24/7 Managed Detection and Response (MDR) Services
Our AI-enabled Managed Detection and Response (MDR) services offers continuous, round-the-clock cyber threat detection, investigation, and response services.
INTRODUCTION
Your Reliable MDR Partner: CyberNX
Cyber threats are constantly evolving, and today’s adversaries are one step ahead, taking advantage of cyber security weaknesses and loopholes to affect the company. Are the present monitoring systems capable of doing sophisticated analytics and detection needed to identify and successfully tackle the contemporary cybersecurity threats? Are the challenges we see today due to rapid adoption of technology and digital infrastructure addressable?
We address your key challenges:
PROCESS
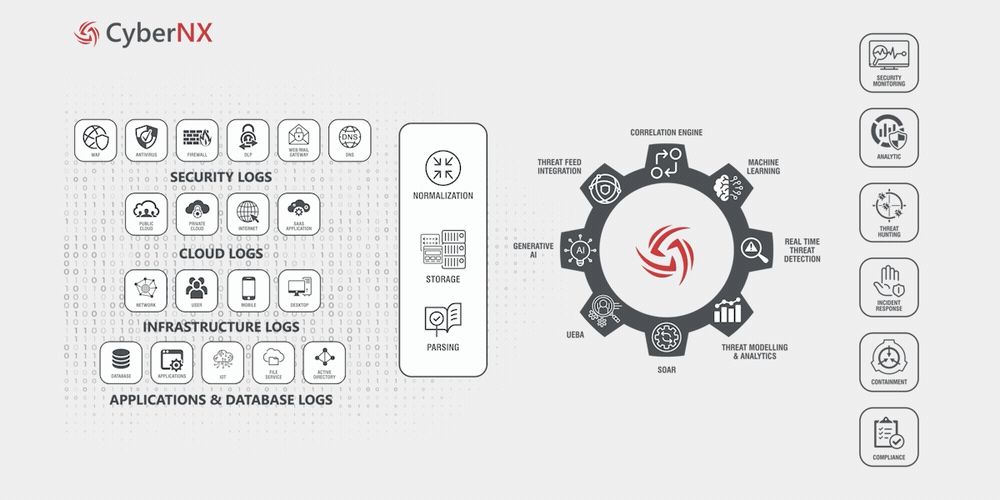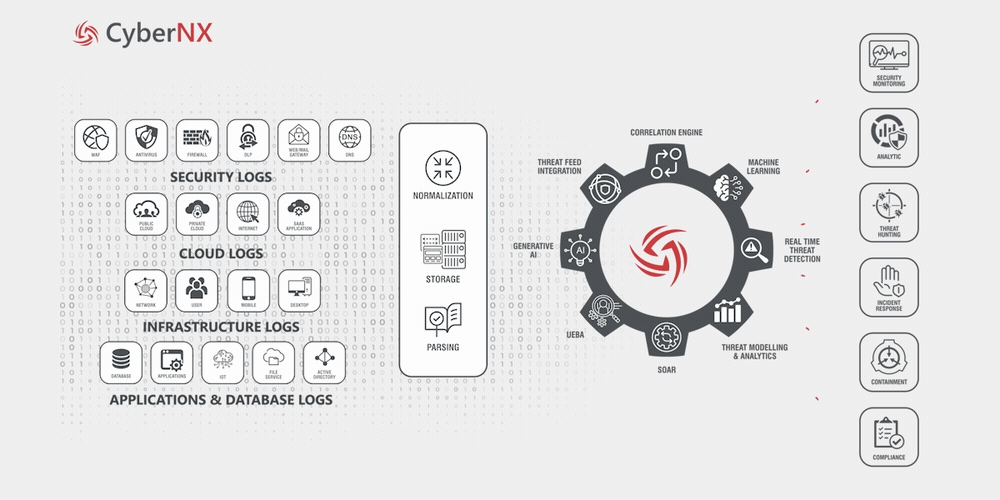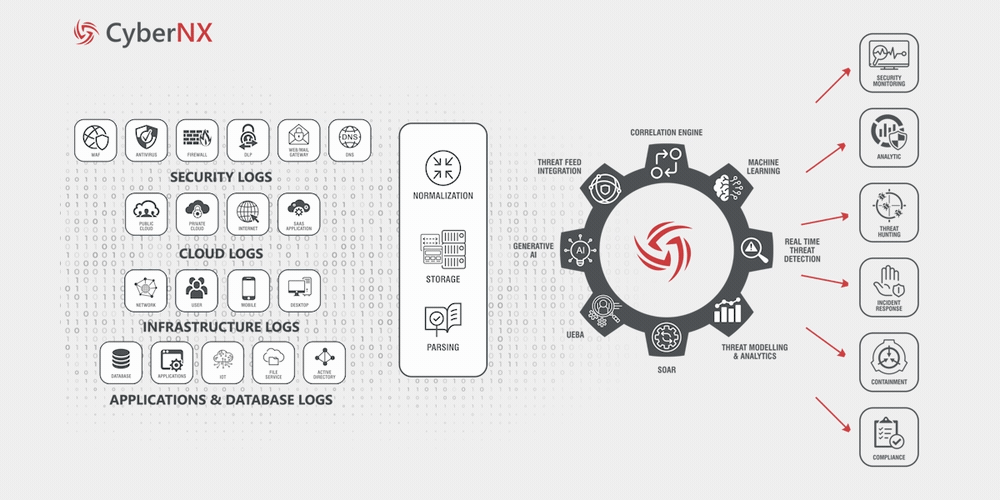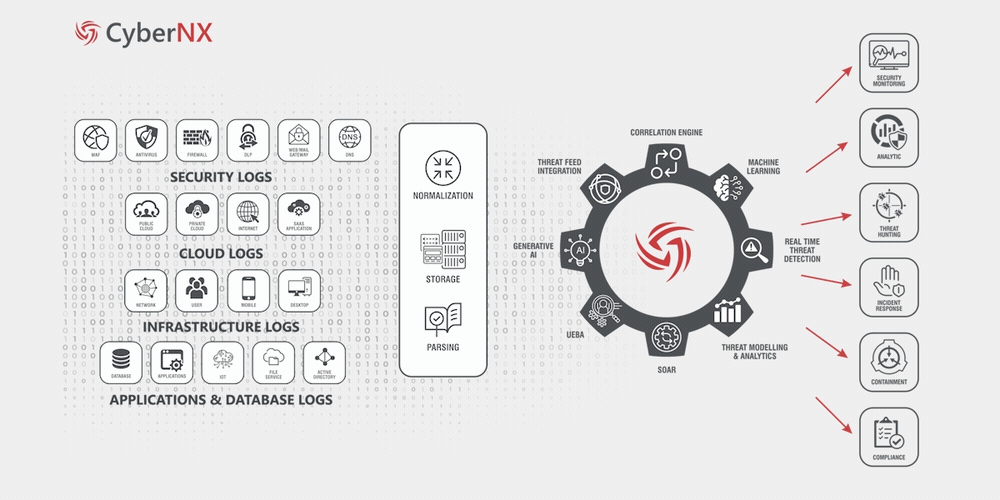
How It Works?
Looking for MDR Services? Connect with Our Cybersecurity Experts!
APPROACH
What Makes CyberNX Your MDR Partner of Choice?
Threat modeling
Log Assessment
Use Case Customization
Dedicated Threat Hunting
Customized Reporting
Functional SME Team
Platform engineering, integrations, threat intel, R&D, analysis, threat hunting, and incident response – all part of the Functional SME Team.
Customer first Approach is our guiding principle.
BENEFITS
Maximizing Threat Visibility with Best MDR Services
Expertise That Matters
Our cybersecurity team comprises seasoned professionals adept in threat detection, incident response, and vulnerability management.
Modern Technology
To offer unmatched visibility into possible risks, we make use of cutting-edge techniques, machine learning, generative AI, and global threat information.
Rapid Incident Response
To maintain operational continuity, security issues must be addressed quickly to reduce impact and downtime.
Managing Costs
By allocating resources more efficiently, outsourcing security services can be less expensive than keeping an internal staff.
Increased Visibility
Acquire thorough knowledge of your security posture, risks, and vulnerabilities to help you make well-informed decisions for more robust defences.
Peace of Mind
You may confidently concentrate on your primary business operations knowing that your organization's security is in good hands.
Choose A Plan For MDR Services
Plans for all business |
Bronze For Start-upsSelect Plan |
Silver For MSMEsSelect Plan |
Gold For Mid-size EnterprisesSelect Plan |
Platinum For Large EnterprisesSelect Plan |
24 X 7 Security Monitoring |
||||
Log collection and Aggregation |
|
|
|
|
Log retention |
15 Days |
20 Days |
30 Days |
30 Days |
Correlation of Logs |
|
|
|
|
Machine Learning Detections |
|
|
|
|
Custom Dashboards |
|
|
|
|
Cloud Security Posture Monitoring (CSPM) |
|
|
|
|
Cloud Vulnerability Management (CNVM) |
|
|
|
|
Weekly Threat Hunting Reports |
|
|
|
|
Commercial Threat Intelligence |
|
|
|
|
Brand Reputation Monitoring (BRM) |
|
|
|
|
Automated Reports |
Monthly |
Monthly |
Daily and Weekly |
Daily and Weekly |
Governance Calls |
|
Qaurterly |
Monthly |
Weekly |
Long term log retention |
Optional |
Optional |
Optional |
Optional |
For Customized Plans tailored to Your Needs,
Get in Touch Today!
FAQ
Frequently Asked Questions
Managed Detection and Response (MDR) is a comprehensive security service that combines advanced technology and human expertise to detect, investigate, and respond to cyber threats in real time. It provides continuous monitoring, threat hunting, and incident response to ensure your organization’s security.
MDR services are essential for organizations to stay ahead of evolving cyber threats. They provide enhanced visibility into your security landscape, reduce the time to detect and respond to threats, and help ensure compliance with regulatory requirements. MDR services also fill the gap caused by the shortage of skilled cybersecurity professionals.
CyberNX provides your organization with top MDR solutions consisting of a team of experts who monitor your endpoints, networks and cloud environments and respond to cyberthreats 24/7.
- 24/7 Monitoring and Detection: Continuous surveillance of your IT environment to identify and respond to threats in real time.
- Threat Hunting: Proactive search for threats that might evade automated detection systems.
- Incident Response: Rapid response to security incidents to mitigate impact and reduce recovery time.
- Advanced Analytics: Use of machine learning and AI to enhance threat detection and analysis.
- Compliance Support: Ensuring adherence to industry regulations and standards.
RESOURCES

