet regulatory standards and focus on company goals.
How much does a penetration test cost?
Pricing will vary depending on the scope, complexity and the types of assessment done. Talk to our experts for more information.
How do I convince leadership at my company to do penetration testing?
To convince leadership, present penetration testing as a proactive investment in protecting business assets. Emphasize the financial, reputational and operational risks of undetected vulnerabilities, and how testing helps prevent costly breaches. You can also highlight industry-specific compliance requirements (e.g., PCI-DSS, ISO 27001, HIPAA) that mandate or strongly recommend pen testing. If needed, our team is available to provide supporting materials or assist in stakeholder discussions.