Gain visibility into software components with
SBOM Solutions
We offer end-to-end automation from collection to analysis, ensuring complete visibility into software components. Plus, our continuous security monitoring protects you against vulnerabilities & compliance risks.
Talk to our Experts Today





















INTRODUCTION
Better Security and Compliance with CyberNX SBOM Solutions
Enhance your security and compliance posture with CyberNX’s comprehensive SBOM solutions, delivering deep component insights, automated vulnerability detection and compliance tracking across your entire software supply chain.
Key Features:
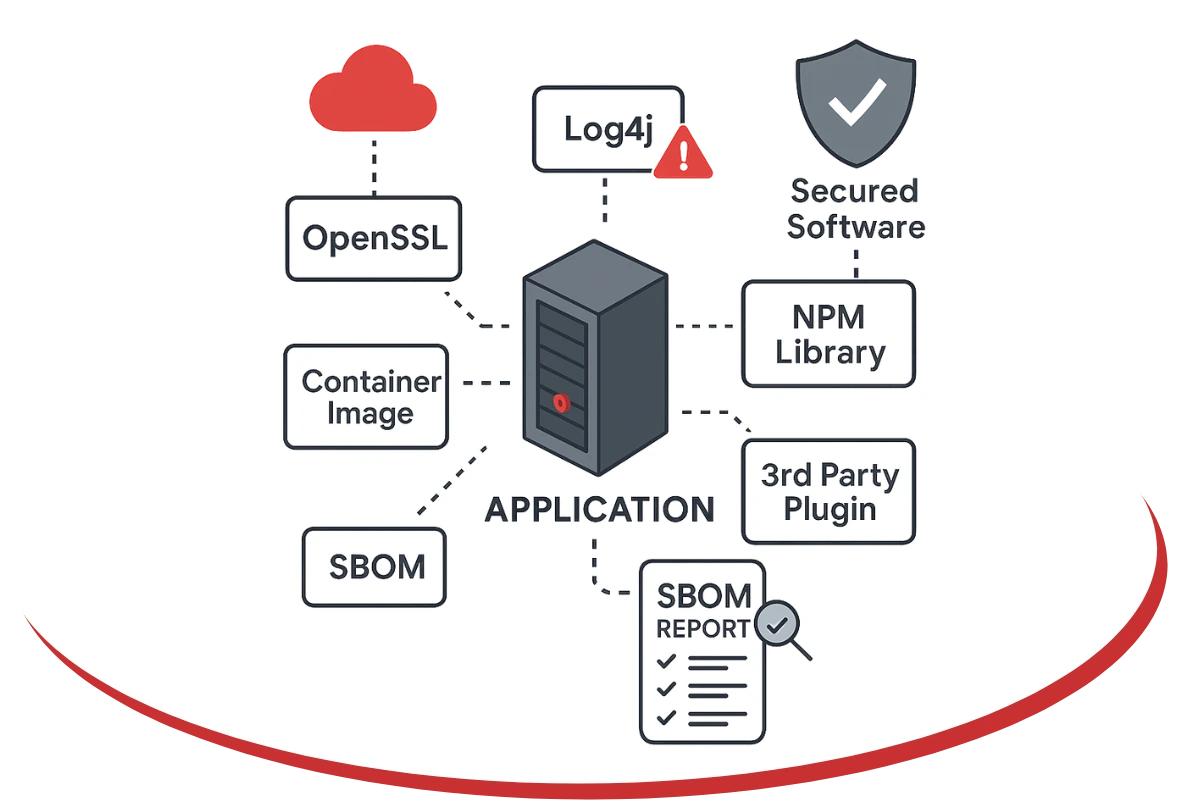
Offers visibility into the complete inventory of software components and dependencies, and information about those components.
Meets RBI, SEBI CSCRF’s SBOM mandates for Regulated Entities, and helps with other regulatory requirements.
Provides continuous monitoring and tracking of vulnerability status as components change and conducts risk assessment.
Offers multiple deployment models to meet your organization’s specific requirements for security, compliance and operational needs.
Complete awareness of components, relationship between components, versions, licenses, encryptions and cryptographic hashes.
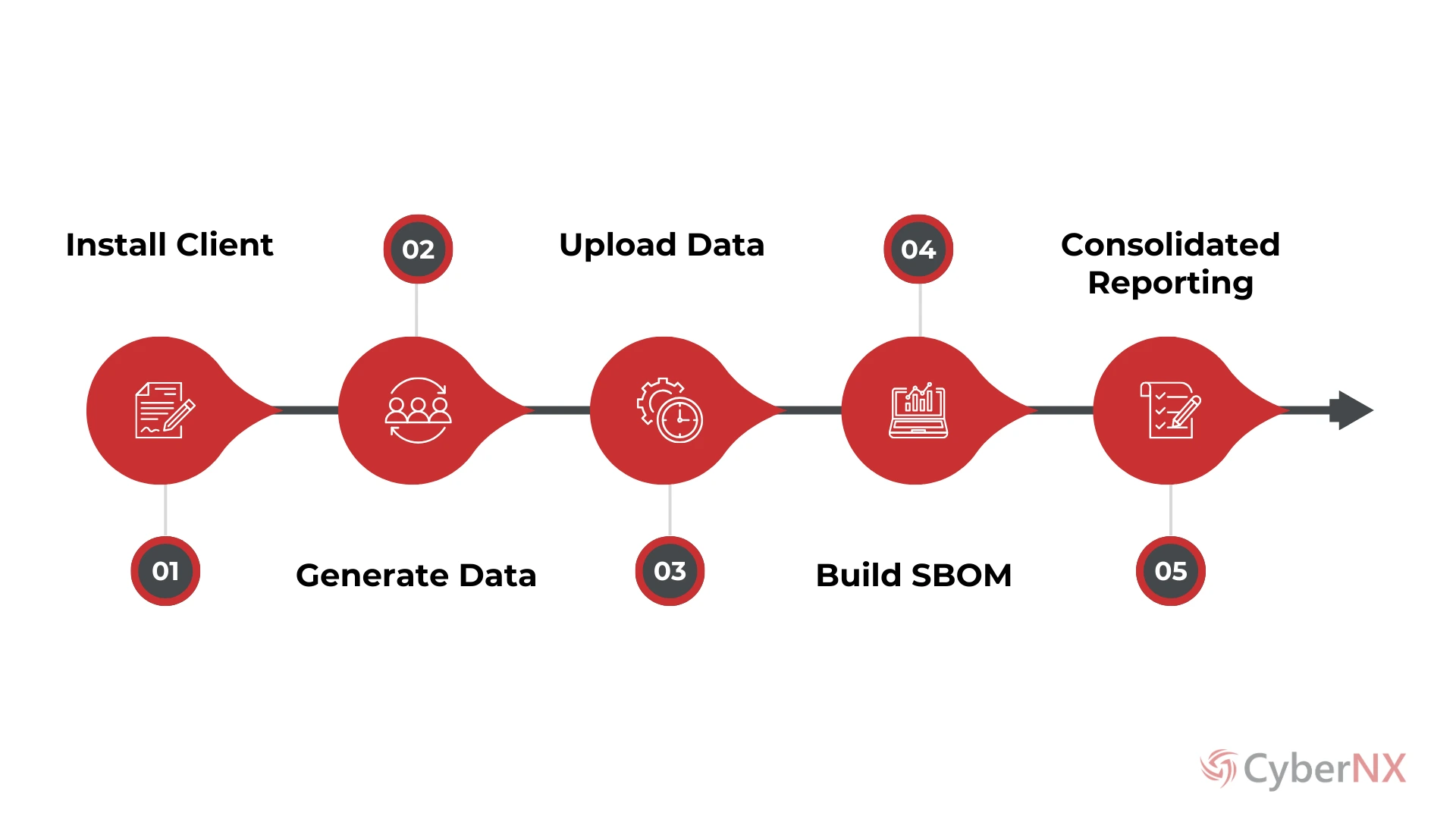
How It Works?
APPROACH
Why Choose CyberNX SBOM Solutions?
Our advanced SBOM solutions are powered by automation that reduces manual efforts and errors, easily integrates with existing workflows and offers continuous monitoring and updates.
Automated Collection
We automate SBOM gathering from multiple sources such as container and registry scanning, and vendor SBOM ingestion.
Centralized Management
We offer a secure SBOM repository with version control & tracking, data normalization, and cross-environment visibility.
Continuous Analysis
Our solutions enable real-time vulnerability monitoring, risk-based prioritization, impact assessment and automated threat detection.
Actionable Insights
Compliance-ready reporting, trend analysis & custom metrics & KPIs help make informed decisions.
Best Practices
Follow best practices like automating SBOM creation in CI/CD pipeline, defining SBOM policies and more.
Secure Your Software Supply Chain with our SBOM Management Solutions
BENEFITS
Our SBOM solutions: Automated, Scalable and Compliant
Enhanced Security
Quickly identify and address vulnerabilities when new threats emerge, protecting software from security risks.
Risk Management
Continuously assess and mitigate risks in your software supply chain for safer, efficient software delivery.
Regulatory Compliance
Meet compliance requirements from SEBI, RBI, and other global authorities through component-level documentation.
Complete Transparency
Gain complete visibility into all software components and dependencies across your products.
Tailored Deployment
Supports deployment models like on-premise and SaaS, tailored to organization’s operational needs.
For Customised Plans Tailored to Your Needs,
Get in Touch Today!
Customer First Approach is our Guiding Principle.
RESOURCES
Cyber Security Knowledge Hub
FAQs
Frequently Asked Questions
We install industry-accepted SBOM raw data capturing tools on your server to capture raw files. These are uploaded to our SBOM processing server to build reports as per parameters recommended by regulatory bodies such as SEBI or RBI.
No personal information or sensitive data is captured by our SBOM services. The SBOM file contains only components used, licenses, dependencies, and related technical metadata.
One-time generation typically takes 2-3 weeks. Quarterly setup with first-time scanning can be completed in 3-4 weeks.
Our SBOM generation follows standards recommended by SEBI, RBI, and international frameworks like NIST and SPDX formats.
Our SBOM services support all major programming languages including Java, .NET, Python, Node.js, PHP, Ruby, Go, and more. Our tools can analyse both open-source and proprietary components.
Yes, we support Docker containers, Kubernetes deployments, and traditional server-based applications. Our agents can scan container images and running containers.
No, our lightweight agents run with minimal system impact and do not require application downtime. The scanning process runs in the background without affecting performance.


