This blog takes a deep dive into the two commonly used methodologies: Black Box vs White Box Penetration Testing.
Our experts have helped hundreds of CISOs and CEOs understand the fundamental differences between the two.
Read to find out the advantages, disadvantages, key parameters that differentiate the two approaches and decide which method best supports your compliance posture and security strategy.
Black Box Vs White Box Penetration Testing
What is Black Box Penetration Testing?
Here’s the definition of black box penetration testing: it simulates an external attacker with no prior knowledge of internal architecture, code or logic of your business systems.
The pentesters act like a real-world hacker using full force to breach your environment. For this, publicly accessible information or what could be gathered through reconnaissance are used.
Key use cases of this pentesting approach include assessment of perimeter defences, web-facing applications and how your organisation appears to a real-world hacker.
What is White Box Penetration Testing?
White box penetration testing, also known as clear-box or transparent testing, gives pentesters full access to the systems. It includes source code, architecture diagrams, API documentation, credentials and infrastructure details.
The goal here is to uncover deep-rooted vulnerabilities that might remain hidden otherwise.
Key use cases of this pentesting approach are critical business system auditing, secure application development and achieving compliance and regulatory standards.
Done with definitions, find out advantages and disadvantages of both penetration testing approaches.
Black Box vs White Box Penetration Testing: Advantages and Disadvantages
Black Box Pentesting: Advantages
- Realistic threat-simulations Mimics all the techniques and methodology used by an external attacker. It is as real as it can get. So, it provides insight into real-world exploitability of your assets.
- No Insider Bias As pentesters come with no assumptions, it provides a clear, objective perspective about your existing environment.
- Exploitable Entry Points Login portals, network interfaces and APIs – all publicly exposed surfaces are assessed.
Black Box Pentesting: Disadvantages
- Limited Visibility What limitations does is that internal flaws in the system such as insecure code logic or misconfigured roles remain unseen.
- Time-intensive Discovery Excessive effort must be put to gather intelligence in the reconnaissance phase.
- Missing Deep Vulnerabilities Since this approach focuses on observable behaviour, business logic errors and insider threats may be missed.
White Box Pentesting: Advantages
- Complete Assessment Complete system visibility helps in auditing the source code, configurations and backend services.
- Efficient Exploitation With proper access, more time is spent exploiting and validating vulnerabilities instead of finding them.
- Secure Development Lifecycle Fixes flaws early in the development process, reducing cost of patching in the production stage.
- Compliance Ready Best for meeting internal and external audit requirements.
White Box Pentesting: Disadvantages
- Skilled Expertise Advanced knowledge of code analysis, system architecture and security principles are required. Companies are sometimes unable to find such skilled experts.
- Possible Bias Pentesters might sometimes overlook security issues due to familiarity with the system or access to excess information.
- Misaligned with real-world attacks Does not simulate how a real-world attacker would approach a breach, which is a clear disadvantage.
Key Differences: Black Box vs. White Box Penetration Testing
| Parameter | Black Box Penetration Testing | White Box Penetration Testing | Business Impact |
|---|---|---|---|
| 1. System Knowledge and Access | No prior knowledge; external perspective. | Full access to source code, infrastructure, credentials. | White box enables deep vulnerability detection; black box simulates real attacker scenarios. |
| 2. Attack Simulation Fidelity | Emulates an outside hacker with no inside access. | Models insider threats or developer errors. | Black box is ideal for external threat validation; white box supports compliance and internal audit. |
| 3. Vulnerability Coverage | Surface-level flaws like open ports, weak login. | Deep issues like logic flaws, hardcoded secrets, insecure APIs. | White box provides deeper, broader coverage across app and infrastructure layers. |
| 4. Toolsets and Techniques | Nmap, Nessus, Burp Suite, social engineering, fuzzing. | SAST, manual code review, SonarQube, architecture validation. | White box uses analytical tools; black box relies on hacker-like simulation tools. |
| 5. Testing Time and Complexity | Slower due to reconnaissance and limited info. | Faster if systems are well-documented, but can be complex. | White box is efficient for in-depth audits; black box for stealth-based attack simulation. |
| 6. Security Posture Insights | Identifies external entry points and attack vectors. | Reveals internal design flaws and systemic issues. | Black box gives strategic risk visibility; white box delivers tactical precision. |
| 7. Cost Implications | Lower initial cost; less resource intensive. | Higher initial cost; requires deeper expertise and collaboration. | White box may have better ROI when used early in SDLC or for compliance. |
| 8. Compliance & Risk Management | Demonstrates threat exposure to external stakeholders. | Provides detailed, audit-ready reports for frameworks like PCI, SOC 2, ISO. | White box supports regulatory readiness; black box supports risk exposure storytelling. |
| 9. Team Involvement | Minimal involvement from internal teams. | Requires developer, IT, and security team collaboration. | White box promotes DevSecOps and cross-functional security culture. |
| 10. Business Fit / Scenarios | Best for SaaS platforms, web apps, and perimeter defence. | Best for critical infrastructure, proprietary apps, and regulated sectors. | Choose based on system sensitivity, exposure, and compliance needs. |
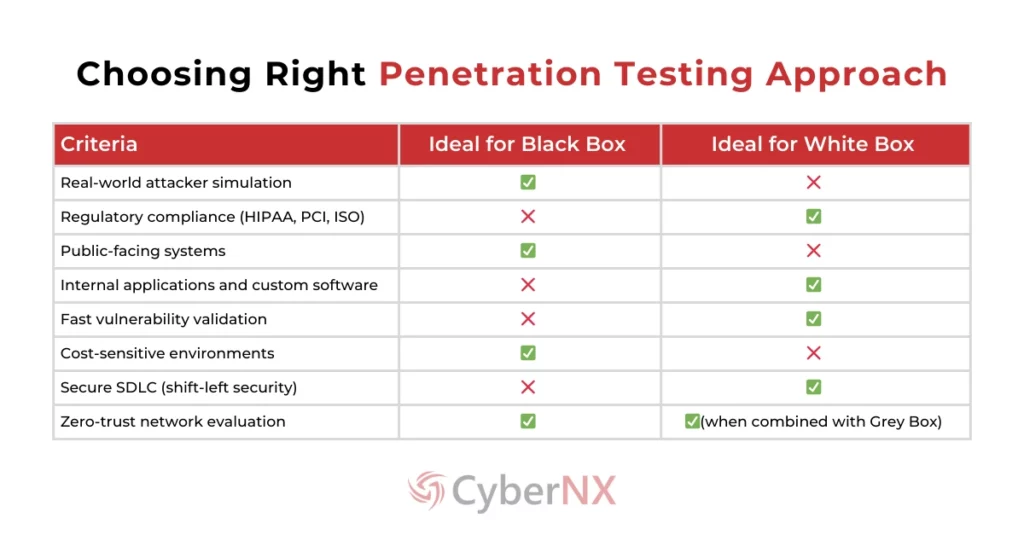
How to Choose the Right Penetration Testing Approach?
That’s the question we are trying to address here. Find the answer in an easy-to-understand manner in the table below:
What About Grey Box Penetration Testing? The Middle Ground
Grey box penetration testing combines aspects of both black box and white box approaches. Testers are given limited internal knowledge, such as credentials or architecture overviews, while maintaining an outsider’s perspective. In short, this hybrid method provides a balanced assessment.
Conclusion
In the Black box vs White box penetration testing debate, it is important to understand that both serve distinct, complementary purposes, depending on the needs of the organisation.
They are not interchangeable. Instead, they are used to address distinct aspects of security posture.
The key is to align the penetration testing type with your business goals, regulatory mandates and risk appetite.
CyberNX is a premier penetration testing service provider offering both black and white box penetration testing approaches. Our experts first understand your risks, unique threat model and recommend the best approach based on your business context.
To know more about our services, talk to our experts.
FAQs
Can I use both black box and white box testing together?
Yes. Many organizations adopt a hybrid or grey box approach to combine the realism of black box with the depth of white box, offering a balanced and comprehensive security assessment.
Which is better for early-stage product development—black box or white box?
White box is more suitable during early development as it helps identify code-level and architectural flaws before deployment, reducing long-term security risks and remediation costs.
How often should each type of testing be conducted?
Black box testing is typically done annually or after major updates to public-facing systems. White box testing should be integrated into the SDLC and performed continuously or quarterly for critical applications.
Does white box testing expose more security gaps than black box?
Yes, in most cases. Because white box testers have full visibility into the system, they can uncover logic errors, insecure APIs, and hidden vulnerabilities that black box testing might miss due to limited access.