Who needs a Security Operations Center (SOC)? Businesses that handle sensitive customer data, those who need to meet mandatory compliance requirements and maintain continuous operations. And that covers most modern organizations today.
You would agree that cyber threats have become frequent. It is quite challenging to predict who is the next target. This is where setting up a Security Operations Center is necessary for businesses aiming to protect their entire digital infrastructure.
Now you might imagine SOC as a room with screens and tech tools. Although it is close to it, SOC should be seen as the brain behind modern cyber defence. A mission control room or a console with highly structured, intelligence-driven functions unifying all key security elements – people, process and technology. The aim? To help detect, respond to and recover from security incidents 24X7.
Security Operations Center is a huge advantage for a business today as it reduces risk, limits damage and maintains trust with customers and stakeholders all the time.
What is SOC?
Consider Security Operations Center as a command center, from where everything related to your digital ecosystem present in the organization is either managed or supported.
SOC continuously monitors, detects, analyses and responds to cybersecurity incidents. Skilled personnel, defined processes and a suite of technologies combine to safeguard all your digital assets – from servers, databases and workstations to apps, endpoints and networks.
The SOC team consisting of engineers, analysts and threat hunters work in real time and use advanced tools to monitor logs, investigate alerts, hunt for threats and coordinate responses. Plus, SOC ensures compliance with data protection laws. One key highlight of Security Operations Center is that it makes sure an organization is always ready to act by designing security measures and protocols to combat future threats.
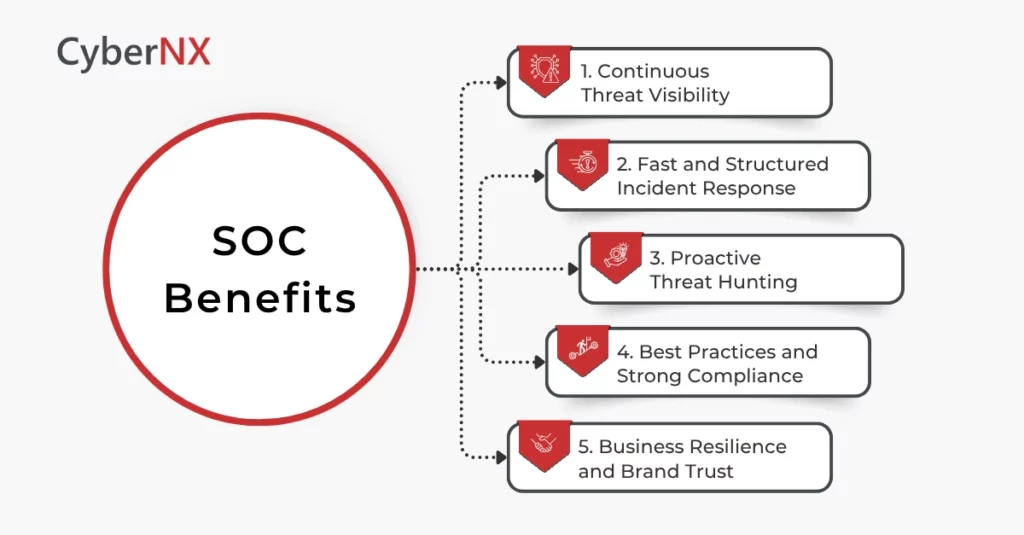
Key Benefits of Having a Security Operations Center
A thought-out, strategically built SOC delivers several benefits for an organization:
1. Continuous Threat Visibility
By now, we know that cyberattacks can occur at any time. SOC teams tackle this challenge head on. They use advanced tools that scan and provide round-the-clock visibility into network traffic, endpoints, applications and cloud environments. This ensures that blink-and-a-miss does not happen even with the mildly suspicious threats.
2. Fast and Structured Incident Response
Whenever a threat is identified, SOC teams are the first to arrive on the scene. With well-defined workflows and trained responders, SOCs take fast action, containing and mitigating incidents in an appropriate manner. In addition, the experts reduce potential damage and ensure business continuity.
3. Proactive Threat Hunting
Security Operations Center do not wait for alerts from potential issues. Instead, threat hunters in the team proactively search for signs of hidden threats like malware using behavioural analytics, threat intelligence and past attack patterns.
4. Best Practices and Strong Compliance
Security Operations Center help organisations in multiple ways; by helping them follow best security practices and meeting government regulations like GDPR, HIPAA and PCI-DSS. Industries like BFSI, healthcare and fintech benefit a lot from SOC functions, preventing them from hefty penalties by supporting compliance through centralized logging, audit trails and continuous monitoring.
5. Business Resilience and Brand Trust
Security Operations Center enforces continuous learning, pushing for effective use of the latest technologies, assessing the security health and strengthening the foundation of IT and digital infrastructure. This prevents breaches, minimizes downtime and secures businesses, boosting brand reputation.
How a Security Operation Center Operates?
SOC in cybersecurity revolves around a structured and continuous cycle that comprises detection, analysis, response and improvement. Here’s how it works:
1. Preparation
Before anything else, SOC takes stock of the assets that need protection, sets up tools, processes and designs policies required to monitor the digital environment. This includes configuring SIEM and SOAR systems, integrating endpoints and creating response playbooks.
2. Monitoring and Detection
Security Operations Center use multiple tools to collect and correlate data from across the organization. For example, security tools feed logs from servers and databases into a central SIEM platform, where analysts monitor unusual activities.
3. Alert Triage and Investigation
Based on the severity rating and potential impact, SOC analysts prioritize alerts and escalate the same to internal teams or take action by themselves. Low-risk events may be dismissed or logged, while high-priority incidents trigger detailed investigations.
4. Incident Response
Once a threat is identified and confirmed, the SOC team immediately springs into action and executes a response plan. The actions can range from isolating affected systems and deleting malicious files to revoking credentials and blocking IP addresses.
5. Recovery and Post-Incident Review
Once the issue is resolved, SOCs review what happened, how it was handled and what can be improved. Detection rules are fine-tuned, and teams reimagine processes based on lessons learned.
What Constitutes a SOC Team?
Once your organization decides to partner with a SOC service provider, you would want to know what constitutes the team and whom you will be dealing with. Key Security Operations Center roles in a security lifecycle are discussed.
- SOC Manager: Every SOC team will consist of an operation head, who will ensure policies are followed, incidents are documented reports are delivered. Plus, the SOC manager makes sure that the team is well-trained and stays updated and coordinated.
- Security Engineers: These are the people who design, deploy and maintain advanced and cutting-edge SOC tools and platforms. This includes tuning SIEMs, UEBA, configuring firewalls and integrating endpoint detection systems like XDR and MDR.
- Analysts: Tie1, 2 and 3: SOCs consist of multi-tier analysts. Tier 1 analysts monitor dashboards, assess incoming alerts and escalate threats that require deeper analysis. Tier 2 professionals dig into suspicious activity, perform forensic analysis and investigate how an attack occurred.
Incident responders or threat hunters constitute Tier 3 analysts. These experts manage complex attacks, reverse-engineer malware and develop detection rules. - Threat Intelligence Analysts: They gather commercial threat intelligence from reliable and trusted external sources with the purpose of understanding latest attacker tactics, tools and trends. This helps SOC teams to stay ahead of emerging threats.
Core Functions and Tools of a Security Operations Center
Security Operations Center carries out several critical functions to protect organisations from cyberattacks. These include:
- Real-time monitoring of networks, servers, endpoints, and cloud environments to detect anomalies or uncharacteristic system details
- Logs from multiple sources are collected for correlation and thorough analysis
- Alerts are prioritized as per their severity
- Incident management
- Threat hunting where experts proactively look for threats
- Behaviour analysis
- Vulnerability detection and risk assessment
- Helps with regulatory compliance and reporting requirements
To conduct these functions effectively, SOCs rely on a vast technology stack that includes:
- SIEM (Security Information and Event Management): Gathers and analyses logs from across the IT environment. For example, if your servers receive a DDoS attack, experts could assess the problem in the SIEM platform.
- SOAR (Security Orchestration, Automation, and Response): Automates repetitive tasks and accelerates response actions. A good example is data leaks that could occur through databases. Such malicious activity is detected via UEBA. Now a SOC analyst uses the SOAR platform to receive data from across these tools which will guide the whole team to collectively orchestrate a response.
- EDR/XDR (Endpoint/Extended Detection and Response): EDR and XDR provide deep visibility into endpoints and beyond. Threat hunters used these tools to search for threats. For example, malware in workstations.
Read our blog EDR vs XDR to know the difference between the two. - NDR (Network Detection and Response): Focused on the network, the NDR tool monitors traffic for any possible suspicious patterns.
- Threat Intelligence Platforms: Offers the latest, valuable contextual information about existing and emerging threats and vulnerabilities. Plus, it offers deep insight into attacker behaviour.
- Case Management Tools: Helps track incident progress and ensure nothing falls through the cracks.
SOC Service Models: What are Your Options?
Every organization has different security needs which depend on the business size, budget and risk profile. So are the different SOC service models available:
- In-House SOC: In this model, your organization will have complete control over tools, processes and people. It is ideal for large enterprises with strict data control requirements. However, it is costly to maintain plus a shortage of skilled professionals can be a serious issue.
- Managed SOC (MSSP): The whole SOC functions are handled by a third-party provider. This model gives businesses expert support without the overhead, making it suitable for small to midsize companies.
- Hybrid SOC: In this model, your internal security team works with external SOC provider. For example, the internal team handles day shifts while an MSSP covers nights and weekends. Plus, you can outsource specific security tasks to the external SOC.
- Virtual SOC: This is a cloud-based, remote service model that offers flexibility, scalability and cost-effectiveness. Quite helpful for businesses that operate in distributed or digital-first environments.
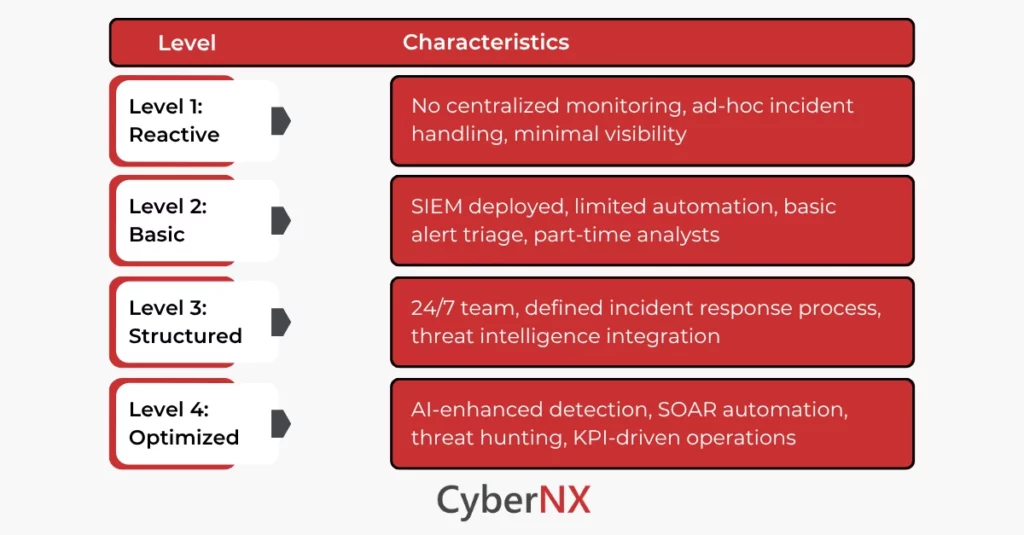
SOC Maturity Model: Where Do You Stand?
Understanding where your organization currently stands can help define the next steps for security improvement. Here’s a simplified four-stage maturity model according to which you can choose what kind of SOC model you want:
Most small to medium businesses fall between Levels 1 and 2, while large enterprises or highly regulated firms aim for Levels 3 and 4.
SOC Performance Metrics and KPIs That Matter
Executives and security leaders always would want to evaluate SOC effectiveness based on measurable outcomes. Here are some key metrics you can use to monitor and optimize SOC performance:
| Metric | Description |
| Mean Time to Detect (MTTD) | Average time taken to identify a security incident after initial compromise |
| Mean Time to Respond (MTTR) | Average time from detection to full containment/remediation |
| False Positive Rate | Percentage of alerts investigated that turn out to be non-malicious |
| Analyst Efficiency | Number of alerts triaged per analyst per shift |
| Detection Accuracy | Ratio of correctly identified threats vs missed threats |
| Incident Volume | Number of security incidents handled per month or quarter |
| Time to Containment | Time from detection to successful isolation of the threat |
| Automation Rate | Percentage of processes handled without human intervention |
Security leaders can track these metrics and help businesses identify bottlenecks, justify investments and continuously improve SOC operations.
SOC vs MDR: What’s the Difference?
A quick glance, and you may think SOC and MDR are the same. On a deeper level, they serve different purposes.
SOC has a broader scope and function covering all aspects of security monitoring, from detection and investigation to response and compliance. It supports a wide range of tools and has multiple use cases. MDR (Managed Detection and Response), on the other hand, is a service that combines advanced detection technologies with human-led response.
In simple terms, if Security Operations Center is the control room, MDR is more of a rapid response team to handle threats quickly and efficiently.
Related Content: MDR vs SOC Explained: Which Managed Service Best Fits Your Security Needs?.
Common Challenges Faced by SOCs
Despite the advantages security operations center offers, organizations may face several real-world challenges. They are discussed below:
1. Alert Overload
With alerts generated daily, your SOC analysts would struggle to distinguish real threats from false positives. And without AI, automation and prioritization, critical incidents can be missed.
2. Skill Shortages
Security Operations Center consist of different roles that require deep technical skills, experience and constant learning. Due to workforce shortage, many organizations find it hard to attract and retain talent.
3. Complex Tool Environments
A SOC is a control unit managing myriad tools that need to work together seamlessly. However, integrating and optimizing them might be time-consuming for in-house teams and can lead to gaps in visibility.
4. 24/7 Staffing and Burnout
For in-house SOC teams, maintaining round-the-clock coverage will be challenging. Without proper planning and sometimes proper extended support, teams can face fatigue and probably high turnover.
5. Evolving Compliance Requirements
Regulations keep changing, sometimes overnight. Security Operations Centers need to adapt quickly to the changes to help organizations stay compliant, document incidents and maintain audit-ready systems.
AI in SOC: How Artificial Intelligence & GenAI are Transforming Cyber Defence
Artificial Intelligence, just like everything else, is revolutionizing the Security Operations Center. Making Security Operations Center faster, more adaptive, and more scalable. With the growing volume and complexity of cyber threats, AI can become a force multiplier for your organization.
How Traditional AI Supports SOC Teams
As soon as you put AI in the room, the process becomes fast.
- Alert Prioritization: Filters through hundreds and thousands of logs to flag the most critical threats, which otherwise takes a lot of time manually.
- Anomaly Detection: Fastens the process of identifying behaviour that deviates from recorded, known baselines.
- Automated Triage: Speeds up matching alerts against known IOCs and triggers playbooks.
- Threat Intelligence Correlation: Links external threat feeds with internal telemetry quickly and efficiently.
How Generative AI (GenAI) is Redefining the SOC
Generative AI goes a step further from traditional AI. How? By extending a helping hand to human analysts in real-time decision-making, communication and investigation. The use cases below prove it.
- Incident Summarization: Creates incident reports automatically by compiling logs, user activity and remediation steps in human-readable formats, saving time and effort.
- Threat Hunting Assistant: With Generative AI, analysts can just ask natural language questions like “Show me lateral movement patterns over the last 24 hours.” It immensely helps in uncovering hidden attacks in the fastest time possible.
- Playbook Generation: GenAI helps SOC teams create new response workflows based on incident types and past behaviour and keep updating them for efficiency.
- Real-time Recommendations: In certain scenarios, GenAI can be used to receive response suggestions by junior analysts, reducing reliance on deep expertise and taking action when necessary.
- Security Awareness Content Creation: Crafts internal alerts, training material and phishing simulations customized to the organizational context.
Benefits of AI-Driven SOCs
Instead of AI replacing human analysts, it will empower SOC teams to operate faster and with greater precision by:
- Reducing analyst fatigue and increasing coverage
- Improving response time and decision quality
- Enhancing overall SOC efficiency through smarter alert handling
- Making cybersecurity more accessible to non-expert teams
- Boosting ROI by eliminating process inefficiencies
Organizations that choose AI-enhanced SOCs will be better equipped to combat modern threats.
Conclusion
Security Operations Center should be, must be a part of the organizations looking to prevent breaches, reduce damage, meet compliance requirements and build continuous trust with customers. Modern enterprises need modern, upgraded and AI SOC, blending skilled people, smart processes, advanced tools and AI-driven insights to protect what you have built.
We offer the right mix of AI technology, certified experts and advanced processes to build a Security Operations Center that can fortify your business in the digital-first world. Contact us today to learn about our SOC engagement models, AI Managed SOC as a Service and more.
Security Operations Center FAQs
How does a SOC differ from a NOC (Network Operations Center)?
While both a SOC and NOC monitor IT infrastructure, their goals are very different. A SOC focuses on cybersecurity — identifying, analysing, and responding to threats like malware, phishing, or data breaches. A NOC ensures performance and uptime, managing servers, networks, and IT systems. In essence, the NOC keeps your systems running smoothly, while the SOC keeps them secure.
What kind of data does a Security Operations Center monitor to detect threats?
A SOC monitors a wide range of data sources including firewall logs, endpoint activity, authentication records, cloud traffic, email metadata, DNS requests, and application logs. By correlating this information, the SOC can uncover patterns, spot anomalies, and identify suspicious behaviour across the entire digital environment.
Can small and medium businesses benefit from SOC services?
Absolutely. In fact, SMBs are increasingly targeted by cybercriminals due to weaker defences. Modern SOC models like virtual SOCs or managed SOC-as-a-service options offer enterprise-grade protection at a fraction of the cost. These solutions allow SMBs to detect threats early, maintain compliance, and respond to incidents without hiring a large security team.
How long does it typically take to set up a Security Operations Center?
The timeline depends on the model. An in-house SOC can take 6 to 12 months to fully build, requiring planning, hiring, and tool integration. In contrast, a managed or virtual SOC can be operational in a few weeks, offering faster time-to-value. Organizations should also factor in time for tuning detection rules, training analysts, and testing incident response processes.