The Securities and Exchange Board of India (SEBI) introduced the Cybersecurity and Cyber Resilience Framework (CSCRF) to elevate the cybersecurity posture of its Regulated Entities (REs). This comprehensive framework outlines core principles, key objectives, and recommended technical tools to help REs enhance their cybersecurity capabilities and ensure compliance with regulatory standards.
The Five Core Goals of CSCRF
The CSCRF framework is designed to build cyber resilience across five key goals:
- Anticipate: Maintain proactive preparedness to identify and prevent potential cyberattacks.
- Withstand: Ensure business continuity even in the face of successful cyber incidents.
- Contain: Localise and isolate the impact of cyber events to minimise damage.
- Recover: Restore systems, processes, and operations swiftly after an incident.
- Evolve: Continuously adapt cybersecurity measures to address the dynamic threat landscape.
Cyber Security Tools Recommended Under CSCRF
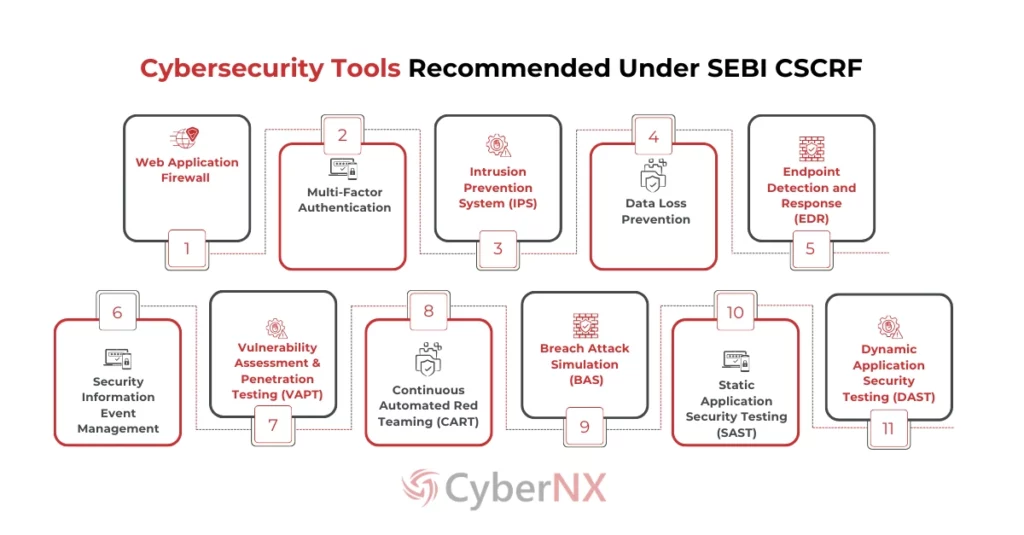
The CSCRF framework encourages organisations to implement advanced cyber security tools and technologies to strengthen their overall cybersecurity capabilities. Below is an overview of the cyber security tools suggested in the framework:
1. Web Application Firewall (WAF)
A WAF protects web applications by filtering, monitoring, and blocking harmful HTTP traffic. It defends against common threats such as cross-site scripting (XSS), SQL injection, and denial-of-service (DoS) attacks.
2. Multi-Factor Authentication (MFA)
MFA requires users to verify their identity using two or more factors—such as a password, a physical token, or biometrics. This prevents unauthorised access even if passwords are compromised.
3. Intrusion Prevention System (IPS)
An IPS monitors network traffic for malicious activities and actively blocks threats like DoS attacks, worms, and viruses before they can cause harm.
4. Data Loss Prevention (DLP)
DLP solutions prevent sensitive data from leaving an organisation’s control by monitoring and restricting data movement across email, web browsing, and file sharing.
5. Endpoint Detection and Response (EDR)
EDR monitors endpoint devices for suspicious activity, helping detect and mitigate malware, investigate compromised devices, and respond to threats.
6. Security Information and Event Management (SIEM)
SIEM tools collect and correlate security data from multiple sources, providing insights into potential threats and supporting compliance with regulatory requirements.
7. Vulnerability Assessment and Penetration Testing (VAPT)
VAPT involves identifying vulnerabilities in systems and applications and testing their exploitability to strengthen an organisation’s security posture.
8. Continuous Automated Red Teaming (CART)
CART continuously simulates attacks to identify vulnerabilities and strengthen defences before real-world exploitation.
9. Breach and Attack Simulation (BAS)
BAS tools mimic real-world attack scenarios to assess an organisation’s security posture and identify improvement areas.
10. Static Application Security Testing (SAST)
SAST analyses source code for vulnerabilities such as SQL injection, buffer overflows, and XML external entity (XXE) attacks during the development phase.
11. Dynamic Application Security Testing (DAST)
DAST identifies vulnerabilities in live applications by testing against known sources like the OWASP Top 10.
12. Dark Web Monitoring
Dark web monitoring tracks stolen credentials or sensitive data related to an organisation to mitigate risks of identity theft or breaches.
13. Decoy Technology
Decoy assets attract attackers, allowing organisations to detect and respond to potential threats proactively.
14. Privileged Identity Management (PIM)
PIM solutions secure privileged user accounts with elevated access to critical systems, reducing the risk of misuse.
CyberNX: Your Partner in CSCRF Compliance
At CyberNX, we specialise in implementing and maintaining compliance with the SEBI Cybersecurity and Cyber Resilience Framework. Our expertise ensures that your organisation adheres to SEBI’s regulatory requirements while strengthening its overall cybersecurity posture.
With a structured approach, we provide:
- Tailored solutions to meet specific compliance needs.
- Comprehensive implementation and ongoing support for CSCRF cyber security tools.
- A reliable framework for enhancing cybersecurity and resilience.
Contact us today to ensure your organisation meets SEBI CSCRF standards and stays ahead in the cybersecurity landscape.