It is impossible to imagine a business function today without mobiles, laptops and desktops. Modern enterprises also use servers, Internet of Things (IoT) devices and safety cameras that share data across digital systems.
All these devices are known as endpoints that connect to a company network. Any one of these devices, if left unprotected, can act as an entry point for cyber attackers.
That’s why endpoint detection and response is critical to securing your entire network. Plus, it protects your organisation from barrage of modern threats like ransomware, zero-day exploits, fileless malware and insider attacks that can no more be prevented by signature-based defences like antivirus.
What is Endpoint Detection and Response (EDR)?
Endpoint Detection and Response is a cybersecurity technology or solution that continuously observes and records activities and events across endpoints to detect threats and orchestrate appropriate responses.
It involves gathering data from processes, user actions, file modifications, registry entries and network activity. It uses advanced analytics and behaviour detection techniques to identify suspicious patterns or anomalous actions. Once a threat like ransomware or malware is found, EDR either alerts security teams or take rapid response measures, followed by threat hunting, forensic investigation and continuous learning.
Why is EDR in Cybersecurity Important?
Cyberattacks do not occur on a single day or in a single step. With enough motivation and resources, meticulous planning is done. Various techniques such as phishing or credential compromise are used followed by lateral movement, privilege escalation, data collection and finally, exfiltration or encryption inside your system.
While conventional security tools fail to detect this slow-burning exercise, EDR excels at recording and recognizing even the most subtle markers or suspicious behaviour that precedes a major breach.
This is why endpoint detection and response is important because of its ability to catch stealthy intrusions. Additionally, it boosts response capabilities by containing, investigating and recovering from attacks before they could escalate into a full-blown security incident. This proactive model helps organizations reduce attacker dwell time and minimize damage.
Endpoint Detection and Response (EDR) vs Antivirus and EPP
Antivirus recognises and neutralises known threats, and therefore it is reactive. Endpoint Protection Platforms (EPP) built on antivirus as foundation, add monitoring agents across endpoints and puts in place preventive measures like device control, encryption and app whitelisting.
EDR works at a macro level. It goes beyond stopping known threats and focuses on the unknown. Continuous monitoring for outliers, investigating root causes and rapid recovery actions makes EDR a detection and response tool, as its name aptly implies.
As you can see, legacy tools wait for signatures or basic anomalies to trigger alerts. Endpoint Detection and Response (EDR), on the other hand, monitors, records, correlates and responds to suspicious behaviours across every device in your network.
What is an Example of Endpoint Detection and Response (EDR)?
Here is an example that explains the importance of endpoint detection and response in your business security strategy:
Imagine one of your employees unknowingly clicks on a phishing email link and installs a remote access tool. In this case, no malware is involved. Only a disguised command-line operation. Antivirus programs might overlook this completely.
EDR tools, however, would pinpoint the unusual use of PowerShell, detect lateral network probing and correlate these suspicious behaviours with threat intelligence to generate an alert. It would automatically isolate the compromised machine, preserve evidence and notify the SOC for investigation.
As you can see, the real-time visibility and context-aware response sets EDR tools apart.
Related Content: Top 10 EDR Tools in 2025: Choosing the Right Endpoint Defender
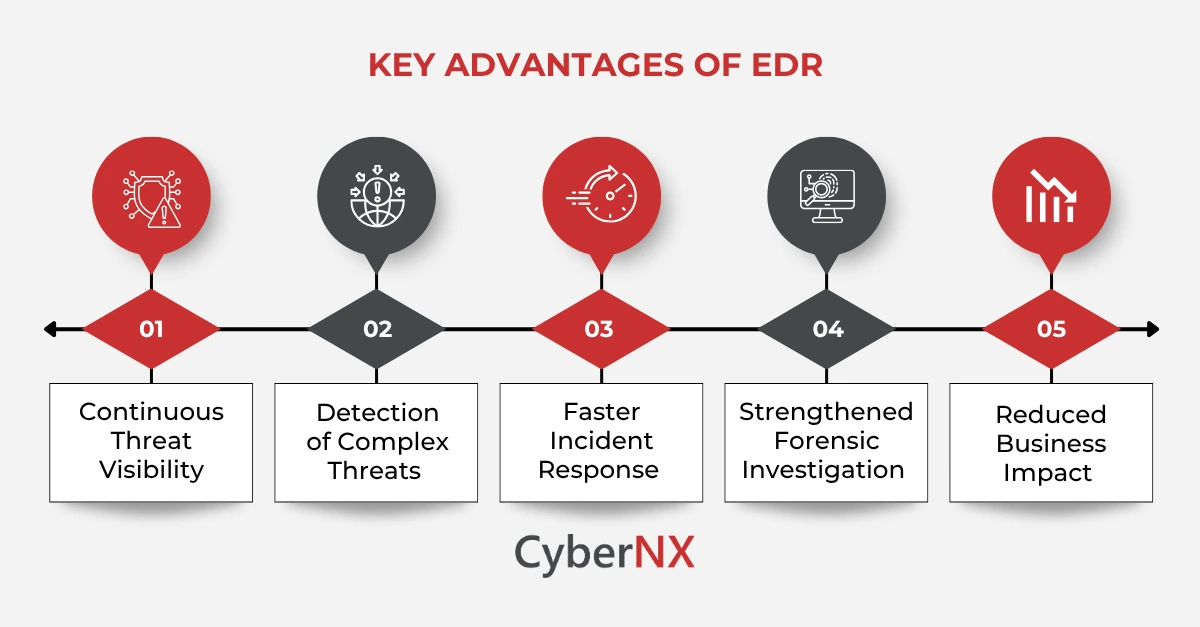
Benefits of EDR
If you are looking to strengthen the security posture of your organization, EDR offers plenty of benefits.
1. Continuous Threat Visibility
EDR provides complete visibility into everything that’s happening at endpoints. This means every user action, file modification and network request in your digital ecosystem is recorded. This telemetry empowers security teams to observe threat actor behaviour, reconstruct attack timelines, understand impact and identify weaknesses with utmost clarity.
2. Detection of Complex Threats
Modern attacks with sufficient time bypass signature-based tools. To combat this, Endpoint Detection and Response tools use behavioural analytics and machine learning to spot anomalies that suggest malicious activity from miles afar, making detection of complex threats easy.
3. Faster Incident Response
That’s the differentiator for EDR platforms. It equips security teams with precise data and advanced tools to take swift action in a quick time. It enables organizations to isolate a device, terminate a process or reverse malicious changes, bringing the system from the infected to previously normal state.
4. Strengthened Forensic Investigation
As discussed before, EDR records granular endpoint data. How does it help? It acts as a key intelligence for post-incident analysis. Security teams are able to trace actions from the source, identify compromised accounts and understand how threats evolved and gained foothold.
5. Reduced Business Impact
With early detection and immediate containment, EDR helps organizations avoid costly downtime, reputational damage and regulatory fines that often follow major breaches.
How Does EDR Work?
EDR solutions may work differently, depending on the vendor you choose. However, here is a broader, generalized method in which most of them work:
1. Monitoring and Data Collection
EDR is all about continuous surveillance or vigilance. Monitoring agents are deployed on endpoints to collect data on everything, from process executions and file changes to network connections and user behaviour. This data acts as the raw material for analysis.
2. Analysis and Threat Detection
Once data is collected, the telemetry is analysed using heuristics, anomaly detection and threat intelligence. ML models identify any and every unusual activity patterns that may emerge and indicate a breach. They include credential misuse, lateral movement or attempts to disable security controls.
3. Alerting and Investigation
As soon as potential threats are identified, the system generates detailed alerts, incorporating contextual information that helps EDR analysts assess severity and scope. The investigation tools allow security teams to visualize the entire attack chain.
4. Response and Remediation
EDR platforms offer both automated and human-led, expert response capabilities. These may include quarantining infected endpoints, stopping malicious processes, deleting files and initiating forensic snapshots for legal or audit purposes.
Other Key Functions of EDR
Other EDR functions that help security teams are discussed below:
- Builds profiles of normal behaviour and detect deviations like suspicious command-line usage, privilege escalation attempts and patterns consistent with ransomware or APTs.
- Isolates infected components from the network in case of breach or compromise and neutralizes the malicious process.
- Bings back system to a pre-infection state. This is possible due to the recording or journaling capabilities of EDR.
- Offers query-based interfaces. It allows analysts to search for indicators of compromise (IOC), unknown threats and abnormal activity.
- Retains historical data about an incident that happened in the past. It helps in forensic investigations, incident reconstructions and compliance reporting.
- Advanced EDR technology connects easily with SIEM, SOAR and other platforms, helping threat signals to be shared and right responses to be orchestrated.
Things to Consider While Choosing an EDR Solution
Finding Endpoint Detection and Response that provides comprehensive protection is crucial. Plus, EDR solution should offer solid support to your security teams.
Scalability and Coverage
It is important to choose EDR technology that covers the entire digital ecosystem, from remote employees and hybrid cloud workloads to mobile phones and IoT devices. That’s the demand of modern organizations. The solution should also scale without any drop in performance.
Quality of Detection
False positives are just wastage of time. EDR platforms should offer high signal-to-noise ratio, leveraging behavioural analysis and threat intelligence to inform only what matters.
Automation and Response Playbooks
EDR solutions should have built-in response automation that can contain threats before human intervention is needed, improving mean time to resolution (MTTR).
Analyst Experience
Often overlooked aspect of an EDR platform is the interface it offers. The platforms with intuitive dashboards, contextual alerts and visual mapping of attack sequences help analysts get a clear and bigger picture of your security.
Integration Capabilities
EDR tools should plug into the existing tech stack without hiccups. Compatibility with SIEM, cloud platforms and identity providers is critical for smooth operations.
Compliance and Reporting
The endpoint detection and response platform should offer custom reporting and role-based access control. This helps in audits and meeting regulatory requirements.
EDR Implementation Process
EDR implementation process should be carefully carried out to avoid disruptions.
1. Assessing Endpoint Environment
Conducting an in-depth assessment of all devices, operating systems and usage patterns across the network. Thorough understanding of this baseline will help shape the deployment strategy.
2. Selecting the Right Platform
Map technical, operational and regulatory requirements against available solutions. Consider a proof-of-concept phase to validate detection accuracy and performance.
3. Agent Deployment
Initially, install lightweight agents across endpoints, testing if they function properly and without affecting system performance. You can begin with a pilot group before scaling across organization.
4. Policy Configuration
Define alert thresholds, response actions and logging preferences tailored to the organization’s risk appetite. Pre-configured playbooks help automate reactions to common threats.
5. Staff Training and Simulation
Train the team on alert handling, investigation techniques and response workflows. Conduct mock attack drills to test readiness and refine processes.
6. Continuous Tuning and Review
Refine detection rules, monitor false positives and adapt configurations as your environment evolves.
Common Challenges and Solutions While Adopting EDR
Adopting EDR can create possible roadblocks. Understanding them and implementing solutions for the same can help organizations maximize benefits.
- False Positives and Alert Noise: Alert fatigue happens due to poorly tuned detection thresholds, and this eventually leads to critical signals being missed. To counter this, EDR platforms must be fine-tuned regularly and enriched with relevant threat intelligence.
- Resource Constraints and Skill Gaps: Organizations may not have a mature SOC or experienced analysts. Here, managed services like Managed Detection and Response (MDR) integration or EDR platforms with built-in automation and guided workflows can help.
- Performance Impact on Endpoints: Extensive telemetry collection may slow devices, especially older systems. Select agents optimized for lightweight performance and conduct phased rollouts with endpoint resource monitoring.
- Integration Complexity: Integrating EDR into your security stack can be complex. Prioritizing tools with open APIs, native connectors and pre-built integrations that simplify onboarding and orchestration can help.
- Change Management and Cultural Resistance: End users often resist security tools or for that matter, anything new. Clear communication, executive buy-in and visible outcomes from EDR deployment help build trust and encourage adoption.
EDR vs MDR vs XDR
What about the other detection and response tools? How do they compare with EDR? You might want to know the answers to these questions. EDR, as we have been discussing, focuses on endpoint-specific visibility and response whereas MDR, which stands for Managed Detection and Response, is totally different. It is a managed service offering detection and response expertise on behalf of organizations.
XDR or Extended Detection and Response is an extension of EDR. It broadens the scope, covering endpoints, cloud, network and identity systems into a unified threat detection platform.
Know in-depth about the differences between these detection and response technologies in our blog: EDR vs XDR.
Also read our guide on EDR vs MDR vs XDR for complete overview of endpoint security solutions and services available.
Conclusion
Cyber threats have become evasive in nature today. Endpoint Detection and Response helps by gaining situational awareness, speed and control required to stop a breach before they spiral into a business crisis. Additionally, EDR solutions outpace attackers, reduce risks and stay resilient in the expanding digital ecosystem.
Endpoint Detection and Response FAQs
Can EDR protect against ransomware attacks, and how effective is it?
Yes, Endpoint Detection and Response is highly effective against ransomware, especially when combined with behavioural detection and rollback features. Unlike traditional antivirus, EDR can identify the unusual file encryption behaviour ransomware exhibits, isolate the endpoint to prevent lateral spread, and in some solutions, automatically revert systems to a pre-attack state. This rapid detection and response significantly limit ransomware damage.
Is Endpoint Detection and Response suitable for small and medium-sized businesses (SMBs)?
Absolutely. While Endpoint Detection and Response (EDR) started as an enterprise-focused solution, many providers now offer lightweight, cost-effective versions tailored for SMBs. These solutions often include simplified dashboards, pre-configured response playbooks, and managed services—allowing SMBs to achieve enterprise-grade protection without needing a large security team.
How does EDR support compliance with data protection regulations like GDPR or HIPAA?
EDR tools help meet regulatory requirements by offering audit logs, endpoint activity records, and incident response documentation. They provide visibility into unauthorized access, data movement, and policy violations. When a breach occurs, Endpoint Detection and Response can assist with investigation, containment, reporting, and remediation—core components of compliance frameworks like GDPR, HIPAA, PCI-DSS, and ISO 27001.
What’s the difference between agent-based and agentless EDR solutions?
Agent-based EDR solutions install lightweight software on each endpoint to gather telemetry in real time. Agentless EDRs, often used in cloud environments, access endpoints via APIs without direct software installation. While agent-based systems offer deeper visibility and control, agentless models may suit environments with limited device access or where agent deployment is impractical. Many modern endpoint detection and response platforms offer hybrid models combining both.